If the buyer has something the seller wants, in exchange for the good or service they desire, then a transaction occurs. The challenge is simple, each party defines the value of what they are providing or exchanging and presto the trade occurs.
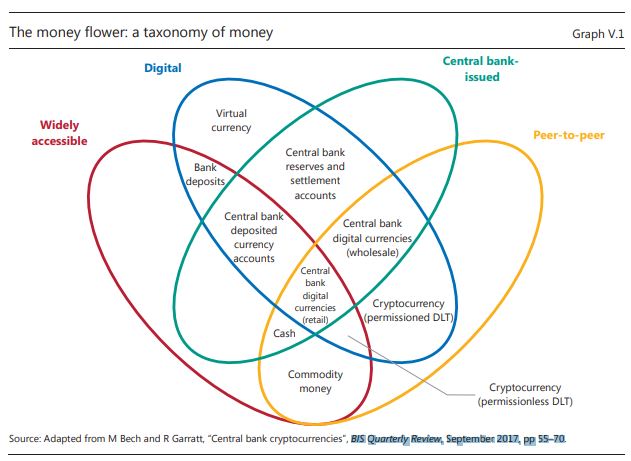
When society grows and the complexity of what each of us produces and when our needs are not aligned to this process called barter, a means of monetization is established. Society creates a trusted means of exchange – pebbles, coins, money, a promissory note or now even, some would argue, cryptocurrencies.
In other words, society created an answer to enable the exchange of goods and services between parties, who do not have the goods and services the other party seeks.
With cash, coins or other tangible representations of value, commerce is easy. When society does not develop a secure and trusted means of facilitating the exchange of things commerce, innovation and a good life cannot be achieved. To this end, paper money is imbued with ‘value’ based on the integrity of the party issuing the physical or now electronic ‘money’. The addition of the word ‘electronic’ brings technology, computers, and networks into the conversation. One network, typically referred to as the Automated Clearing House ‘ACH’ allows banks to electronic instruct the movement of ‘money from an account at one bank to an account at another.
The addition of the word ‘electronic’ brings technology, computers, and networks into the conversation. One network, typically referred to as the Automated Clearing House ‘ACH’ allows banks to electronic instruct the movement of ‘money from an account at one bank to an account at another. The use of an ach check processing system for business transactions between vendors and customers has become increasingly common in addition to banks. The advantage of this system is that it usually allows businesses to transfer money automatically between bank accounts so that their payments can be cleared out in a short period of time.
In the 1958 Bank of America created Visa Inc., in 1964 the Wallenberg family created Eurocard, and then in 1966 a collection of banks banded together to create the Interbank Card Association, Mastercharge and now MasterCard.
These payment networks, by necessity, add complexity. They create the need to establish a two sided market. On one side the relationship with the buyer, consumer, or cardholder. On the other side if this market the seller, merchant, or retailer.
Issuance and Acceptance. Two words to describe the two sides of a network. It’s only when the two sides of the market have sufficient participants. Only at the tipping point, when critical mass exists, can one claim to have created a self-sustaining network. A network of people promoting use to buyers and a network of merchants willing to accept payment based on the terms and conditions defined by the network. Beginning at this tipping point, the network and it’s Brand blossoms. If either side of the market does not achieve critical mass, the network collapses.
Relationships – The oil of commerce
Any two entities familiar and trusting in the Brand, or each other, can easily establish a temporary relationship with entities associated with the brand. If one or more of the entities require anonymity increases the level of trust and recognition the Brand must establish with these participants.
In a digital environment, we are in need of mechanisms to share and establish trust across trillions of electrons. The two sides of a relationship, in other words, the market, will not take the time to understand or appreciate the need for network and endpoint security; until the risk exceeds a threshold understood by the participants.
The Artifact of Trust
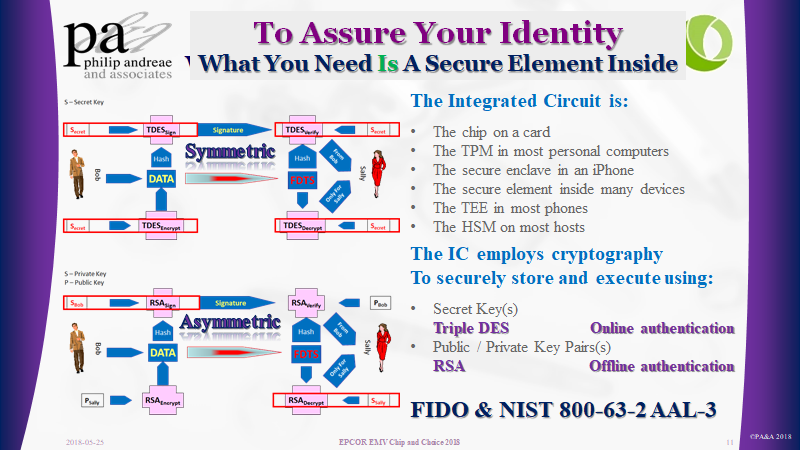
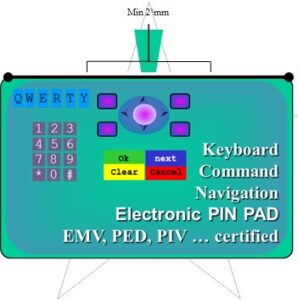
When a mutually trusted set of parties gives the citizen, consumer, employee or courtier a letter, card, device or any uniquely registered object, and provides every acceptor with a reader capable of recognizing the trusted thing. Then the two parties are in a position to establish “trust”. The consumer has a thing which is recognized and trusted by the acceptor. This is often referred to as “What You Have”.
Once the thing is recognized by the acceptor, then, the process of identification and authorizations (the transaction) can take place. The object – the artifact – carries an identifier. It possesses unique characteristics. The object also possesses a means of assuring the acceptor the presentation of that identifier represents a unique representation of that identifier.
The simplest artifact of establishing “trust” is a handheld thing, be it a key, fob, card, watch, pendant, phone, earpiece. It does not matter what it is, all that counts is that the merchant recognizes it and that the consumer is willing to carry and present it.
Trust, for the merchant, means they can, according to defined procedures, recognize and authenticate the thing. They are then in a position to pursue a temporary and trusted relationship. What can be achieved during the time the relationship of trusted is bounded, is constrained by an additional layer. In this layer the consumer, the acceptor and any third parties address which the rights and privileges are to be granted or pursued. This is when the exchange, sale, conversation, tranaction, event or access is granted.