https://modernconsensus.com/technology/building-digital-dollar-requires-private-sectors-help-fed-chairman/
Clearly, I am a bit behind.
Category: Payments
Philip in the News
Identity in the Digital World
The Means of Payment And the Method of Payment
Two words each can be seen as the same as the other. Yet, it is important to create a distinction.
The method of payment should be related to how we execute and not from where the money comes. The means of payment should relate to the source of funds.
Too often, we allow these terms to get lost. Is tapping a payment card at the point of sale or typing in the 16 digits printed or embossed on the card a means of payment? I would argue not! This is the method we use to inform the merchant how they will be paid for the goods and services we seek to procure.
When we talk about the means of payment, we should focus on the source of funds. Are these funds held on deposit, funds in the wallet, or a loan of funds?
Our vocabulary is rich in confusion. These two words in the complex space of payments need to have independents reason.
As an example, I use Apple Pay to pay does not mean Apple is involved in managing the funds. It is simply the method used to share the payment card details with the merchant, enabling the merchant to request funds from the account selected by the user through the Apple Pay user interface.
The Card Was and Is Only a Credential Carrier
Cash is here to stay – cards are the true dinosaurs
This question of the extinction of the payment card is misleading.
What is a payment card? It is the carrier of a set of credentials, A means of Identification offering financial Attributes capable of being authenticated by a party seeking to sell something to the individual or entity presenting the credential as a mechanism to assure payment.
Back when credit cards were designed, the goal was to offer merchants a guarantee of payment and anonymous consumers a means of paying. Behind this means of payment, a financial institution, the issuer, provides the consumer with a “Line of Credit”.
On the merchant side, another financial institution buys these guaranteed receivables from the merchant and charges the merchant a “merchant discount”. Later that day the Issuing Institution advances payment to the Acquiring Institution based on an agreed set of terms and operating rules. Terms and conditions the involved financial institutions collectively agreed upon.
For this method of payment to be effective, a large number of consumers and merchants had to agree to participate; hence the financial institutions came together and formed what we now know as MasterCard and Visa.
Given the state of technology at the time it was essential this new mechanism work without the burden and expense associated with the merchant, supported by the acquirer, contacting the issuer to receive approval, or, in stronger terms be assured of a guarantee of payment. To achieve this result, the merchant needed something to acquire the necessary information to submit a request for payment. For both the merchants and financial institutions,, there had to be a means of authentication. Designed to assure the responsible parties of the authenticity of the person or entity to present their payment credentials.
 To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
Overtime criminals successfully counterfeited these security features.
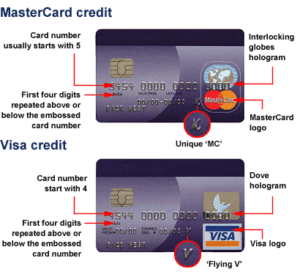
As these features were compromised additional features had to be added.
Today, a computer has been embedded inside the card, in order to assure the authenticity of the payment card credentials being presented to the merchant.
These computers embedded onto the front of a payment card exploit the power of cryptography. Cryptographic certificates and digital signatures are created by and for these computers, allowing:
-
- The Issuer (symmetric cryptography) to support Online Authentication
- The merchant (asymmetric cryptography) to support Offline Data Authentication
These two mechanisms prove to the merchant and issuer that the card is unique and the data, credentials, and digital signature it contains or produces are authentic.
Once all the merchants have are capable of reading the data from the chip card, the security features of the card become redundant.
As these features become redundant and the merchants embrace Near Field Communications, based on the ISO 14443 standard, the issuer can replace the card form factor with anything equipped with the necessary computational capabilities and ability to communicate with the terminal over the NFC interface.
This is exactly what Apple Pay and Google Pay have done. They replaced the card with a device. Yes, the Payment Card may become redundant. But, the Payment Credentials they contain, remain.
What we know as card payments, is fundamentally an account-based solution. Money, through the defined settlement process, ultimately move from the line of credit or deposit account of the buyer, through a series of accounts with the participating financial institutions, to the account of the merchant.
Card-based credential payments
simply become
Device-based credential payments
EMVCo Good or Evil
https://www.securepaymentspartnership.com/wp-content/uploads/2019/12/Payment_Insecurity_Final.pdf
In 1993, I was asked by the then CEO of Europay International to establish a relationship with Mastercard, and Visa focused on developing the specifications necessary to assure the interoperability of chip card-based security for credit and debit payment cards. The result published in 1996 was the “EMV Integrated Circuit Card Specifications for Payment Systems.”
