As we continue to explore the case for Identification and Authentication I share the below article.
What is becoming clear is standards are being embraced.
In the Payment space
Will it be W3C WebAuthN, 3DC and Webpayments or EMVCo SRC & Tokenization?
My guess depends on if standards bodies can play well together. EMV (contact or contactless) will remain the many stay for physical world commerce, until the App takes over the Omni Channel shopping experience. then the merchant will properly authenticate their loyal customer and use card on file scenarios for payments. The question of interchange rates for CNP will see a new rate for “Cardholder Present&Authenticated/ Card Not Present.”. In time when a reader is present I can see an out of band “tap to pay” scenario emerging using WebPayments and WebAuthN.
In the identity space
I contend the government and enterprise market will go for a pure identification solution with the biometric matched, in the cloud, in a large central database. In order to maintain a unique and secure cloud identity, they might probably make use of various opportunities that come their way (you can hover over at this website to learn more).
However, does that mean it includes what you know username, email address or phone number? Maybe! If it is simply the captured image or behavior, then it is a 1 to many match. If it is with an identifier, it is classic authentication with a one-to-one match.
In the pure authentication space where the relying party simply wants to know it is the person they registered. Then, the classic FIDO solutions work perfectly and will be embedded into most of our devices. Additionally, the use of a visitor sign in sheet synced with the security database could expedite the sign-ins of visitors. It could also see its applications with employee log authentication and verification. Or, as we’ve seen with some enterprises, the relying party will embrace U2F with be a FIDO Key, like what Yubico and Google recommend.
The classic process needs to be thought about in respect to what can be monetized.
- Enrollment = I would like to become a client or member
- Proofing = Ok you are who and what you claim, we have checked with many to confirm your Identity – This is where federation comes in.
- Registration – Verification = Ok, now we confirm it is you registering your device(s)
- Authorization & Authentication = Transaction with multiple FIDO enabled relying parties using your duly registered authentication.
How Microsoft 365 Security integrates with the broader security ecosystem-part 1
by toddvanderark on July 17, 2018
Today’s post was coauthored by Debraj Ghosh, Senior Product Marketing Manager, and Diana Kelley, Cybersecurity Field CTO.
This week is the annual Microsoft Inspire conference, where Microsoft directly engages with industry partners. Last year at Inspire, we announced Microsoft 365, providing a solution that enables our partners to help customers drive digital transformation. One of the most important capabilities of Microsoft 365 is securing the modern workplace from the constantly evolving cyberthreat landscape. Microsoft 365 includes information protection, threat protection, identity and access management, and security managementproviding in-depth and holistic security.
Across our Azure, Office 365, and Windows platforms, Microsoft offers a rich set of security tools for the modern workplace. However, the growth and diversity of technological platforms means customers will leverage solutions extending beyond the Microsoft ecosystem of services. While Microsoft 365 Security offers complete coverage for all Microsoft solutions, our customers have asked:
- What is Microsofts strategy for integrating into the broader security community?
- What services does Microsoft offer to help protect assets extending beyond the Microsoft ecosystem?
- Are there real-world examples of Microsoft providing enterprise security for workloads outside of the Microsoft ecosystem and is the integration seamless?
In this series of blogs, well address these topics, beginning with Microsofts strategy for integrating into the broader security ecosystem. Our integration strategy begins with partnerships spanning globally with industry peers, industry alliances, law enforcement, and governments.
Industry peers
Cyberattacks on businesses and governments continue to escalate and our customers must respond more quickly and aggressively to help ensure safety of their data. For many organizations, this means deploying multiple security solutions, which are more effective through seamless information sharing and working jointly as a cohesive solution. To this end, we established the Microsoft Intelligent Security Association. Members of the association work with Microsoft to help ensure solutions have access to more security signals from more sourcesand enhanced from shared threat intelligencehelping customers detect and respond to threats faster.
Figure 1 shows current members of the Microsoft Intelligent Security Association whose solutions complement Microsoft 365 Securitystrengthening the services offered to customers:
Figure 1. Microsoft Intelligent Security Association member organizations.
Industry alliances
Industry alliances are critical for developing guidelines, best practices, and creating a standardization of security requirements. For example, the Fast Identity Online (FIDO) Alliance, helps ensure organizations can provide protection on-premises and in web properties for secure authentication and mobile user credentials. Microsoft is a FIDO board member. Securing identities is a critical part of todays security. FIDO intends to help ensure all who use day-to-day web or on-premises services are provided a standard and exceptional experience for securing their identity.
Microsoft exemplifies a great sign-in experience with Windows Hello, leveraging facial recognition, PIN codes, and fingerprint technologies to power secure authentication for every service and application. FIDO believes the experience is more important than the technology, and Windows Hello is a great experience for everyone as it maintains a secure user sign-in. FIDO is just one example of how Microsoft is taking a leadership position in the security community.
Figure 2 shows FIDOs board member organizations:
Figure 2. FIDO Alliance Board member organizations.
Law enforcement and governments
To help support law enforcement and governments, Microsoft has developed the Digital Crimes Unit (DCU), focused on:
- Tech support fraud
- Online Chile exploitation
- Cloud crime and malware
- Global strategic enforcement
- Nation-state actors
The DCU is an international team of attorneys, investigators, data scientists, engineers, analysts, and business professionals working together to transform the fight against cybercrime. Part of the DCU is the Cyber Defense Operations Center, where Microsoft monitors the global threat landscape, staying vigilant to the latest threats.
Figure 3 shows the DCU operations Center:
Figure 3. Microsoft Cyber Defense Operations Center.
Digging deeper
In part 2 of our series, well showcase Microsoft services that enable customers to protect assets and workloads extending beyond the Microsoft ecosystem. Meanwhile, learn more about the depth and breadth of Microsoft 365 Security and start trials of our advanced solutions, which include:



