Apple exemplified an era of global capitalism that has passed from The Economist https://www.economist.com/leaders/2021/08/28/apple-exemplified-an-era-of-global-capitalism-that-has-passed
Category: eCommerce
EMVCo Good or Evil
https://www.securepaymentspartnership.com/wp-content/uploads/2019/12/Payment_Insecurity_Final.pdf
In 1993, I was asked by the then CEO of Europay International to establish a relationship with Mastercard, and Visa focused on developing the specifications necessary to assure the interoperability of chip card-based security for credit and debit payment cards. The result published in 1996 was the “EMV Integrated Circuit Card Specifications for Payment Systems.”
From these humble beginnings, EMVCo has emerged as a key organization in managing the standards behind card payment systems. In the white paper Payment Insecurity, commissioned by the Secure Payment Partnership, the author reminds us of the difference between standards managed by an open body and those tightly controlled by an exclusive group of competitors. One wonders if the owners of EMVCo will listen and strive to open up their membership or continue to use this entity to protect their proprietary interests.
In the introduction, the author speaks of a series of questions he intends to address. The first question of the paper
Is EMVCo furthering the entire U.S. payments industry or simply protecting Visa and Mastercard’s market share? page 5
begs the question, why limit the discussion to the USA?
This American only focus is driven by the desires of the Unaffiliated Debit Networks and a set of merchants. The paper ignores fundamental and, yes, anti-competitive elements of the EMV specification – the AID or the Application Identifier. It was and is directly related to the Brand responsible for the underlining technology incorporated into the Chip.
I then read the following complaint and am driven to ask how the consumer interpreted the prior Debit versus Credit prompts.
Visa’s response to this solution was to require merchants to display to consumers a choice between “Visa Debit” and “U.S.
Debit” at checkout. – page 13
In essence, what Visa required was simple, the terminal should comply with the EMV specification for “application selection,” key and inherent in the multi-application design of EMV and the underlining ISO 7816.
Moving further into the document in Section 6.1, the author attempts to document the history leading to the creation of EMVCo. As one of the founding members, the author’s sources were not involved and did not understand the history.
First, only France had a smart card solution designed to address Credit and Debit card fraud. They referred to their implementation as B Zero Prime.
Second, the UK in 1995 was driven by Visa to embrace an earlier version of the Visa specifications adapted to the unique requirements of the UK market and branded UKIS. UKIS and the unique UK requirements are responsible for changing many of the shall’s in the EMV 2.0 version of the specifications to should’s in the EMV 3.0 version. This accommodation was the result of legacy limitation within the X25 network the United Kingdom depended on for card authorizations.
To further identify issues with his record of history, the statement on page 22
EMVCo developed standards for chip cards that could work with credit, debit and stored-value cards
It is fair to suggest EMV attempted to incorporate Stored-Value cards in the specification. But as a result of the competitive realities of Europay’s Clip, Mastercard’s Mondex, and Visa Visa Cash stored value solutions, they agreed to exclude stored value cards from the specifications.
It then goes on to suggest EMV compromised and offered a Signature option. There was not a compromise; it was intentional. The goal, afford the Issuer the ability to determine, by Cardholder, which cardholder verification method they could be configured for. One need was to address issues of the disabled, e.g., the Blind.
Debit Routing as a result of the Durbin amendment. One might wonder why EMV did not consider this idea of multiple networks associated with a card.
EMVCo was unable and unwilling to resolve the lack of a debit AID because EMV was never designed for the U.S. market.
I sense that there is another front coming out of the Debit Networks seeking to argue the anti-competitive nature of EMV. The paper, link below, draws me to wonder about the argumentation surrounding “Application Selection.” Please let’s get back to basics – the “AID=Brand=Payment Scheme” drives “Routing.”
On page 13, it argues consumer confusion. I would argue it ignores the past. The EMV default user prompts of “Visa Debit” and “US Debit” are no more confusing than the historic “Credit,” and “Debit” prompts. I would argue consumer confusion already existed. The EMV specification for Application Selection simply afforded the Issuer the ability to provide more descriptive prompts by employing the “Application Preferred Name” instead of the default “Application Label.”
This whole fight surrounding EMV and Payment Security is really a fight about the future of Card Payments. On one face, they argue the Payment Networks did not assure the security of the card payments to protect revenue. On the other hand, they argue EMVCo is a closed standards organization designed to protect and assure the interests of its shareholders, without consideration for the other stakeholders in the payment, e.g., the merchant.
In the end, the argument comes down to the role, definition, and control. How we structure the underlining payment transaction is what we need to talk about. Who provides the mechanism, guarantee, and support for a particular mechanism decides the rules.
To Identify or to Authenticate what is the difference?
Today I read an article on LinkedIn
‘Identification’ is to give an answer to the question of ‘Who is he/she?’, while ‘Authentication’ is to answer ‘Is he/she the person who he/she claims to be?’
This distinction for me is clear. Yet, based on this article, and personal observation, people do not appreciate the unique difference between these two words.
For those who remember the film War Games, the two young adults were able to access the game simply by learning tidbits about the author of the program. “Joshua” is the critical fact our young hackers unveiled. This single word was both the identifier and the password. A simplistic form of Identification which some may confuse with Authentication.
Our driver’s license number, credit card numbers, passport number, social security number, employee number, email address or other aliases; are identifiers. These values are and should have remained, simple means of linking someone to the person who initially registered on a web site.
We then link these identifiers to a means of Authentication, an Authenticator. We then use the authenticator combined with the identifier to assure Identification. The recent NIST 800-63 standard defines the strength of an Authenticator. The simple reality the authenticator can be a combination of things you know, things you have, and things you are. Combining these factors create different strengths of Authentication.
Back in the day, a password, if properly constructed, was a very strong means of authentication. Unfortunately remembering numerous and unique passwords is unmanageable.
One of the issues we face is how so many entities, companies, and other enterprises have taken the identifier and allowed it to also become a means of Identification, a secret.
As soon as a simple number or string of letters designed as public information, to be shared with others; became a means of Identification we created an untenable situation.