From these humble beginnings, EMVCo has emerged as a key organization in managing the standards behind card payment systems. In the white paper Payment Insecurity, commissioned by the Secure Payment Partnership, the author reminds us of the difference between standards managed by an open body and those tightly controlled by an exclusive group of competitors. One wonders if the owners of EMVCo will listen and strive to open up their membership or continue to use this entity to protect their proprietary interests.
In the introduction, the author speaks of a series of questions he intends to address. The first question of the paper
Is EMVCo furthering the entire U.S. payments industry or simply protecting Visa and Mastercard’s market share? page 5
begs the question, why limit the discussion to the USA?
This American only focus is driven by the desires of the Unaffiliated Debit Networks and a set of merchants. The paper ignores fundamental and, yes, anti-competitive elements of the EMV specification – the AID or the Application Identifier. It was and is directly related to the Brand responsible for the underlining technology incorporated into the Chip.
I then read the following complaint and am driven to ask how the consumer interpreted the prior Debit versus Credit prompts.
Visa’s response to this solution was to require merchants to display to consumers a choice between “Visa Debit” and “U.S.
Debit” at checkout. – page 13
In essence, what Visa required was simple, the terminal should comply with the EMV specification for “application selection,” key and inherent in the multi-application design of EMV and the underlining ISO 7816.
Moving further into the document in Section 6.1, the author attempts to document the history leading to the creation of EMVCo. As one of the founding members, the author’s sources were not involved and did not understand the history.
First, only France had a smart card solution designed to address Credit and Debit card fraud. They referred to their implementation as B Zero Prime.
Second, the UK in 1995 was driven by Visa to embrace an earlier version of the Visa specifications adapted to the unique requirements of the UK market and branded UKIS. UKIS and the unique UK requirements are responsible for changing many of the shall’s in the EMV 2.0 version of the specifications to should’s in the EMV 3.0 version. This accommodation was the result of legacy limitation within the X25 network the United Kingdom depended on for card authorizations.
To further identify issues with his record of history, the statement on page 22
EMVCo developed standards for chip cards that could work with credit, debit and stored-value cards
It is fair to suggest EMV attempted to incorporate Stored-Value cards in the specification. But as a result of the competitive realities of Europay’s Clip, Mastercard’s Mondex, and Visa Visa Cash stored value solutions, they agreed to exclude stored value cards from the specifications.
It then goes on to suggest EMV compromised and offered a Signature option. There was not a compromise; it was intentional. The goal, afford the Issuer the ability to determine, by Cardholder, which cardholder verification method they could be configured for. One need was to address issues of the disabled, e.g., the Blind.
Debit Routing as a result of the Durbin amendment. One might wonder why EMV did not consider this idea of multiple networks associated with a card.
EMVCo was unable and unwilling to resolve the lack of a debit AID because EMV was never designed for the U.S. market.
I sense that there is another front coming out of the Debit Networks seeking to argue the anti-competitive nature of EMV. The paper, link below, draws me to wonder about the argumentation surrounding “Application Selection.” Please let’s get back to basics – the “AID=Brand=Payment Scheme” drives “Routing.”
On page 13, it argues consumer confusion. I would argue it ignores the past. The EMV default user prompts of “Visa Debit” and “US Debit” are no more confusing than the historic “Credit,” and “Debit” prompts. I would argue consumer confusion already existed. The EMV specification for Application Selection simply afforded the Issuer the ability to provide more descriptive prompts by employing the “Application Preferred Name” instead of the default “Application Label.”
This whole fight surrounding EMV and Payment Security is really a fight about the future of Card Payments. On one face, they argue the Payment Networks did not assure the security of the card payments to protect revenue. On the other hand, they argue EMVCo is a closed standards organization designed to protect and assure the interests of its shareholders, without consideration for the other stakeholders in the payment, e.g., the merchant.
In the end, the argument comes down to the role, definition, and control. How we structure the underlining payment transaction is what we need to talk about. Who provides the mechanism, guarantee, and support for a particular mechanism decides the rules.
The Surveillance State Exists for Profit
I hope we all understand the data collected on each of us
https://www.nytimes.com/interactive/2019/opinion/internet-privacy-project.html
https://www.nytimes.com/interactive/2019/12/19/opinion/location-tracking-cell-phone.html
As a technologist, the revelation of what is available did not surprise me. I understood how location can easily be captured from all of the electronic devices I use. Be it the GPS chip, the triangulation of Cell Towers or the IP address of the router I am using to access the Internet. Where I am is easily acquired by any application or server I am employing.