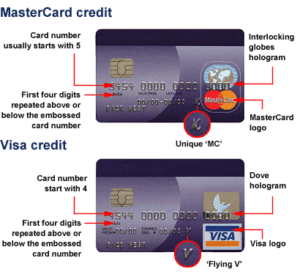
 We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card.
We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card. now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC”
now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC” 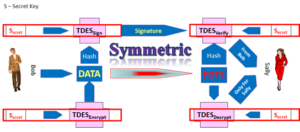 were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
 Apple and Google, supported by their friends, the payment network operators.
Apple and Google, supported by their friends, the payment network operators.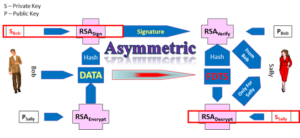 If the Issuer or their processor is in control and understands
If the Issuer or their processor is in control and understands  Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure.
Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure. be they criminals, state actors and terrorists to find alternate another channels for their financial gain.
be they criminals, state actors and terrorists to find alternate another channels for their financial gain.



 and a Eurocard was all we needed to buy and enjoy life. Electronic payments was the norm, paper checks were a rare oddity and cash, well yes there was a very present grey economy.
and a Eurocard was all we needed to buy and enjoy life. Electronic payments was the norm, paper checks were a rare oddity and cash, well yes there was a very present grey economy.

 We could go on and talk about how Apple saw the possibility of a 0.15% income stream from ApplePay based mobile payments and how the EMVCo tokenization framework evolved to support their desire to protect the Apple Brand.
We could go on and talk about how Apple saw the possibility of a 0.15% income stream from ApplePay based mobile payments and how the EMVCo tokenization framework evolved to support their desire to protect the Apple Brand.






 Tokenization why is everyone so excited?
Tokenization why is everyone so excited? They simply wanted the PAN to be an index, “a pointer” “an Identifier”, to an account, or relationship, a card issuer (financial institution) created between itself and the cardholder. In our quest to take advantage of the telephone, the mail and ultimately the internet as a set of sales channel. The Payment System actors agreed if the card acceptor “merchant” would accept liability. Then, they could simply use the PAN, the expiry data and cardholders name to effect a card payment. This acceptance of liability was an acknowledgement they could not inspect the card and verify that the physical security features where present, hence the token was not present to be authenticated.
They simply wanted the PAN to be an index, “a pointer” “an Identifier”, to an account, or relationship, a card issuer (financial institution) created between itself and the cardholder. In our quest to take advantage of the telephone, the mail and ultimately the internet as a set of sales channel. The Payment System actors agreed if the card acceptor “merchant” would accept liability. Then, they could simply use the PAN, the expiry data and cardholders name to effect a card payment. This acceptance of liability was an acknowledgement they could not inspect the card and verify that the physical security features where present, hence the token was not present to be authenticated.