The Identifier should not be the Authenticator
I was asked to look into the value of the EMV Secure Remote Commerce Specifications. In the first section they wrote:
“1.1 Background … While security of payments in the physical terminal environment have improved with the introduction of EMV specifications, there have been no such specifications for the remote commerce environment. …”
This statement caused a bit of angst. It caused me to think of the work to create SET and Visa’s efforts to promote the original version of 3D-Secure. I was further reminded of how difficult it has been to find the balance between convenience and fraud and how merchants are more worried about abandonment than they are about the cost of fraud. Ultimately, it caused me to wonder about the goal of the EMV 3-D Secure specification.
“To reflect current and future market requirements, the payments industry recognised the need to create a new 3-D Secure specification that would support app-based authentication and integration with digital wallets, as well as traditional browser-based e-commerce transactions. This led to the development and publication of the EMV® 3-D Secure – Protocol and Core Functions Specification. The specification takes into account these new payment channels and supports the delivery of industry leading security, performance and user experience.”
The keywords found in the last sentence “the delivery of industry leading security, performance and user experience” suggest these two specifications are searching to solve the same problem.
According to the Oxford dictionary
Security is
- “The state of being free from danger or threat.”
- “Procedures followed or measures taken to ensure the security of a state or organization.”
Authentication is
- “The process or action of proving or showing something to be true, genuine, or valid.”
- “Computing The process or action of verifying the identity of a user or process.“
On this same page, the authors go on to make the following statement
“… there is no common specification to address the functional interactions and transmission of data between the participants.”
This then causes me to wonder about the original ISO 8583 specification, the current ISO 20022 specification, and the subsequent concept of the three-domain model within the 3D-Secure specification. All three of these specifications define the interaction between the participants while not restricting the method of transmitting the data. It seems the authors of the SRC specifications have forgotten history. Or, are they trying to rewrite history.
At this stage, Authentication seems to the most important part of what EMV is attempting to address. But, the focus seems to be more about rewriting history that solving the fundamental problem. We seem to have this desire to take public identifiers and convert them into secrets.
“An industry transition from a dependency on Consumer entry of PAN data can be accomplished by providing an SRC specification that meets the needs of all stakeholders involved.”
These intriguing contradictions beg the question. Why did the authors of the Secure Remote Commerce specification not reference the good work of those that created the 3D-Secure specification and propose an approach unlike EMV? They all are part of the same organization!
Is the goal not to address authentication and Security of the payment transactions, be they instore or on the Internet. I would argue
We allowed the PAN, the payment card identifier, to become a means of authentication
This use of the PAN as both an identifier and an authenticator; reminds me of a hearing of the United States House Committee on Ways and Means May 17th, 2018 hearing on “Securing Americans’ Identities: The Future of the Social Security Number”.
“House Ways and Means Social Security Subcommittee Chairman Sam Johnson (R-TX) announced today that the Subcommittee will hold a hearing entitled “Securing Americans’ Identities: The Future of the Social Security Number.” The hearing will focus on the dangers of the use of the Social Security number (SSN) as both an identifier and authenticator, and examine policy considerations and possible solutions to mitigate the consequences of SSN loss or theft.”
All the witnesses and most of our members of congress accepted and understood the problem. We allowed a simple government-issued identifier to become a means of authentication, in other words, an authenticator. Like allowing the social security number and now also the PAN to become part of how we authentic someone’s identity. We caused these publically available identifiers to become valuable and sensitive PII data.
Cardholder Authentication and Consumer Device Identification
What is clear, as one continues reading the SRC specifications, is the goal is to reduce the frequency of presenting payment credentials on merchant websites.
“Minimising the number of times Consumers enter their Payment Data by enabling consistent identification of the Consumer and/or the Consumer Device”
A very different approach to what the payment schemes do with the EMV based payment process. The authors of EMV saw the PAN as public data, they architected something designed to assure the uniqueness of the card and the ability to positively verify cardholder. Card Authentication and Cardholder Verification.
Why not simply think and focus on the same architecture? Simply change the word “card” to “device” and focus on Device Authentication and Cardholder Verification or as everyone is promoting Multi-Factor Authentication. We simply need to make sure the thing is genuine and the right individual is using the thing. The thing is what the cardholder has – The “what you have” factor. Add a pin/password or better still a biometric to be the second factor the “what you know” or “what you are” factor.
EMV 3D-Secure creates the ability to exploit the “what you have” factor by offering Device fingerprint data to the issuer’s authentication process.
What is a Cryptocurrency or better yet why do we want them
As a member of a committee responsible to develop the agenda for Payment Summit this February in St Lake City, we’ve been discussing a panel on Cryptocurrency. The initial conversation spoke of blockchain and cryptocurrencies and how these two topics, while related, need to be independent of each other.
With an agreement to focus on Cryptocurrency, I began to ask myself, “What is a cryptocurrency”?
Off to the Internet. My computer instantly offered a definition.
A digital currency in which encryption techniques are used to regulate the generation of units of currency and verify the transfer of funds, operating independently of a central bank
-
-
-
- ‘decentralized cryptocurrencies such as bitcoin now provide an outlet for personal wealth that is beyond restriction and confiscation.’
- ‘States will undoubtedly resist the spread of cryptocurrencies.’
- ‘Bitcoin was the first widely used cryptocurrency, but few people know it is not the only one.’
- ‘What does your cryptocurrency allow people to do that they could not do otherwise, and how does it help them do existing tasks more quickly or cheaply?’
- ‘If cryptocurrencies are like other speculative activities, the early players and the big players benefit to the detriment of the late entrants and the small players.’
- ‘As with all cryptocurrencies, price is based on supply and demand.’‘Even with recent fluctuations, the total value of the cryptocurrency is still over eight billion USD.’
- ‘The majority of cryptocurrency activity still appears to be speculative.’
- ‘A cryptocurrency may be hackable, but it can also be really, really, really hard to hack—harder than robbing a bank.’
-
-
The interesting challenge in this definition is the words “operating independently of a central bank”.
In September 2017 the Bank of International Settlement BIS published a report on Cryptocurrencies. This report spoke to the idea of CBCC or Central Bank Cryptocurrency. The authors offered a diagram known as the Money Flower. The flower positions this idea of CBCC within the world of money and argues a Central Bank could easily create a sovereign cryptocurrency. 
