These two words began to fascinate me as I began to understand the value of cryptography while working through the goals we established when developing EMV and attempted to secure the payment credentials when used on the Internet.
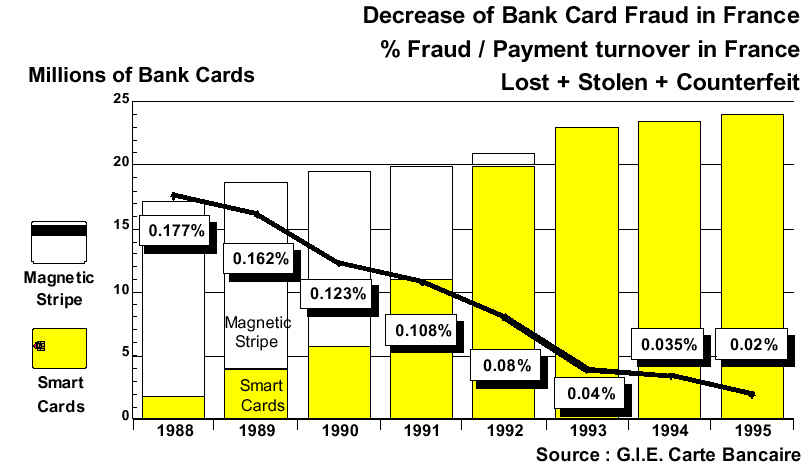
With EMV we were trying to address the challenge of the fraud (an issuer cost) resulting from the ease of counterfeiting the token of the token which was a token of a token already.
This last broken token is the magnetic stripe on the payment card.
The payment card, in and of itself, is a token. An instrument imbued with physical security features e.g. the hologram and signature panel. Security features the merchant is supposed to check when attempting to allow a buyer, the consumer, to use the payment credential associated with the card to make payment for good and services.
The PAN is just a unique number, another token. This unique number is simply the index, The identifier within the payment credentials, which associates the payment with the underlining source of funds.
The source of funds, the PAN or Token pointing to, is then either a line of credit, prepaid balance or bank account.
The card, the hologram, the magnetic stripe and the printed security features and the PAN had reached the end of their useful life, as security features or tokens. The criminal knew how to compromise the card and associated static data.
As we entered the 90’s, the card as the carrier of the payment credential, with those physical security features, was longer a means of Authentication. These layers of authentication had been compromised. In other words the token was broken!
To address this concern, in 1993 the founders of EMV embraced the chip card and its Cryptographic capabilities. In particular, the use of symmetric and asymmetric algorithms to provide a new set of tokens the merchants (asymmetric) and Issuer (symmetric) could use to Authenticate the unique carrier of the payment credential – the token – the chip card.

On the Internet the challenge is different. The physical features of the card are not easily accessible, hence useless. In 1993, when WWW became the thing of conferences, everyone said lets think of the internet in the same way we allow merchants to sell stuff via mail and telephone. Everyone simply decided and agreed to exploit the acceptance rules agreed on for those other virtual environment, the phone and the mail.
Bottom line, in the world of mail order / telephone order and now a browser; merchant simply agrees to accept the cost of fraud, given the CARD is NOT PRESENT. Worse still how do they prove the right cardholder in present?. For the merchant, given the potential of the Internet, it is was a small price to pay.
Everyone simply accepted that be capturing the data embossed on the front (PAN, expiry date and cardholder name) and the CVV printed on the back of the card and, in some cases, using the power of AVS “Address Verification Service” a modicum of security could be factored in. At least for a time!
SET “Secure Electronic Transactions”, a cryptographic mechanism Visa and MasterCard cooked up, was developed circa 1995-1996 and deployment was attempted. The challenge, the limitations of the then deployed technologies and the inability to provide a reasonably convenient user interface. The problem begins with loading payment credentials into the browser and more importantly figuring out how to use them when shopping.
A set of great ideas foiled by convenience.
Next came 3D-Secure, an invention of Visa. This time the idea was to exploit the power of passwords and secret questions to authenticate the user.
Nice idea, well thought out; but, unfortunately not designed with the consumer in mind.
Another feeble failed attempt to develop a mechanism to authenticate the buyer. Or better put, solve the dilemma the New Yorker so aptly described
“On the Internet nobody knows your a dog”.

All this begs the question – how will we secure payments on the Internet?
3D-Secure 2.0, maybe? Or maybe W3C and the FIDO Alliance have the answer in what is called WebAuthN.
To address this question we must begin by defining the problem.
When we think about payments and we think about shopping on the internet it is all about someone or something {read issuer} agreeing that the consumer will make good on the promise to pay and therefore the issuer is willing to guarantee payment towards the merchant. The challenge, how do we confirm it is the legitimate person seeking to pay with their means of payment.
In other spheres of endeavour it’s about granting access to someplace or some website. In the physical world we have a key that we can insert into the lock or a security device {card} we can insert or tap on a reader programmed to recognize our credential and allow us access.
On the Internet, the use of a physical card with physical security features, numbers, letters, and a magnetic stripe was not feasible. Instead, we ended up employing user names, passwords, and payment encryption. Payment encryption, which secures sensitive financial information during online transactions, offers a crucial layer of protection. The user name – a unique identifier, and the password, a secret, support the identification of the person using the browser or connected device, from somewhere out there.
If we could each create and remember complex secrets, these cumbersome things call passwords. And, more importantly, never share them with nefarious individuals seeking to take advantage of our naiveté. All would be at peace in the world of security and convenience. The problem is expecting you and I to remember the myriad of complex passwords and not get tricked into sharing our secrets.
Is there an answer, I believe so and at Money 2020 October 25 we will be discussing this very topic. Wednesday Morning at 8:30 in the Titian room at The Venetian in Las Vegas on Level 2, join us as we discuss Identity is Fundamental: What You Need to Know About Identity & The Future of Money.