Karen Webster
CEO, Market Platform Dynamics
President, PYMNTS.com
Karen,
Last week in your publication I read the article Deep Dive: Security In The Time Of Faster Payments and I had to offer the following thoughts:
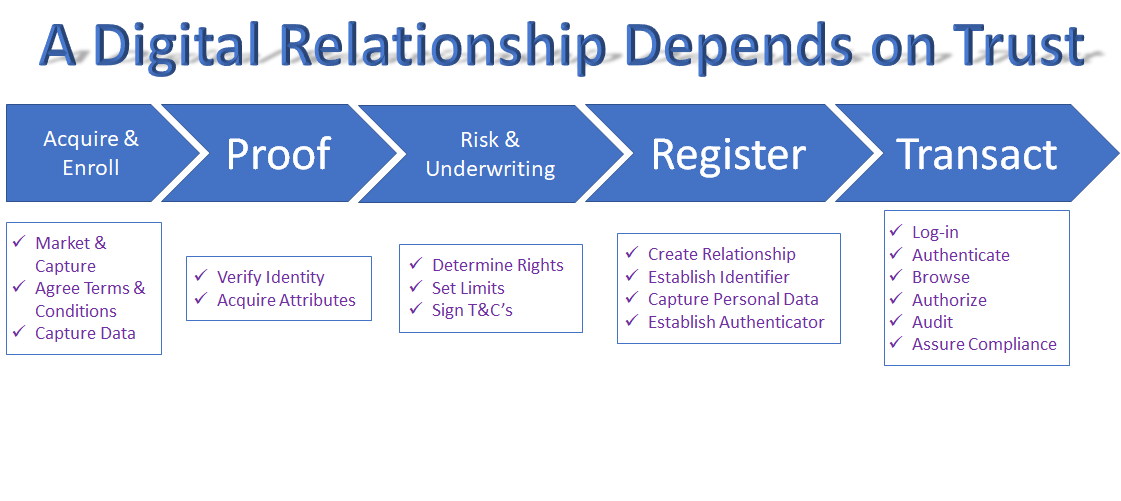
The concept of Multi-Factor Authentication is based on the idea of layering multiple authentication techniques on top of each other.
We typically speak of three factors “What You Have”, “What You Know” and “What You Are”.
When we think of “What You Have” we think of a “Thing”. An object that cannot be replicated or cannot be counterfeited.
An object “a secure computer” that can be upgraded and made more secure as threats like Quantum emerge.
A unique object with a False Reject Rate FRR and a False Accept Rate FAR approaching zero.
In the physical world “the thing” is a card or passport. You will remember our first discussion, we came to agree the “secure computer” embedded inside provides a future proof mechanism. In the digital world, we depend on Cryptography. This Thing, inside our computers, mobile phones and other technologies; many refer to as a ROE “Restricted Operating Environment”. Technology people may call it a Secure Element, a SIM, an eSIM, a TPM, a TEE, an eUICC or even Security in Chip. Companies like ARM specialize in creating the design of these things and silicon manufacturers embrace and license their designs.
Today these connected devices (be they: personal computers, identity & payment cards, FOBs, mobiles phones, bracelets, watches and hopefully every IoT device) need to be secured. This array of cheap ~$1 security circuitry provides a place to create and/or store private keys & secrets keys, perform cryptographic functions and assure the integrity of the BIOS and software being loaded or currently running in these computers.
Think Bitcoin for a second. The key to its architecture is the Private Key associated with your store of coins. Lose it and they are lost. Many people store these in hardware, based on the use of a ROE.
The second factor is all about proving that you are present. Behavior, location, PIN, fingerprint or passwords are second or even third factors, be they something you know or something you are.
This is what FIDO and what WebAuthN is all about. Especially since they introducing the security certification regime. This is what the Apple Secure Enclave is and Samsung and others embed into their devices. This is what we put into payment cards, government identity cards and the Yubico keys we see various enterprises embracing. This is what Bill Gates started talking about in 2002. BILL GATES: TRUSTWORTHY COMPUTING
As we move to Faster Payments we must move to Secure payments. Immutability and irrefutably become key requirements. To achieve this goal I suggest we need to understand one fundamental security principle.
The First Factor
is Something(s) You Have
My Thing(s)
The Second and Third factors
Prove You Are Present
Storing Biometrics in the Cloud
Creates a Honey Pot
And, begs questions of Privacy
Let me identify myself to My Thing.
Then let My Thing
Authentication my presence to
The Relying Party (Bank or Credit Union)