The article then goes on to describe a series of examples. As I moved through the document I was drawn to the idea of Digital Currency and once again was compelled to search for clarity. At the same time I noted the recent announcement by China and how the European Union recently suggested the European Central Bank consider just such an investment.
During my research, I was reminded of the work of David Chaum and remembered how early in the growth of Bitcoin someone suggested David could be Satoshi Nakamoto. I am also reminded of my time at Europay and how we explored the use of Chip Cards, given their hardware and cryptographic capabilities, to create a Cash Replacement, Mondex. In parallel with our efforts Visa Cash emerged, Proton, Chip Knip, Chipper and, others emerged. This led me to a BIS report on Electronic Money.
Looking back in history to the early discussions of Electronic Money and read the early views of the European Union and the US Treasury, it reminded me of some of the original concepts and issues. I’m reminded of words like anonymity, traceability, origination, and sovereignty.
Anonymity and the lack of traceability are what criminals and Silk Road Market Place saw as the benefit of Bitcoin. The concepts of origination and sovereignty clearly are key to the thinking of Governments and Central Bankers and critical elements of the origin of Bitcoin, as expressed in the original white paper.
What these cryptographers have created is amazing, yet one worries about who is responsible for and benefits from the origination of Bitcoins, forks of Bitcoins and the multiple cryptocurrencies now in existence.
If we look inside Bitcoin its architecture promotes the idea of mining and allows the successful miner to originate new bitcoins. They argue this is the incentive driving participation. I then wonder about the cost of Bitcoin mining or the cost of Ethereum mining. Does the cost of supporting Bitcoin justify its continued existence? Does the supposed benefit of cryptocurrencies justify the profit earned by the miners who support the work to assure consensus?
As my research progressed I ran into a speech given at a conference and the Bundesbank Money in the digital age: what role for central banks? The article attempts to address three questions:
-
-
- What is money?
- What constitutes good money, and where do cryptocurrencies fit in?
- And, finally, what role should central banks play?
-
The author’s arguments are worthy of consideration. Especially the questions of efficiency and trust.
The question we all must consider
What is money?
Especially in the global and emerging digital market place.
In the end, I remain confused and concerned. Digital Money, Electronic Money, Digital Currencies, Cryptocurrencies, Feit Money, stablecoins and the potential of the distributed ledger clearly are set to disrupt much.
Where are we
Today.
How many passwords are you trying to manage! Does your LinkedIn contact list connecting you to more than 4,000 individuals? Does Facebook, Instagram, and other social media websites inundating you with news and stories about your friends, colleagues and interesting people?
How many cookies have your computers accumulated? How many databases have more information about you than they need? If we search the dark web, how valuable is your data?
Cando seeks to help you manage your data, identity, assets, and relationships.
Philip lives on Sea Island with his 93-year-old father, the Doctor. They pursue travel and Philip keeps his head into what is happening in financial services, blockchain, authentication, digital identity, and, whatever else people seeking to understand the transformation; particularly those in the identity and payments space.
What is happening means we can unlock our hotel rooms, cars, and homes from our phones. Our security system iwill be another app we have to find on our phone.
Instead, we need an intuitive assistant seeking to simplify our lives by taking on repetitive tasks like driving, working inside a data table or simply opening up the house for the season.
Normalizing data and performing the analysis capable of earning value is the name of the game. Management is about stimulating a team to work in the mutual interest of the organization. Executives define the strategy and articulate the vision in a manner conducive to success.
Cando seeks to help you manage your assets and relationships. Assets those places and things you use doing your daily life and those interactions you have with people and entities seeking to serve, sell and partner with you.
Then there are friends who we expect to be part of our lives and therefore have privileges and access capabilities.
All of this with a target of selling integration services to the top million and simply assuring each person has an identity thus serving the bottom billion. ultimately earning $1 per year per user to simply be there when it all breaks and you wish to restore your digital life.
At the core, your digital security will be based on the use of cryptography and sophisticated matching algorithms designed to assure anyone that you are that one individual in the populatations of the universe.
What You possess, What You Are, What You Claim … Your Certificates
NCCOE NIST Multi-Factor Authentication
What you Possess — The Thing
What you Are — You
Your Relationships
Responsibilities
Authority
Advice
— Secrets
My Certificates
World Wide Web Consortium
FIDO Alliance
Global Platform
The Trusted Computing Group
- EMVCo
- ISO
- ANSI
- ABA
Future interests
- Artificial Intelligence
- Machine Learning
- Nature Language Interface
- Predictive Analytics
Identifiers, Tokens and Authentication
Often times I have wondered why everyone is so enamored with Tokens and Tokenization. Some time ago I begged the question of the broken token in a presentation to the Smart Card Alliance.
My premise is simple.
Identifiers are not authenticators. Replacing the identifier with a token as a result of turning an Identifier, the PAN, Social Security Number or other identifying index value, is a bandage on a festering mistake.
What we need to do is address the challenge of authentication in a convenient and frictionless way. Having to protect an identifier was the issue that created PCI and the whole issue of PII data. The Identifier should not need to be protected. It was and still should be an index and means of recognizing the relationship the relying party has with you. The authentication function is to make sure the person linked to that identifier is you!
User name: Identifier
Password: *********
Was not a bad start. Single factor authentication “what you know”.
Given the number of relying parties we all maintain relationships with, it is time to retire the password; Introducing “what you have” a secure thing (be it a chip card, Fob, Mobile Phone or Personal computer) and exploit the power of cryptography. Then add a second factor, a password or PIN, is a great first step. Changing the PIN or Password to a Biometric is a great leap into a truly secure environment.
The Key is to embrace the first factor “What You Have” a true token.
SCA Workshop Tokenization - 2015
We are here to help you figure out the right approach for your organization.
Multi-Factor Authentication – Faster Payments and the Immutability of a Transaction
Karen Webster
CEO, Market Platform Dynamics
President, PYMNTS.com
Karen,
Last week in your publication I read the article Deep Dive: Security In The Time Of Faster Payments and I had to offer the following thoughts:
The concept of Multi-Factor Authentication is based on the idea of layering multiple authentication techniques on top of each other.
We typically speak of three factors “What You Have”, “What You Know” and “What You Are”.
When we think of “What You Have” we think of a “Thing”. An object that cannot be replicated or cannot be counterfeited.