What bothered me is that “We the People” have not pushed our governments to regulate the capture and use of this very personal information and data. What bothers me is that most of the citizens of this country or this world do not take the time to read the terms and conditions or the privacy statements provided to us and so often simply consented to them without a thought. And, if they did read them, most of us would not appreciate the language and therefore the meaning of these legal documents.
The surveillance state is real. Marketing companies, employers and so many others are buying the data and using it to improve their delivery of services, advertisements and so much more.
https://www.linkedin.com/pulse/i-hope-we-all-understand-data-collected-each-us-philip-andreae/
The Identifier should not be the Authenticator
I was asked to look into the value of the EMV Secure Remote Commerce Specifications. In the first section they wrote:
“1.1 Background … While security of payments in the physical terminal environment have improved with the introduction of EMV specifications, there have been no such specifications for the remote commerce environment. …”
This statement caused a bit of angst. It caused me to think of the work to create SET and Visa’s efforts to promote the original version of 3D-Secure. I was further reminded of how difficult it has been to find the balance between convenience and fraud and how merchants are more worried about abandonment than they are about the cost of fraud. Ultimately, it caused me to wonder about the goal of the EMV 3-D Secure specification.
“To reflect current and future market requirements, the payments industry recognised the need to create a new 3-D Secure specification that would support app-based authentication and integration with digital wallets, as well as traditional browser-based e-commerce transactions. This led to the development and publication of the EMV® 3-D Secure – Protocol and Core Functions Specification. The specification takes into account these new payment channels and supports the delivery of industry leading security, performance and user experience.”
The keywords found in the last sentence “the delivery of industry leading security, performance and user experience” suggest these two specifications are searching to solve the same problem.
According to the Oxford dictionary
Security is
- “The state of being free from danger or threat.”
- “Procedures followed or measures taken to ensure the security of a state or organization.”
Authentication is
- “The process or action of proving or showing something to be true, genuine, or valid.”
- “Computing The process or action of verifying the identity of a user or process.“
On this same page, the authors go on to make the following statement
“… there is no common specification to address the functional interactions and transmission of data between the participants.”
This then causes me to wonder about the original ISO 8583 specification, the current ISO 20022 specification, and the subsequent concept of the three-domain model within the 3D-Secure specification. All three of these specifications define the interaction between the participants while not restricting the method of transmitting the data. It seems the authors of the SRC specifications have forgotten history. Or, are they trying to rewrite history.
At this stage, Authentication seems to the most important part of what EMV is attempting to address. But, the focus seems to be more about rewriting history that solving the fundamental problem. We seem to have this desire to take public identifiers and convert them into secrets.
“An industry transition from a dependency on Consumer entry of PAN data can be accomplished by providing an SRC specification that meets the needs of all stakeholders involved.”
These intriguing contradictions beg the question. Why did the authors of the Secure Remote Commerce specification not reference the good work of those that created the 3D-Secure specification and propose an approach unlike EMV? They all are part of the same organization!
Is the goal not to address authentication and Security of the payment transactions, be they instore or on the Internet. I would argue
We allowed the PAN, the payment card identifier, to become a means of authentication
This use of the PAN as both an identifier and an authenticator; reminds me of a hearing of the United States House Committee on Ways and Means May 17th, 2018 hearing on “Securing Americans’ Identities: The Future of the Social Security Number”.
“House Ways and Means Social Security Subcommittee Chairman Sam Johnson (R-TX) announced today that the Subcommittee will hold a hearing entitled “Securing Americans’ Identities: The Future of the Social Security Number.” The hearing will focus on the dangers of the use of the Social Security number (SSN) as both an identifier and authenticator, and examine policy considerations and possible solutions to mitigate the consequences of SSN loss or theft.”
All the witnesses and most of our members of congress accepted and understood the problem. We allowed a simple government-issued identifier to become a means of authentication, in other words, an authenticator. Like allowing the social security number and now also the PAN to become part of how we authentic someone’s identity. We caused these publically available identifiers to become valuable and sensitive PII data.
Cardholder Authentication and Consumer Device Identification
What is clear, as one continues reading the SRC specifications, is the goal is to reduce the frequency of presenting payment credentials on merchant websites.
