Recently I was directed to a link http://paymentsjournal.com/tokens-work-because/ and wanted to write the author Sarah Grotta. As I wrote the message crystallized in my head and maybe as this prior post already discussed, this idea of tokenization made me cringe.
I contend that Tokens exist because we turned the PAN Personal / Primary Account Number, like we turned the SSN Social Security Number, into an authenticator. One can must ask the question. How can a random value (an identifier) become an authenticator and remain secure?
EMV works because it renders the Card unique, hence addressing the question of counterfeit, by employing the first factor of the classic MFA Multi-Factor Authentication concept “What You Have”. EMV defined a common set of secrets and digital credentials; securely stored in a Secure Element or Chip Card.
“What You Have”. EMV defined a common set of secrets and digital credentials; securely stored in a Secure Element or Chip Card.
We here in the United States decided not to implement the second factor, the Personal Identification Number or PIN, for a variety of reasons. Hence, why Lost and Stolen remains an issue or weakness in the American Card Payment environment.
Biometrics are emerging and could solve for the assurance of cardholder presence. The challenge is how to effectively (cost and convenience) locate the biometric sensor and facilitate the matching of the sensors output to the persons registered biometric. Let alone, how does one make sure the right persons biometric was registered and associated with the device.
In the mail order / telephone order, now cyberspace, we did not replicate merchant authentication, the first factor – “What You Have. The card,  once was secured with things like the magnetic stripe, using CVV1, the Hologram and the other physical features. We simply shifted the liability to the merchant and called it a “card not present” transaction.
once was secured with things like the magnetic stripe, using CVV1, the Hologram and the other physical features. We simply shifted the liability to the merchant and called it a “card not present” transaction.
People can claim all sorts of goodness because of tokenization. They can talk about how the EMVCo’s tokenization framework describes the use of tokens in device and domain specific scenarios. All of this, an issuer, could have done; if they, like some did, simply issued another number, a PAN, to the wife, bracelet, watch, ring or whatever other permutation they deemed appropriate. They can talk about dynamic data. yet what they often forget to include when they use the words “Dynamic Data” they are really talking about a cryptographic value as described in EMVCo Book 2.
Yes, this does mean the question of how the PAN and its digital credentials get deployed; has to be addressed. This said, GSMA with EPC did offer some thoughts, last decade, when they described the Trusted Service Manager
Instead handset oligopolies replaced the MNO with the their Mobile Pay wallets. They working with the ![]()
![]() Payment Networks and focused on control and the creation of income. They, as monopolist will, have created barriers, restricting others from offering comparable services. The TSP now becomes this restrictive service that guarantees the power of companies like
Payment Networks and focused on control and the creation of income. They, as monopolist will, have created barriers, restricting others from offering comparable services. The TSP now becomes this restrictive service that guarantees the power of companies like 
 Apple and Google, supported by their friends, the payment network operators.
Apple and Google, supported by their friends, the payment network operators.
The original article also spoke of the PAR; another data element merchants, processors and the industry, will have to invest in supporting.
I ask the question.
If we had assured the authentication and verification of every payment transaction
Using Multi-Factor Authentication
Why did we need to turn the PAN into a dynamic value?
My contention, simply use the appropriate level of cryptography.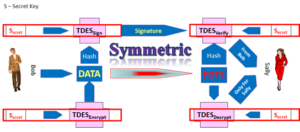
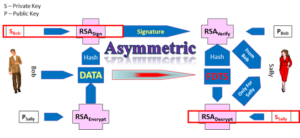 If the Issuer or their processor is in control and understands basic EMV and Cryptography, then securing the PAN is not an issue.
If the Issuer or their processor is in control and understands basic EMV and Cryptography, then securing the PAN is not an issue.
Consider household financial management. If each member of a household has a unique PAN; budget, tax preparation and understanding who spent what where is a lot easier. The husband,wife and children should have their own unique PAN, stored in the clear in their devices and on their card.
The real requirement, my personal devices, including my payment card, simply need to be linked to one PAN their Personal Account Number, associated with the individual. The PAN Sequence number could easily allows each device to be uniquely identified, if necessary. The card and devices becomes the carrier of your identifier. A thing that can be authentication as something you have.
Here is where the second factor comes in. Is the person presenting the PAN the rightful and authorized individual? All this required, is assurance to the shareholders that the presentment of the PAN is a unique and authorized event. This is best achieve by using either something you know or something you are to bind the individual to the instrument carrying the Identifier.
Yes, a bit of friction to assure the consumer they are securely paying for what they want to buy
Since the World Wide Web came of age and merchants saw its potential. The question of how to secure the  Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure.
Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure.
Each, an attempt to provide some means of Authentication and Verification.
Each introducing a level of friction as a means of security.
This is the problem. The market did not start by emphasizing the need for security by educating the consumer. The industry needed to help the consumer understand they should care and want to securely pay for what they intend to buy.
Instead:
- The Zero Liability Policy was adopted.
- The merchant was more than happy to sustain a degree of lose (fraud) in exchange for sales and profits.
The result, as all anticipated would happen, was blissfully ignored and eventually they cried out about.
Fraud migrated to the weakest point
Just like water finds its way to the lowest point.
EMV, introduced in the Face to Face card present environment, pushing the bad guys: be they criminals, state actors and terrorists to find alternate another channels for their financial gain.
be they criminals, state actors and terrorists to find alternate another channels for their financial gain.
EMV and now the recently published WebAuthN and FIDO specifications create effective mechanisms for Consumer Authentication.
Let us please remember – the PAN, a user name, your social security number or your email address are excellent Identifiers. They should not be authenticators and they are not a means of “Identification”.
Let us also remember, the term Identification means that one is assured of the irrefutability of identity.
The big question:
- Why did we have to get rid of or replace the PAN?
- Why did we and continue to need to invent and invest in all this addition overhead?
- Why did we not simply address authentication?
Some will argue the challenge of using the PIN or a Password, as a means of Verification, is because it is to hard to remember. Especially, if each password people use to access website, services, building, has to be unique. Some will argue imposing friction to add security is not convenient. Others will remind us that security is and has been a necessity since the beginning of time.
Why didn’t we when we created this great new digital shopping mall?
Bottom line each of the devices used to present or acquire the PAN, must be capable of authenticating the identity of the authorized presenter, in both the physical and virtual world.
At least these are the views of someone who believe history provides a baseline for tomorrow and tomorrow must be designed as a function of where you want to be, knowing where things came from.