An object “a secure computer” that can be upgraded and made more secure as threats like Quantum emerge.
A unique object with a False Reject Rate FRR and a False Accept Rate FAR approaching zero.
In the physical world “the thing” is a card or passport. You will remember our first discussion, we came to agree the “secure computer” embedded inside provides a future proof mechanism. In the digital world, we depend on Cryptography. This Thing, inside our computers, mobile phones and other technologies; many refer to as a ROE “Restricted Operating Environment”. Technology people may call it a Secure Element, a SIM, an eSIM, a TPM, a TEE, an eUICC or even Security in Chip. Companies like ARM specialize in creating the design of these things and silicon manufacturers embrace and license their designs.
Today these connected devices (be they: personal computers, identity & payment cards, FOBs, mobiles phones, bracelets, watches and hopefully every IoT device) need to be secured. This array of cheap ~$1 security circuitry provides a place to create and/or store private keys & secrets keys, perform cryptographic functions and assure the integrity of the BIOS and software being loaded or currently running in these computers.
Think Bitcoin for a second. The key to its architecture is the Private Key associated with your store of coins. Lose it and they are lost. Many people store these in hardware, based on the use of a ROE.
The second factor is all about proving that you are present. Behavior, location, PIN, fingerprint or passwords are second or even third factors, be they something you know or something you are.
This is what FIDO and what WebAuthN is all about. Especially since they introducing the security certification regime. This is what the Apple Secure Enclave is and Samsung and others embed into their devices. This is what we put into payment cards, government identity cards and the Yubico keys we see various enterprises embracing. This is what Bill Gates started talking about in 2002. BILL GATES: TRUSTWORTHY COMPUTING
As we move to Faster Payments we must move to Secure payments. Immutability and irrefutably become key requirements. To achieve this goal I suggest we need to understand one fundamental security principle.
The First Factor
is Something(s) You Have
My Thing(s)
The Second and Third factors
Prove You Are Present
Storing Biometrics in the Cloud
Creates a Honey Pot
And, begs questions of Privacy
Let me identify myself to My Thing.
Then let My Thing
Authentication my presence to
The Relying Party (Bank or Credit Union)
NYTimes: Transaction Costs and Tethers: Why I’m a Crypto Skeptic
Transaction Costs and Tethers: Why I’m a Crypto Skeptic https://nyti.ms/2NYYSdw
As a technologist with an understanding of cryptography and very aware that in order to remain secure and tamper proof we increasingly increase the complexity of the work to assure the integrity of what we are using cryptography to protect. I wonder why so many people got so excited about Bit coin and Blockchain. As I have written before the cost to assure the integrity of the ledgar. Be it the original work to calculate the nonce or the subsequent work to confirm that the nonce the miner calculated was the right one, there is a need to spend money buying work specific computers, renting or building a facility to houses these work units and the power to cool and run these computers.
Mr. Krugman properly outlines the challenges. He effectively focuses on two issues. The cost and the idea of tethering.
It is this need to identify the value of the coin. Governments help to stabilize their defined currency. The intrinsic value or use of Gold, establishes its value.
Understanding and being able to clearly articulate how cryptocurrencies are valued and how then can achieve the stability necessary to support commerce is essential. This is what tethering is about. How do we establish and more importantly share the nature of the valuation.
The case for Identification and Authentication
As we continue to explore the case for Identification and Authentication I share the below article.
What is becoming clear is standards are being embraced.
In the Payment space
Will it be W3C WebAuthN, 3DC and Webpayments or EMVCo SRC & Tokenization?
My guess depends on if standards bodies can play well together. EMV (contact or contactless) will remain the many stay for physical world commerce, until the App takes over the Omni Channel shopping experience. then the merchant will properly authenticate their loyal customer and use card on file scenarios for payments. The question of interchange rates for CNP will see a new rate for “Cardholder Present&Authenticated/ Card Not Present.”. In time when a reader is present I can see an out of band “tap to pay” scenario emerging using WebPayments and WebAuthN.
In the identity space
I contend the government and enterprise market will go for a pure identification solution with the biometric matched, in the cloud, in a large central database. In order to maintain a unique and secure cloud identity, they might probably make use of various opportunities that come their way (you can hover over at this website to learn more).
However, does that mean it includes what you know username, email address or phone number? Maybe! If it is simply the captured image or behavior, then it is a 1 to many match. If it is with an identifier, it is classic authentication with a one-to-one match.
In the pure authentication space where the relying party simply wants to know it is the person they registered. Then, the classic FIDO solutions work perfectly and will be embedded into most of our devices. Additionally, the use of a visitor sign in sheet synced with the security database could expedite the sign-ins of visitors. It could also see its applications with employee log authentication and verification. Or, as we’ve seen with some enterprises, the relying party will embrace U2F with be a FIDO Key, like what Yubico and Google recommend.
The classic process needs to be thought about in respect to what can be monetized.
- Enrollment = I would like to become a client or member
- Proofing = Ok you are who and what you claim, we have checked with many to confirm your Identity – This is where federation comes in.
- Registration – Verification = Ok, now we confirm it is you registering your device(s)
- Authorization & Authentication = Transaction with multiple FIDO enabled relying parties using your duly registered authentication.
How Microsoft 365 Security integrates with the broader security ecosystem-part 1
by toddvanderark on July 17, 2018
Today’s post was coauthored by Debraj Ghosh, Senior Product Marketing Manager, and Diana Kelley, Cybersecurity Field CTO.
This week is the annual Microsoft Inspire conference, where Microsoft directly engages with industry partners. Last year at Inspire, we announced Microsoft 365, providing a solution that enables our partners to help customers drive digital transformation. One of the most important capabilities of Microsoft 365 is securing the modern workplace from the constantly evolving cyberthreat landscape. Microsoft 365 includes information protection, threat protection, identity and access management, and security managementproviding in-depth and holistic security.
Across our Azure, Office 365, and Windows platforms, Microsoft offers a rich set of security tools for the modern workplace. However, the growth and diversity of technological platforms means customers will leverage solutions extending beyond the Microsoft ecosystem of services. While Microsoft 365 Security offers complete coverage for all Microsoft solutions, our customers have asked:
- What is Microsofts strategy for integrating into the broader security community?
