Today 2019-12-12 I found my way to the following article and associated podcast.
https://www.constellationr.com/blog-news/identity-dead
Below is a flow of thought as I read and listened. to Jon Reed and linkedin.com/in/lockstep Stephen Wilson discuss this most interesting topic.
Surveillance Capitalism – So many are taking advantage of our data!
We need to evolve through the pony express stage of data management, and get to a point where there are responsible data intermediaries who are being held to account.
Identity management, for me, is about proving things about myself. I want to log onto a bank and prove that I have a particular bank account. Sometimes I want to log on and prove that I am the controller of a multi-party bank account with my wife. And sometimes I want to log onto a health service and prove my health identity. So this is all about proving things about me in different contexts.
In the podcast, they beg the question “Why is the Digital Identity problem still any issue”? This leads one to think about the scale and expectation so many have surrounding this idea of “DIgital Identity”!
They then go on to ask the question What is two-factor authentication and remind us that our phone is a two-factor device, exactly what the standards FIDO Alliance worked to develop. They remind us of the reality that people look after their phones. We know when our phone is not with us.
Why not simply bind my identity to my phone.
Mr. Wilson sees the phone as the second factor. I would suggest our devices, bond to our identity, is the primary factor.
Mr. Wilson reminds us that Identity is all about Verifying Claims. We claim to be someone and the relying party seeks to confirm that I am who I claim to be. Or, when I seek to log back into a website, the relying party needs to make sure it is I – the same person who the relying party originally proofed, registered and agreed on an identifier and an associated means of authentication.
Attributes are more interesting than Identity
Attributes are what matters in the various relationships we have when we interact with another. As we think about our data we need to think seriously about what other parties need to know about us and what we wish to share with them. Efforts in Europe to institute GDPR and the efforts in California to implement CCPA
As I continued to read and follow the thread I ended up at a W3C working group working on “Verifiable Claims” and found the following:
Abstract
We are expecting people to be better than smarter than the crooks. This is an interesting thought that begs the question.
How do “we the people” trust anything we hear, read or otherwise come across.
How does each of us keep up with all of the various products, standards, specifications and other efforts to develop stuff capable of securing our “IDENTITY”?
I am a firm believer in the work the FIDO ALLIANCE and W3C’s work on Web Authentication and recommend its adoption and use based on authenticators capable of adhering to a level of security certification commensurate with the associated risk of the acts, transactions, information, and services offered by the relying party to the user.

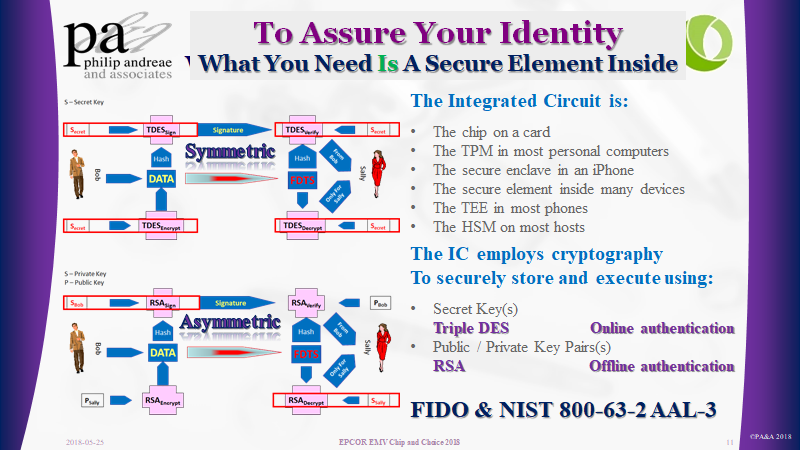













 . How we restore privacy and what will happen as the new GDPR regulations go into force in Europe, and as California moves to introduce its privacy legislation; requires each of us to watch carefully and be part of the move to restore the consumers’, OUR, right to the data that is us.
. How we restore privacy and what will happen as the new GDPR regulations go into force in Europe, and as California moves to introduce its privacy legislation; requires each of us to watch carefully and be part of the move to restore the consumers’, OUR, right to the data that is us.