“Minimising the number of times Consumers enter their Payment Data by enabling consistent identification of the Consumer and/or the Consumer Device”
A very different approach to what the payment schemes do with the EMV based payment process. The authors of EMV saw the PAN as public data, they architected something designed to assure the uniqueness of the card and the ability to positively verify cardholder. Card Authentication and Cardholder Verification.
Why not simply think and focus on the same architecture? Simply change the word “card” to “device” and focus on Device Authentication and Cardholder Verification or as everyone is promoting Multi-Factor Authentication. We simply need to make sure the thing is genuine and the right individual is using the thing. The thing is what the cardholder has – The “what you have” factor. Add a pin/password or better still a biometric to be the second factor the “what you know” or “what you are” factor.
EMV 3D-Secure creates the ability to exploit the “what you have” factor by offering Device fingerprint data to the issuer’s authentication process.
Pay to be Paid
An interesting concern and a telling phrase. When one Googles the phrase “Pay to the Paid” the result takes us into the contracts associated with Protection and Indemnity insurance P&I.
When I entered the search term, I was thinking about how financial institutions see ‘payments’ as a revenue source. In particular, the word ‘Interchange’ springs to mind. I remember sitting in a management meeting in Foster City, at the Visa International offices, as we discussed the results of a McKinsey study this study stated the banks were not earning from their most frequent activity – processing payments.
We then as Visa saw a need to help our members appreciate the breadth and complexity of this simple word “Payment”. Payment Zsars and Gurus were all the rage. International Banks spent millions to create payment factories capable of supporting ACH, WIRE, Swift and card payment. Was the goal to streamline the process? For some, yes! For others, the focus was on reducing costs. For others, they focused on creating a sticky proposition capable of assuring long term relationships with their corporate clientele. For all, increase revenue and profit.
Did any actually think to focus on streamlining the mechanical process of moving money between two individuals or entities? Many will argue yes. Why did they not seek to develop Real-time Gross Settlement Systems, RTGS? Why is it only new economies that saw these opportunities?
The answer often comes back to the fear of cannibalizing existing sources of revenue or even worse making a legacy solution redundant.
We Keep Talking About It, When Will We Solve For Identity in the Digital Space
This morning I read an article in the Financial Times The real story behind push payments fraud. What is disturbing, the acceptance of fraud and the focus of bankers on adding fees (like Interchange) to help cover the cost of fraud. This article speaks to Push Payments and how liability shifts from the merchant back to the Issuer and ultimately the consumer. It makes reference to Pull Payments and the use of debit cards where the fraud liability, unless online, is the merchants’.
To address card payment fraud in the physical world the payment schemes developed EMV. In the digital or eCommerce realm everyone accepted allowing the merchants to not attempt to authenticate the cardholder and simply ask the consumer to provide openly available data {cardholder name, PAN the account number, expiry date, and address details}; if they, the merchant, would accept liability for any fraud.
As the world moves to embrace “Faster Payments” and Real-Time Gross Settlement ‘RTGS’, instead of focusing on assuring the identity of the sender and the recipient; we assume fraud will occur.
Why not focus on solving the problem? Solving for Digital Identity solves for Card Not Present fraud, RTGS fraud, Faster Payment fraud, and so much more.
Where are we
Today.
How many passwords are you trying to manage! Does your LinkedIn contact list connecting you to more than 4,000 individuals? Does Facebook, Instagram, and other social media websites inundating you with news and stories about your friends, colleagues and interesting people?
How many cookies have your computers accumulated? How many databases have more information about you than they need? If we search the dark web, how valuable is your data?
Cando seeks to help you manage your data, identity, assets, and relationships.
Philip lives on Sea Island with his 93-year-old father, the Doctor. They pursue travel and Philip keeps his head into what is happening in financial services, blockchain, authentication, digital identity, and, whatever else people seeking to understand the transformation; particularly those in the identity and payments space.
What is happening means we can unlock our hotel rooms, cars, and homes from our phones. Our security system iwill be another app we have to find on our phone.
Instead, we need an intuitive assistant seeking to simplify our lives by taking on repetitive tasks like driving, working inside a data table or simply opening up the house for the season.
Normalizing data and performing the analysis capable of earning value is the name of the game. Management is about stimulating a team to work in the mutual interest of the organization. Executives define the strategy and articulate the vision in a manner conducive to success.