- What services does Microsoft offer to help protect assets extending beyond the Microsoft ecosystem?
- Are there real-world examples of Microsoft providing enterprise security for workloads outside of the Microsoft ecosystem and is the integration seamless?
In this series of blogs, well address these topics, beginning with Microsofts strategy for integrating into the broader security ecosystem. Our integration strategy begins with partnerships spanning globally with industry peers, industry alliances, law enforcement, and governments.
Industry peers
Cyberattacks on businesses and governments continue to escalate and our customers must respond more quickly and aggressively to help ensure safety of their data. For many organizations, this means deploying multiple security solutions, which are more effective through seamless information sharing and working jointly as a cohesive solution. To this end, we established the Microsoft Intelligent Security Association. Members of the association work with Microsoft to help ensure solutions have access to more security signals from more sourcesand enhanced from shared threat intelligencehelping customers detect and respond to threats faster.
Figure 1 shows current members of the Microsoft Intelligent Security Association whose solutions complement Microsoft 365 Securitystrengthening the services offered to customers:
Figure 1. Microsoft Intelligent Security Association member organizations.
Industry alliances
Industry alliances are critical for developing guidelines, best practices, and creating a standardization of security requirements. For example, the Fast Identity Online (FIDO) Alliance, helps ensure organizations can provide protection on-premises and in web properties for secure authentication and mobile user credentials. Microsoft is a FIDO board member. Securing identities is a critical part of todays security. FIDO intends to help ensure all who use day-to-day web or on-premises services are provided a standard and exceptional experience for securing their identity.
Microsoft exemplifies a great sign-in experience with Windows Hello, leveraging facial recognition, PIN codes, and fingerprint technologies to power secure authentication for every service and application. FIDO believes the experience is more important than the technology, and Windows Hello is a great experience for everyone as it maintains a secure user sign-in. FIDO is just one example of how Microsoft is taking a leadership position in the security community.
Figure 2 shows FIDOs board member organizations:
Figure 2. FIDO Alliance Board member organizations.
Law enforcement and governments
To help support law enforcement and governments, Microsoft has developed the Digital Crimes Unit (DCU), focused on:
- Tech support fraud
- Online Chile exploitation
- Cloud crime and malware
- Global strategic enforcement
- Nation-state actors
The DCU is an international team of attorneys, investigators, data scientists, engineers, analysts, and business professionals working together to transform the fight against cybercrime. Part of the DCU is the Cyber Defense Operations Center, where Microsoft monitors the global threat landscape, staying vigilant to the latest threats.
Figure 3 shows the DCU operations Center:
Figure 3. Microsoft Cyber Defense Operations Center.
Digging deeper
In part 2 of our series, well showcase Microsoft services that enable customers to protect assets and workloads extending beyond the Microsoft ecosystem. Meanwhile, learn more about the depth and breadth of Microsoft 365 Security and start trials of our advanced solutions, which include:
What is EMVCo goal with the release of their SRC framework
October 2017 EMVCo published version 1.o of their Secure Remote Commerce Technical Framework. Today I decided to read and appreciate what they are trying to accomplish and then consider how it ties into what I remember and think we need to do moving forward.
Clearly the challenge links back to the now infamous New Yorker Cartoon.  We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card.
We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card.
We then developed something called SET or Secure Electronic Transactions and unfortunately the payment networks were not willing to allow Bill Gates and Microsoft to earn 0.25% of every sale for every transaction secured by SET he proposed to build into Microsoft’s browser. Without easy integration into the consumer browser, the challenges of integrating SET into the merchant web pages and the Issuer authorization systems caused this effort to fail the death of some many other noble but complicated attempts to create a means of digital authentication.
Next came 3D-Secure, a patented solution Visa developed. It offered what was considered a reasonable solution to Cardholder authentication. Unfortunately, given the state of HTML and the voracious use of pop-ups, the incremental friction, led to abandon shopping carts and consumer confusion. Another aborted attempt at Internet fraud mitigation.
Yet 3D-Secure was not a total failure. Many tried to enhance it, exploit it and avail themselves of the shift of liability back to the Issuer. Encouraging consumer engagement and adoption was futile in some markets mandated and cumbersome in others.
Now let’s consider what EMVCo is attempting to do with their Secure Remote Commerce Technical Framework. As I started to read, I ran into this:
“As remote commerce becomes increasingly targeted and susceptible to compromise, it is important to establish common specifications that protect and serve Consumers and merchants.”
Clearly the authors do not have institutional memory and cannot remember the various attempts alumni of these same organizations spent time on and encouraged many to invest in their implementing. Clearly this lack of historic context will leave some pondering the purpose of this paper.
I then read this sentence and reflect back on a recent hearing on “Social Security Numbers Loss and Theft Prevention” in front of The House Ways and Means Subcommittee on Social Security
“Over time the Consumer has been trained to enter Payment Data and related checkout data anywhere, making it easy for bad actors to compromise data and then attempt fraud.”
Once again, I stand troubled by how the Payment Data clearly printed on the face of the card and especially the PAN, 11-19 digits, designed to simply be an identifier, was converted into an authenticator. Like the social security number, the drivers license number, the passport number and your library card number, the PAN and other “Payment Data” was never designed to be an authenticator. It was meant to be data a merchant could freely record.
The secure features of the card now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC”
now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC” 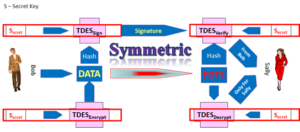 were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
As I began to appreciate the scope of this document, the term “Consumer Device” becomes critical. I began to wonder if a PC is a consumer device or if a consumer device is only something like a mobile phone, watch or other like appliance. Fortunately, later in the document, the definition clears up any confusion created by the earlier use of this term.. This said, I then wonder about the difference between what they define as Cardholder Authentication and Consumer Verification?
After reading through all the definitions, I ponder why the authors had to change terminology? Why could they not embrace known and recognized nomenclature. Do we need a new vocabulary?
I wondered:
If this is another attempt to create a revenue stream for the payment networks?
Or, is this the effort of a “closed standards” body to reduce the potential value of the W3C WebPayments activity?
In search of an answer to this last question, I found this discrete comment inside the SRC FAQ.
