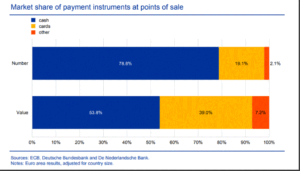
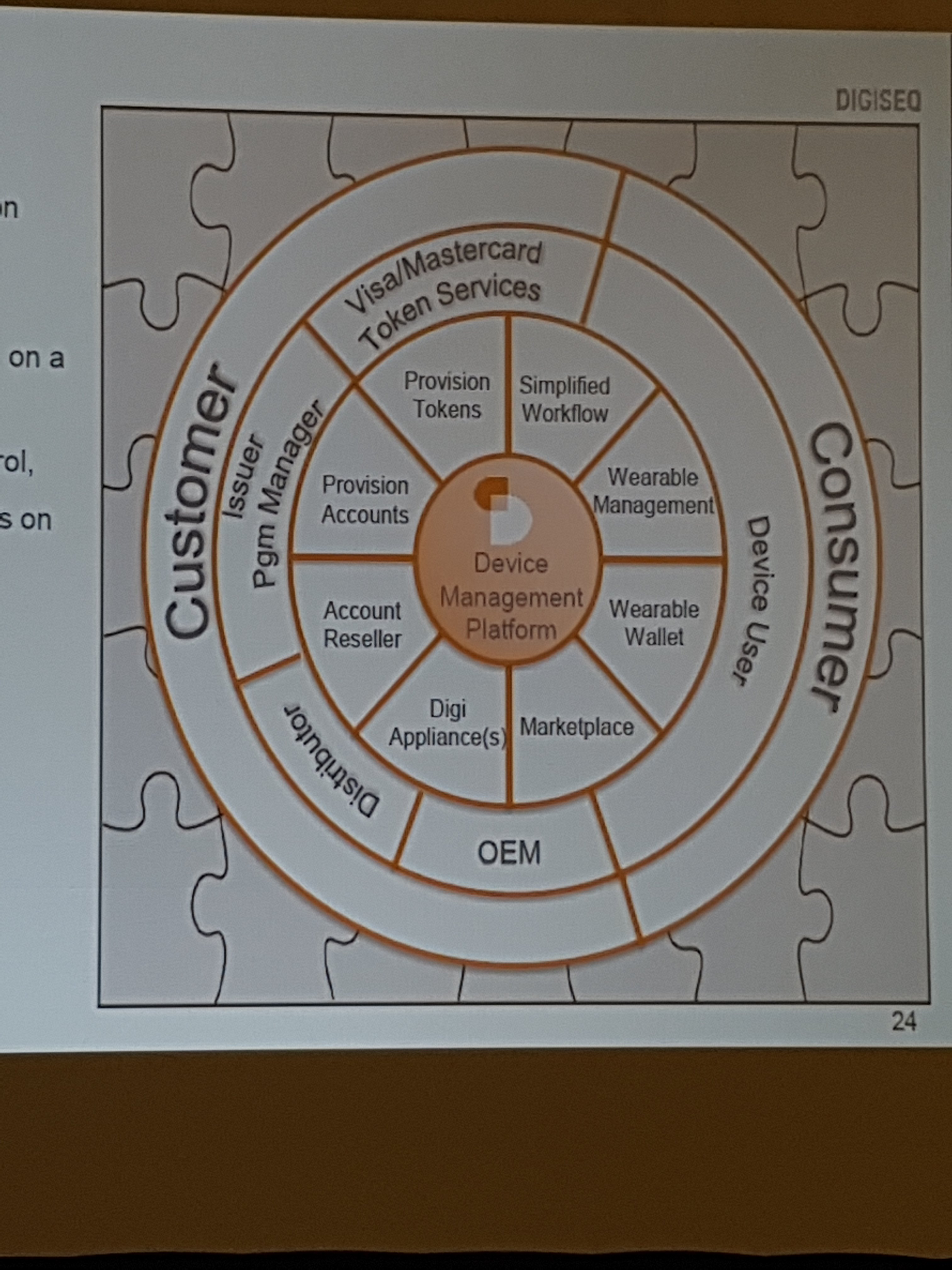
Identifier – Something you create or are provided to digitally identify yourselves. Identifiers are things like an alias, user name, email address are examples.
Identity – This is who we are or wish to represent ourselves to be. These are attributes and information about: where we live, who we work for, which banks we have relationships with, who our friends are, which clubs we belong to, our certified skills, what schools we graduated from, which country(s) we are citizens of, our LinkedIn profile, Our Twitter handle, our Facebook identifier, our phone number … . It is the sum of the attributes we can and will share with others, be they individuals, governments, entities or organizations; as we establish relationships and prove to them who and often what we are.
Authentication – The method we employ to assure that you, based on the identifier presented, are who we (the relying parties) thinks you are. You are the person the relying party accepted when you registered that Identifier as how you would digitally identify yourself. By itself the method of authentication should not allow another party to be able to determine anything about your identity. Privacy is the goal. FIDO Alliance and W3C have defined standards to support authentication.
Verification – The process of confirming that the secret or biometric match the secret or biometric that where originally registered to that Identifier.
Identification – A means of authentication that is bound to your identity. A EMV payment instrument “Chip and PIN”, a PIV card, an electronic passport, a membership card, a drivers license, a national ID are all forms of identification issued by a party that should be trusted to have performed a proof of the individuals Identity, based on a defined and often published criteria.
This particular word, for many, has an alternate meaning. In the biometric community they see Identification as the ability to use a biometric to determine ones Identity. This is achieved by performing a one (the person present) to many match (persons registered). The goal is the same, bind Identity to the mean of Authentication by using the Biometric as the Identifier.
Proof – The method a relying party or an individual uses to validate your claim of a specific Identity. In many cases this is achieved by relying on knowledge of another party. The relying party accepts the due diligence to proof your claimed identity was done to their satisfaction by another party. This other party is often referred to as a Trusted party. This effort to proof the identity of an individual is linked to words and acronyms like KYC “Know Your Customer”, ID&V “Identity and Verification” and Self Sovereign Identity. We classically assume that documents provided by a Government e.g. drivers License and Passports are a solid proof of the claims asserted on those same documents.
In a digital world this is the most important element of a how we as people, entities, governments and corporations can be assured that you are who we believe you to be.
I am once again am reminded of the 1994 New Yorker Cartoon