Cando seeks to help you manage your assets and relationships. Assets those places and things you use doing your daily life and those interactions you have with people and entities seeking to serve, sell and partner with you.
Then there are friends who we expect to be part of our lives and therefore have privileges and access capabilities.
All of this with a target of selling integration services to the top million and simply assuring each person has an identity thus serving the bottom billion. ultimately earning $1 per year per user to simply be there when it all breaks and you wish to restore your digital life.
At the core, your digital security will be based on the use of cryptography and sophisticated matching algorithms designed to assure anyone that you are that one individual in the populatations of the universe.
What You possess, What You Are, What You Claim … Your Certificates
NCCOE NIST Multi-Factor Authentication
What you Possess — The Thing
What you Are — You
Your Relationships
Responsibilities
Authority
Advice
— Secrets
My Certificates
World Wide Web Consortium
FIDO Alliance
Global Platform
The Trusted Computing Group
- EMVCo
- ISO
- ANSI
- ABA
Future interests
- Artificial Intelligence
- Machine Learning
- Nature Language Interface
- Predictive Analytics
Review of the IMF The rise of Digital Money
While reading the recent document produced by the IMF I am compelled to wonder.
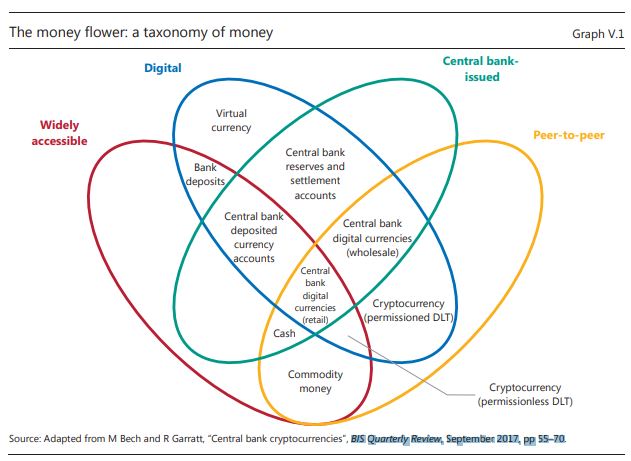
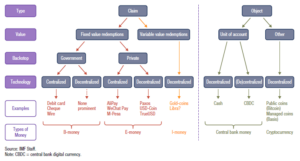
What is the difference between what they call Bank Deposits and e-money. My first question, ignoring the words bank deposit. Both are electronic accounts of value, recorded in someone’s ledger. These two diagrams extracted from a BIS paper offer a perspective.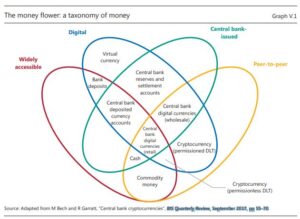
They then speak to four attributed to the “means of payment”
- The Type, be it a claim or an object.
- The value, be it fixed or variable.
- If it is a claim who is liable?
- The technology, be it centralized or decentralized
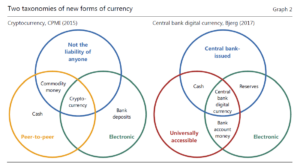
They then speak to the five ‘Means of payment”.
Object-Based
- Central Bank Money (cash)
- Crypto-currency (non-Bank Issued)
As we think of the evolution of these object-based means of payment, we need to reflect on a new term “Central Bank Digital Currency” CBDC.
As a historian, I then wonder where things like Digi-cash and Mondex fit into the classification. The value was originated and then distributed into a personal and secure storage device (Wallet). Redemption or better said the guarantee, was provided by a party. Maybe not a bank or the central bank, yet, easily embraced by such an institution. Somehow history seems to lose sight of the origins of money and assumes the existence of a central bank. Here in the USA, the formation of a Central bank was one of many areas of political discourse.