9. Are any other industry bodies working in this area?
EMV SRC is focused on providing consistency and security for card-based payments within remote payment environments.
EMVCo aims to work closely with industry participants such as W3C to capitalise on opportunities for alignment where appropriate.
Having read bits and pieces of this and the WebPayments efforts one does wonder what is EMVCo trying to do. We shall see?
Why do we need Tokens and Tokenization
Recently I was directed to a link http://paymentsjournal.com/tokens-work-because/ and wanted to write the author Sarah Grotta. As I wrote the message crystallized in my head and maybe as this prior post already discussed, this idea of tokenization made me cringe.
I contend that Tokens exist because we turned the PAN Personal / Primary Account Number, like we turned the SSN Social Security Number, into an authenticator. One can must ask the question. How can a random value (an identifier) become an authenticator and remain secure?
EMV works because it renders the Card unique, hence addressing the question of counterfeit, by employing the first factor of the classic MFA Multi-Factor Authentication concept “What You Have”. EMV defined a common set of secrets and digital credentials; securely stored in a Secure Element or Chip Card.
“What You Have”. EMV defined a common set of secrets and digital credentials; securely stored in a Secure Element or Chip Card.
We here in the United States decided not to implement the second factor, the Personal Identification Number or PIN, for a variety of reasons. Hence, why Lost and Stolen remains an issue or weakness in the American Card Payment environment.
Biometrics are emerging and could solve for the assurance of cardholder presence. The challenge is how to effectively (cost and convenience) locate the biometric sensor and facilitate the matching of the sensors output to the persons registered biometric. Let alone, how does one make sure the right persons biometric was registered and associated with the device.
In the mail order / telephone order, now cyberspace, we did not replicate merchant authentication, the first factor – “What You Have. The card,  once was secured with things like the magnetic stripe, using CVV1, the Hologram and the other physical features. We simply shifted the liability to the merchant and called it a “card not present” transaction.
once was secured with things like the magnetic stripe, using CVV1, the Hologram and the other physical features. We simply shifted the liability to the merchant and called it a “card not present” transaction.
People can claim all sorts of goodness because of tokenization. They can talk about how the EMVCo’s tokenization framework describes the use of tokens in device and domain specific scenarios. All of this, an issuer, could have done; if they, like some did, simply issued another number, a PAN, to the wife, bracelet, watch, ring or whatever other permutation they deemed appropriate. They can talk about dynamic data. yet what they often forget to include when they use the words “Dynamic Data” they are really talking about a cryptographic value as described in EMVCo Book 2.
Yes, this does mean the question of how the PAN and its digital credentials get deployed; has to be addressed. This said, GSMA with EPC did offer some thoughts, last decade, when they described the Trusted Service Manager
Instead handset oligopolies replaced the MNO with the their Mobile Pay wallets. They working with the ![]()
![]() Payment Networks and focused on control and the creation of income. They, as monopolist will, have created barriers, restricting others from offering comparable services. The TSP now becomes this restrictive service that guarantees the power of companies like
Payment Networks and focused on control and the creation of income. They, as monopolist will, have created barriers, restricting others from offering comparable services. The TSP now becomes this restrictive service that guarantees the power of companies like 
 Apple and Google, supported by their friends, the payment network operators.
Apple and Google, supported by their friends, the payment network operators.
The original article also spoke of the PAR; another data element merchants, processors and the industry, will have to invest in supporting.
I ask the question.
If we had assured the authentication and verification of every payment transaction
Using Multi-Factor Authentication
Why did we need to turn the PAN into a dynamic value?
My contention, simply use the appropriate level of cryptography.
 If the Issuer or their processor is in control and understands basic EMV and Cryptography, then securing the PAN is not an issue.
If the Issuer or their processor is in control and understands basic EMV and Cryptography, then securing the PAN is not an issue.
Consider household financial management. If each member of a household has a unique PAN; budget, tax preparation and understanding who spent what where is a lot easier. The husband,wife and children should have their own unique PAN, stored in the clear in their devices and on their card.
The real requirement, my personal devices, including my payment card, simply need to be linked to one PAN their Personal Account Number, associated with the individual. The PAN Sequence number could easily allows each device to be uniquely identified, if necessary. The card and devices becomes the carrier of your identifier. A thing that can be authentication as something you have.
Here is where the second factor comes in. Is the person presenting the PAN the rightful and authorized individual? All this required, is assurance to the shareholders that the presentment of the PAN is a unique and authorized event. This is best achieve by using either something you know or something you are to bind the individual to the instrument carrying the Identifier.
Yes, a bit of friction to assure the consumer they are securely paying for what they want to buy
Since the World Wide Web came of age and merchants saw its potential. The question of how to secure the  Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure.
Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure.
Each, an attempt to provide some means of Authentication and Verification.
Each introducing a level of friction as a means of security.
This is the problem. The market did not start by emphasizing the need for security by educating the consumer. The industry needed to help the consumer understand they should care and want to securely pay for what they intend to buy.
Instead:
- The Zero Liability Policy was adopted.
- The merchant was more than happy to sustain a degree of lose (fraud) in exchange for sales and profits.
The result, as all anticipated would happen, was blissfully ignored and eventually they cried out about.
Fraud migrated to the weakest point
Just like water finds its way to the lowest point.
EMV, introduced in the Face to Face card present environment, pushing the bad guys: be they criminals, state actors and terrorists to find alternate another channels for their financial gain.
be they criminals, state actors and terrorists to find alternate another channels for their financial gain.
EMV and now the recently published WebAuthN and FIDO specifications create effective mechanisms for Consumer Authentication.
Let us please remember – the PAN, a user name, your social security number or your email address are excellent Identifiers. They should not be authenticators and they are not a means of “Identification”.
Let us also remember, the term Identification means that one is assured of the irrefutability of identity.
The big question:
- Why did we have to get rid of or replace the PAN?
- Why did we and continue to need to invent and invest in all this addition overhead?
- Why did we not simply address authentication?
Some will argue the challenge of using the PIN or a Password, as a means of Verification, is because it is to hard to remember. Especially, if each password people use to access website, services, building, has to be unique. Some will argue imposing friction to add security is not convenient. Others will remind us that security is and has been a necessity since the beginning of time.
Why didn’t we when we created this great new digital shopping mall?
Bottom line each of the devices used to present or acquire the PAN, must be capable of authenticating the identity of the authorized presenter, in both the physical and virtual world.
At least these are the views of someone who believe history provides a baseline for tomorrow and tomorrow must be designed as a function of where you want to be, knowing where things came from.
Block Chain. Hype, the future, fiction or a scheme?

Yesterday over a lunch I ended up synthesizing my thoughts into a neat little package that I would like to start sharing.
Those who extoll the virtues of Block Chain speak of:
- Immutability – Cryptographers and mathematicians will prove the immutability of the algorithms, at least for now
- Distributed – as long as there a multiple diverse and competing stakeholders this is great
- Trustless – I keep asking the same question Who defines the content of the Block or the ledger or the transaction? Everyone ultimately agrees a body of people and I sit there and say that sounds like a governance model. Be it a currency, a ledger, a contract two or more must agree to structure format, content and rules.
- Consensus – Great as long as we never exceed the 51% participation by A party, the model is superb.
I then think about Work and the reward
Be it Proof of Work or Proof of Stake the entities that do the work are intermediaries and will want to be rewarded for their work.
Then one must think about shifting from a solution that rewards someone with a coin to a system that rewards someone with a fee earned.
I then reflect on Bit Coin and its use of Proof of Work

Coins are created by the party who figured out the Nonce, as a reward for solving the cryptographic puzzle.
- Once they earned 25 Bitcoins
- Today they earn 12.5 Bitcoins
- At some point, in the future, the reward will be cut in half and then half again
The challenge
As the chain gets longer the work gets harder
As time moves forward and the number of coins in circulation grows
The reward decreases in notation value.
Sounds like inflation is built in.
Real estate, computers and electricity cost money.
As the work expands the costs increases!
In conclusion
There is inherent Inflation built into the Bit Coin Model.
We simply replace intermediaries with Nodes and Miners.
We require a governance model so we simply change the governor to another.
People will want to be paid for the work they do to build the block or assure consensus of the chain
What is truly revolutionary?
The math, ok maybe.
Immutability, it is done today with cryptography, without a block chain.
Multiple copies of the ledger spread around the world. Yes, as long as we address confidentiality.
We have governance, sure we can always elect a new government
What is so magical?
of Tokens and Things
Things, now there is a big word.
- I am a thing
- It is a thing
- I know a thing
- Things must therefore be anything
The dictionary rambles on about things.
Tokens, What is this thing?
 Tokenization why is everyone so excited?
Tokenization why is everyone so excited?
Tokenization and the Search for Identity
The belief in tokens emerges from the need to address security in a world where an identifier becomes an authenticator.
The PAN on the front of a ID-1 Card defined and governed by the International standard IS)/IEC 7812-1. When it was originally conceived there was no desire to turn the PAN into PII Data.  They simply wanted the PAN to be an index, “a pointer” “an Identifier”, to an account, or relationship, a card issuer (financial institution) created between itself and the cardholder. In our quest to take advantage of the telephone, the mail and ultimately the internet as a set of sales channel. The Payment System actors agreed if the card acceptor “merchant” would accept liability. Then, they could simply use the PAN, the expiry data and cardholders name to effect a card payment. This acceptance of liability was an acknowledgement they could not inspect the card and verify that the physical security features where present, hence the token was not present to be authenticated.
They simply wanted the PAN to be an index, “a pointer” “an Identifier”, to an account, or relationship, a card issuer (financial institution) created between itself and the cardholder. In our quest to take advantage of the telephone, the mail and ultimately the internet as a set of sales channel. The Payment System actors agreed if the card acceptor “merchant” would accept liability. Then, they could simply use the PAN, the expiry data and cardholders name to effect a card payment. This acceptance of liability was an acknowledgement they could not inspect the card and verify that the physical security features where present, hence the token was not present to be authenticated.

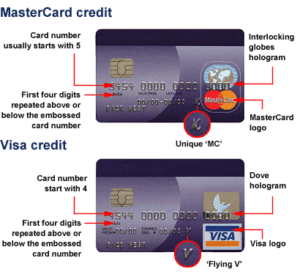
Society in its infinite wisdom followed another path with the Social Security Number. A number originally designed to act simply as a unique value representing each person here in the United States. Unfortunately, as is often true, we took the short cut, assumed this number, stored on hundreds of databases and recorded on an equally large number of forms, could be used to authenticate that you the individual was present.
mysteriously and without thought society allowed these numbers to take on values they where never intended to assume. They became “secrets” number that if known to another could be used to take over our identity. They can make payments in our name. They can apply for loans and take over our financial assets without the true individual being the wiser.
Those that seek to profit and do not share societies morality find ways of taking advantages of our desire to cut cost and reduce friction. They create near perfect counterfeits of these tokens, they take advantage of our naivety and they seek to disrupt and profit.
We could do as we have often done in the past – replace the token with a token. We could claim by tokenizing these identifier with another vale we were adding layers of security. We argued that if this new tokenized value could only be used by that merchant or with that physical device; security would be restored. The question how long would that new think provide the security its champions claimed it would offer.
A Shift from Check-out to Check-in will reshape the way merchants engage with their consumers
Think Uber, think order ahead, think account on file. With these ideas in your mind think engagement and Omni channel. Then consider the need of merchants to assure revenue by delighting and engaging with their customers in meaningful ways. Their focus, increasing basket size, more frequent visits and loyalty; in other words increased sales.
Then remember, Check-out is about friction, payments and long lines. These characteristics merchants seek to eliminate, reduce the cost of and enhance the experience around.
If we think Check-in, using big-data, geo-location, BLE, facial recognition, consumer centric apps and other techniques, we can image a world where human and device based personal assistants engage with the merchants loyal customers in a friendly, informed and satisfying way.
For payment people this means we need to remember that merchants want lower cost payments and friction-less check-out.
Bottom line, for loyal customers solutions that retain the payment credentials securely in the cloud. For one time and infrequent customers, they will look to incent loyalty and registration or simply accept classic means of payments e.g. cards.
This drive to move from recording a loyal customers visit to engaging when the customer arrives or better yet when they are doing their research is what we the consumer seek.