- b-money (Bank issued)
- e-money (Privately issued)
- i-money (Investment funds)
The magic word behind all of these discussions is “Liquidity”. The bottom line does the receiver of the money appreciate the value of the unit of measure and is the receiver confident they will be able to convert that money into another form, of their preference
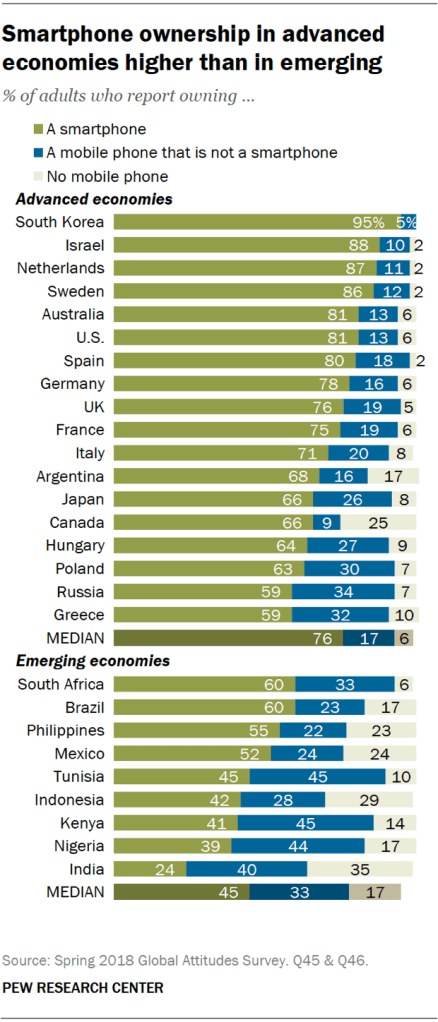
Smart Phone Ownership
Blockchain made simple
Let’s start at the beginning, the transaction, the distributed ledger entry. Think about the content of the transaction as the payload. Next think of the payload as land deed, cryptocurrency value, record of ownership, journal entry, smart contract … marriage contract. Either two or more people seek to exchange and record. Another way to think about all of this is as a block of data, code or other digital representation of something duplicated in every participant’s copy of the current ledger. No matter what happens, a secure system must be established for a smooth cryptocurrency transaction to take place. Maybe look for the best vpn for crypto trading? Could be an option, but only in the later stages when the initial nitty-gritty of the process is established.
A governance model is required
What is essential, before anyone can do anything.
The parties seeking to exploit a distributed ledger must define how it will work.
It is what the community or parties seek to represent and manage, using distributed ledger technology, agree.
The whole process of defining the payload begins when the community agrees to and sets off to publish the processes, procedures, rules, functions, and purpose of their application. It is this act of governance we use to define how and what will be conveyed in the payload to be stored and recorded on a blockchain. Which blockchain, protocol, and cryptographic processes; obviously it is a decision of the community.
We need to be clear before we can do anything with the payload. Ourselves and ultimately others will have initially and subsequently defined the mechanics and processes designed to assure the integrity of the blockchain itself.
A Transaction is appended to the chain
There are two parties to each event recorded within these transactions. The agreed events, transactions and smart contracts are ultimately included in a block and properly extended onto the chain for everyone to see and read. More about Confidentiality in another post.
Once governance is established
People can now interact
Each party has an address and then addresses unique to each asset e.g. coin. The address, in most cases, is simply an asymmetric cryptographic public key.
-
- The individual, as is always the case with cryptography, has their own private key(s); they must retain, never lose and keep secret.
When the two parties decide to record an event; the sale or transfer of the title to a car.
-
- A formal record of a property, a transaction, ledger entry is created.
- The basic data.
- The seller’s public key
- the buyers public key
- the payload
- a hash
- the signature created by the seller using their private key.
The transactions are broadcast to the network, buying and selling included. These transactions can take place through various methods; for instance, digital currencies could be purchased online, whereas to sell, you may have to use Bitcoin ATM and other ideas, which you can learn on Coin Cloud or similar company blogs.
The nodes or miners continuously work to assemble a defined number of transactions and create the next block.
The chain’s role is to record the providence of an asset and the immutability of all the associated transactions.
-
- Each active node or miner is attempting to create the next block.
- The mathematics involved and the use of hashes to bind this new block to the existing blocks in the chain is beyond the scope of this blog.
- Let us simply assume the mathematicians and cryptographers define as part of the original design of each chain an infallible solution to the issues of economics, security, integrity, and immutability.
- These specifications will define the hash game and how one adds the next block to the chain retaining the immutability of the present and the past
By being the first to calculate the cryptographic nonce
The winner receives a reward.
-
- Hopefully proportional to the cost of work or other discernable and agreed method of reward.
- The other active nodes then test to see if they agree the first got it right.
- If consensus is reached the new block is appended to the chain.
- This all assumes 51% or more of the miners or nodes reach consensus on the winner’s answer. And no one can control 51% or anything closer than 33%.
Around and around the game continues, as transactions are added and immutably recorded on the chain.
This whole process fundamentally assures history cannot be altered.