We are all about saving time, enjoying life and satisfying our needs and wants. Merchants that focus on the customer and their shopping experience will succeed and prosper./ Those that do not focus on delighting their customer will learn.
Words all bound to who we claim to be – How do we identify ourselves on the Internet or in Cyberspace?
Identifier – Something you create or are provided to digitally identify yourselves. Identifiers are things like an alias, user name, email address are examples.
Identity – This is who we are or wish to represent ourselves to be. These are attributes and information about: where we live, who we work for, which banks we have relationships with, who our friends are, which clubs we belong to, our certified skills, what schools we graduated from, which country(s) we are citizens of, our LinkedIn profile, Our Twitter handle, our Facebook identifier, our phone number … . It is the sum of the attributes we can and will share with others, be they individuals, governments, entities or organizations; as we establish relationships and prove to them who and often what we are.
Authentication – The method we employ to assure that you, based on the identifier presented, are who we (the relying parties) thinks you are. You are the person the relying party accepted when you registered that Identifier as how you would digitally identify yourself. By itself the method of authentication should not allow another party to be able to determine anything about your identity. Privacy is the goal. FIDO Alliance and W3C have defined standards to support authentication.
Verification – The process of confirming that the secret or biometric match the secret or biometric that where originally registered to that Identifier.
Identification – A means of authentication that is bound to your identity. A EMV payment instrument “Chip and PIN”, a PIV card, an electronic passport, a membership card, a drivers license, a national ID are all forms of identification issued by a party that should be trusted to have performed a proof of the individuals Identity, based on a defined and often published criteria.
This particular word, for many, has an alternate meaning. In the biometric community they see Identification as the ability to use a biometric to determine ones Identity. This is achieved by performing a one (the person present) to many match (persons registered). The goal is the same, bind Identity to the mean of Authentication by using the Biometric as the Identifier.
Proof – The method a relying party or an individual uses to validate your claim of a specific Identity. In many cases this is achieved by relying on knowledge of another party. The relying party accepts the due diligence to proof your claimed identity was done to their satisfaction by another party. This other party is often referred to as a Trusted party. This effort to proof the identity of an individual is linked to words and acronyms like KYC “Know Your Customer”, ID&V “Identity and Verification” and Self Sovereign Identity. We classically assume that documents provided by a Government e.g. drivers License and Passports are a solid proof of the claims asserted on those same documents.
In a digital world this is the most important element of a how we as people, entities, governments and corporations can be assured that you are who we believe you to be.
I am once again am reminded of the 1994 New Yorker Cartoon
Identity and Payments
A presentation provided at the December United States Payment Forum to an audience of 50 plus individuals
Deciphering Digital – Your Phone is Your Wallet
Today Wednesday October 18, 2017. I had the opportunity to provide the closing keynote to the EPCOR Annual Payments conference. Today, I was reminded of the reality that payments is not only about cards it is the engine that fuels the revenue of a financial institution. ACH, Wires, Cards, checks, transfers and even cash are revenue earning services; our community banks call payments.
My speach was about the future and focused on the evolution of our phone in this new digital age we all must learn to embrace.
IoT 2017 Payments Tuesday Afternoon
Continuing the learning and commentary
IoT Payments 2017 – Austin TX October 10th and 11th
Context-based payments
- Security has always been an after thought as devices were deployed and solutions were developed. Security needs to be built in as a fundamental layer in these emerging IoT objects.
- Growth in fraud in online payments is typically a result of the deployment of EMV.
- As we think about Dash buttons and the myriad of other interfaces that can access a card on file style shopping and payment experience we must think anew about security.
- What is context? Our digital footprint as we go through our daily lives.
- The growing number of IoT devices can help to establish context, which can then be used as a fourth factor in an authentication scheme.
- It is all about acquiring data and building a profile, your context.
- What is the unique identifier that links all the objects to the individual.
Bridging the Security Gap
- Brightsight a lab focused on security looking at both physical a logical security at both the operating system and application layer.
- The IoT landscape is a world of objects where to goal is sell fast. No security has been built in and the attack surface is broad and wise.
- The fear of who is able to access the vast array of data available through these connected devices.
- Security is about managing risk. Risk evolves over time. Therefore security must evolve to stay ahead of the current level of risk – continuous improvement.
- In the world of IoT who will define the security requirements and who shall pay becomes the key question.
- We should consider using Common Criteria as a baseline for the security of IoT devices.
- Bottom line – the implementation of security is all about the developer and the use of already certifies components e.g. Integrated Circuit and the Operating System.
The key to top of wallet
- Changing our top of wallet card is not something we are driven to do.
- So many sites drive to Card on File
- The objects will end up with an embedded payment within
- There is a hierarchy of needs
-
BASIC WANTS & NEEDS
-
MASS & PERMITTED RECOMMENDATION
-
SOCIAL & RELEVANT 1REFERRALS
-
ON-BEHALF
As he speaks of On-behalf a document produced back in 1996 must be found
- Will the IoT evolution increase consumption, Maybe?
Wearables 101
- What is the connectivity
- Where are the credentials stored
- Is it a configurable device relative to which credentials
- Types
-
Contactless cards and devices
The mobile ecosystem introduces the token requestorA solid overview of the world of tokenization
- The tap experience with a wearable is an interesting design experience.
- A wearable is smaller and much more personal.
- As seen from the payment networks
- Like a card
- Mobile device (secure element)
- HCE
- Wearable are in market today
- Wearable are in market today
Risk Based Payment Security
- Beth took a walk through the history of payment acceptance
- The Internet of Things creates the tsunami effect on our world of risk. Both scary and empowering.
- Risk is or was always about the balance between security and convenience.
- Tokenization moves the authentication responsibility from the Issuer to the payment brand. In this case who has the responsibility in the event of. Has the threat of penetration moved to the payment brand.
- The move to mobile devices as a result of the inherent transaction security to the registration and ID&V process.
- Interoperability and security standards who controls? IoT is not a market. It is a collections of vertical and closed environments.
- We need to agree on a common set of security values not necessarily on a common standard.
- When we think about the wider question of the how and what of security. We need to think about the security of the device and the cloud. We need to remember it is also about the ability to spoof and acquirer the credentials of a user.
- Security must be designed in from the beginning.