Chains split and fun things happen
If the process is not elegantly managed in full sight of all the participants.
Going Cashless
For some twenty plus years, I can remember hearing people speak of the dream of an economy without coin and paper money. A dream, driven by the desire to promote the use of electronic payments.
Over the last months, a number of articles focus on promoting the idea of a cashless society. They all speak to the advantages and attempt to promote the concept, arguing we can:
- Eliminate the concern of thugs insisting at gunpoint for the cash
- Reduce the risk of employee theft
- Stop paying people to count all those dirty coins
- Remove the need for an expensive safes
- Stop paying to have a specialist truck take the money to the bank
- Eliminate the grey market
The business case for a merchant to eliminate cash seems to be beneficial. Many have tried and succeeded to no longer accept cash.
At the same time articles report on the new regulations; various cities and states are implementing and considering. These regulations are intent on outlawing merchants from going cashless. The argument often focuses on how eliminating cash disadvantage the underbanked.
Then there is a reality! As a consumer, I recently have been surprised at the need to carry cash and the unsettling pleasure of finding out I still had cash in my leather wallet.
The first wake up to this reality took place while driving from St Simons, GA to the Orlando International Airport. In the trusting hands of Google Maps, I traveled down I-95, across I-4 and was directed to the FL-417. Suddenly a road sign informed me that I was on one of the various Florida toll roads. Above my head was a road sign indicating which lane, based on my preferred method of payment, to move into. Driving a car that was not mine and knowing it did not possess a PeachPass, my only option was cash.
Fortunately, I had cash and was able to continue my journey.
The following Friday my father and I went to The Lodge to play Sniff, a dominoes game. The game was competitive and cash was the only method to settle. With a bit of cash in my pocket, I was able to pay the few dollars I lost.
One Saturday a street vendor in front of the local Harris Teeter was selling spare ribs. When I went to pay they informed me, they only accepted cash. Once again I was fortunate, I had enough cash and was able to buy those delicious ribs for dinner.
On various Sundays, when the collection plate came around, I’ve had a check or a bit of cash and was able to leave my tithing.
On a number of occasions, the valet, tour guide or other service individual deserved a tip and I’ve had a few dollars in my wallet.
Two more events brought the reality of how society does not want cash to disappear.
One morning, I wanted to enjoy a pastry. Not having $2.75 to pay for the Danish, Sweet Mama’s, a local baker, charged me $0.50, an eighteen percent surcharge, simply to use a credit card
Finally, yesterday as a guest for lunch at the local Rotary Club, I was confronted with a series of cash only events. This time I did not have any cash and was not in a position to contribute to various worthy causes.
We dream of a cashless society. Yet churches, valets, toll booths, street vendors and the Rotary all continue to desire or require cash. Some are not even willing to accept anything but cash.
Looking at our society from two different angles, we must accept the continuing need for cash. Be it the underbanked, unable to acquire a credit or debit card; or those who carry many credit cards, both need to use cash simply to eat or enjoy life.
Later today I will have to visit the ATM and make sure I have a bit of cash in my wallet.
https://www.paymentssource.com/news/target-outages-show-the-failings-of-cash-as-backup
Cash is King especially when the battery dies or the power goes off
Digital payments are growing, but consumers aren’t ready to abandon real money
Cash is king let us never forget it. Cash has always been the primary form of payment. It was until very recently accepted everywhere. Most likely will once again be accepted everywhere especially given the need to make sure we do not disenfranchise the unbanked and underbanked will remain the default form of payment
This said, what always amazes me is how so many authors forget Apple Pay, Google Pay and the other NFC based mobile phone based payment solutions are simply another device capable of carrying your debit and / or credit card credentials.
What many of these authors are starting to remember is how much it costs a merchant to accept these alternate forms of payment. I wonder when they will also begin to appreciate how many if not all of these alternate forms of payment only work when the power is on. Our always on society assumes power never goes off. We dream of everything in our mobile phone and forget when we last could not use our phone because the battery was empty. Or the store clerk who could read your card because the power went down.
This is one of the redemining facts about cash. Cash exists without power and can be used whenever.
Are we in Need of Faster Payments – a question of speed and instant gratification
When I started to read this article, https://www.pymnts.com/news/b2b-payments/2019/wespay-corporate-faster-payment-adoption/ , my first thought, why would anyone in accounts payable want to pay a bill sooner than it is due. Clearly someone in accounts receivable, the CFO and the treasurer, is in need of a strong cash position. Therefore therefore, wants to bring cash in as fast as possible. This classic struggle between the buyer (accounts receivable) and the seller (accounts payable) begs the question – Who gains from faster payments and who loses?
Clearly the financial institutions are stuck in the middle.
-
- On one side their clients want moneys to flow into their accounts, oh so fast.
- While on the other hand those same companies would prefer moneys moved out of their accounts at a snail’s pace.
If the competition offers the service, then, the financial institution simply must decide if faster Payments creates a competitive disadvantage.
The question is not if – it is when.
Do we the consumer care? Today we have credit and debit cards which allow us to pace the movement of money. In the case of debit – today. In the case of Credit – some number of days after we get the bill. We can set up autopay facilities for those every month payments. We can schedule money transfers to occur on the day we desire.
From a business and technical perspective the movement of funds immediately upon instruction, makes good sense. We the receiver are assured those funds are good funds. We the sender know the moneys have been sent and received. Therefore, whatever subsequent result can be expected, now!
365/7/24 seems to be what instant gratification is all about. We want everything now and have lost the excitement of expectation.
All this said, there are risks we must consider when deciding to employ faster payments. There is no recourse. Once the moneys have been authorized the moneys are in the hands of the party you transferred them to. Only if they so desire, will you be able to recover from a mistake.
Worse still, if someone is able to assume your identity then an even greater risk exists. The funds are gone. The party receiving them will have no interest in addressing your lose.
Therefore Strong Authentication is the essential requirement.
Smart Cards with Fingerprint Scanners
Over the last couple of years the reality of fingerprint cards is a hot topic in conversation, white papers and press articles. It led me to think about the challenges and opportunities associated with this intriguing convergence of technologies.
My purpose is not to determine which solution is best or which companies are developing and selling them. My goal is simply to explore.
The first consideration begins when the card is constructed. Here we must ask the mechanical question relative to how the electronics are integrated into the strata of an ID-1 card. This then begs the question of making sure this new card conforms to the specifications dictated by Payment, Networks, Governments or other bodies who define the use of these branded cards. If we continue to think about the card manufacturing process we need to think about electronics and the use of heat in the typical lamination process or the inclusion of metallic materials used to create a particular look. One needs to think about the method of connecting the various internal components to the other electronic elements as the fingerprint scanner, antenna(s)m LEDs, batteries, the EMV chip or contact plate on the face of the card.
The second set of concerns must be related to the personalization of the card. First question is where will it be personalized? in a branch or within a bureau? How will it be personalized? With a thermal printer, laser engraver or embossing machine? Will any of the personalization processes adversely affect the electronic?. Similarly it will be appropriate to confirm whether any of the various card transport mechanisms will disrupt or damage the sensor and related electronics.
At some point in the processes the consumer must register their fingerprint and the resulting template must be instantiated into the card. How will this be done? Some speak of an in branch process. Others talk about some type of first time cardholder activation process performed when they receive the card in the mail.
Clearly there are a lot more questions the issuer, card manufacturer and personalization provider need to address. Let alone the method of making sure the cardholder knows how to use the card at the point of sale or ATM
The key question is the cost of the card, is it worth it?
Where are we going
Each morning I read trade articles on Blockchain, Faster Payments, Mobile Wallets, Authentication, Identity and other alerts & subjects of interest. Each day the writers leave me thinking about the future of society, howbwe will address cyber security, what we can do to funally eliminate fraud and which solutions will help us to mitigate risk. These then drives concern about where we will end up, as we drive to define effective means of identity and authentication, capable of supporting the individual desire for convenience and gratification.
Facial recognition deployed to speed up entry and exit to and from countries and through airports are here. The surveillance state is emerging at alarming speed. These same cabilities could potentially deliver a safer environment. Which will it be?
Physical and behavioral biometrics many feel should become the primary means of authentication. Yet, false acceptance and more importantly false rejection will result in inconvenience some expect the consumer to tolerate while other remember friction typically ends up with the consumer abandoning the journey.
The cost of payments, the escalating concern of the retail sector, remund us thatnpayments are sourcesnof revenue for some and friction for others.
Identity theft and the ability to create synthetic identifies are the fears of many. Consumers whose identity is stolen struggle to regain their standing.
In the end all we seek is:
- Pay for something
- Identify ourselves
- Protect our hard earned money
- Live a safe and productive life
- Be assured you are you and not someone else