When I received this video
I wondered if prudish Americans would appreciate the continental humor.
For me and now I speak from my heart, mind and soul. I remember well going to Jones Beach with two special ladies. They made it clear they would bath as they wished and I needed to accept and not be some leering male. I then remember traveling to Paris and seeing beautiful people adorning those typical French round advertising pillars. The French simply use the beauty of the human body to promote perfume or some other sensual thing. After I moved to Europe and we venturing, children in hand, to the beaches of Holland, France, Spain and Italy we learned to simply accept. Even more telling, I attended an ITUG conference at a 5 star hotel in Budapest and ventured down to the spa.
I wonder why Americans are bound up in a moral turpitude.
We are either far to the right or fair to the left.
Arnold Schwarzenegger was interviewed today and argued our country must come back to the center. Morality is key to why we are so far apart. So many on the right so many on the left. Little room to find accommodation in the middle.
We purport to be a country of law, a country of freedom and a country of choice. Yet we are tangled up in imposing rules to govern choice. I read of how in Virginia back in the 30’s they attempted to ban interracial marriage and discovered that most of the population had some of Pocahontas in them. I then think about those that are marching today. They argue that the friends who died, are more important than the rights of those who want to let anyone bear arms. Yet that small minority, the NRA, seems to have control over the decisions of the peoples’ representatives. If we believe we can ban the mixing of races, yet we are unable, as the majority, to ban the type of arms, weapons, people are allowed to own, what are we!
Arnold today spoke of education, health and the environment.
If we want to Make America Great Again then why do we allow our system of education to stigmatize people based on where they live. Why do we not assure each citizen the right to equal education. He reminded the audience this country ranks 39th in the world. He said that regulating diversity was ridiculous. He argued that by offering equal education, we enable people equal opportunity. His argument made perfect sense. Using local property taxes to fund education, ultimately means where you live, hence your family income, defines who has opportunity to excel. If we want to remain the greatest country in the world and assure all citizens equal opportunity, then, we must invest in education.
Bottom line Education is the key to Making America Great Again.
Health, there are 4 living doctors in my family. Through my kinship to them, I have heard and listened to them speak of the issues with our system. For my simple mind the problem begins with Capitalism. It is all about big corporations wanting to profit from their skills. It is about insurance companies wanting to minimize risk (expense) by minimizing the amount of care they have to pay for. I am familiar with social medicine. Three countries provided me personally with exposure to how it can and does work.
Yes, if you can afford care in this country, you will get the best care.
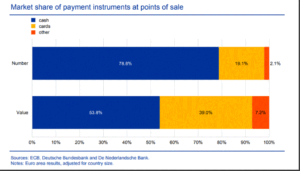
The challenge, every American cannot afford care, without insurance. And, if everyone is not insured then those that are the least wealthy and healthy are without. For me this graph tells the whole store. 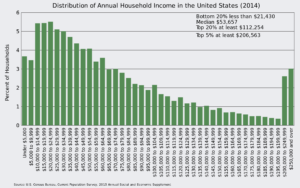
I am personally paying insurance under a Cobra plan. For Selma and I, one household, it costs 1,291.43 a month $15,520.92 a year.
We all need universal care. We need to require everyone to pay into our health system. This is the only way will we assure affordable care for all. How does one build such a system, I suggest, it must resemble what Switzerland has built.
Minimum care paid through taxes. Supplemental care, each households responsibility.
Next is our environment. Once, we worried about pollution and the quality of our air and water. Now, we must expand our thinking. We must remember we are stewards of this earth and realize our consumption of the earth’s resources will affect the balance of the earth and its ecosystem. We are here to protect the earth for our children and for the children they will bring into this world.
We can argue all night long about the science. What we do know is that if we change the balance of anything there is a result. The classic appreciation of cause and effect. We the USA, with less than 20% of the word population, recently were responsible for most of the carbon dioxide injected into the atmosphere. Today this no longer is true. But, we recently pulled away from helping to lead the world to a better place. Instead our President wants us to return our sources of energy back to those non renewable earthly resources, coal and oil. We all know they pollute!
Finding reusable means of generating energy, is good politics. The Economist March 17th 2018 had an excellent special report on the politics of energy.
If we do not embrace renewable sources of energy and reduce our dependence on Oil and Coal, we will no longer be the great national we are and seek to remain.
As I write, I am remember learning about the Fourth Industrial Revolution. As the first sentence so aptly says it
“The Fourth Industrial Revolution is changing everything – from the way we relate to each other, to the way our economies work, to what it means to be human”.
We must properly harness technology.
- Education is the key.
- Our environment can only benefit.
- Healthcare will simply become more efficient
In the end we will improve everyone’s life.
Yet?
As Adam Smith best explains, our global economy (yes we are a global economy), can only be successful when we view it as a closed system.
We must appreciate that we are all part of the whole. Only when we each give to our own abilities, will we find balance. If we allow labor arbitrage to take jobs away; then, those who lose their jobs must find new ways to contribute. They cannot expect the system to sustain them!
Yet they should expect those that profit to help re-educate.
Why am I writing. What am I asking.
Maybe to share. Maybe to speak out.
There is one other topic on my mind. Those who understand the loss of a friend in Parkland are speaking out, they are marching in Washington and around the country to get people to listen and vote to arrest the stupidity of how the second amendment is being mis-interpreted.
For me the key is found in the first part of that amendment
“ A well regulated Militia, being necessary to the security of a free State,
In my opinion, what resulted from District of Columbia v Heller (2008) was an unreasonable interpretation of the second amendment. I would suggest United States V. Cruikshank (1876) and United States v Miller (1939) are a better interpretations. Those interpretations, in my opinion, are not influenced by the political influence of the NRA and gun manufactures’. Their and the NRA’s focus is to market, sell and protect their right to profit! They are not focused on assuring the free state has a well regulated militia. If they were, they would insist on training, education and the formation of groups – in other words militias.
The second phrase
“The right of the people to keep and bear arms shall not be infringed.”
For me, this is why Switzerland ends up with guns in every home. The people are members of the armed forces. They are “The Militia”. They belong to a “well regulated” group of people focused on “the security of a free state”. They are trained. They understand the purpose of these weapons. The militia, in other words the people, can determine if there are mental issues and exclude those individuals as they are evaluated and introduced to their responsibility as a member of the militia of the people.
Looking back on the histogram above many of you are or will be part of the upper 10%. We are the ones most gifted. We therefore must be the ones that are the most interested in making this world is a better place. Simply accepting the way it is, means we are not working together to make the world, this country, a better and more equal place.
Going back to the video we must assure our freedoms. We must focus not on how we expect people to live. We must remember why we became a nation.
“We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness. — That to secure these rights, Governments are instituted among Men, deriving their just powers from the consent of the governed”
Our founders made it clear, we each have the right to life, liberty and the pursuit of happiness.
The way I interpret what we attempted, as a nation, to establish; is a body of people, a society, that respects each of our individual rights and seeks to protect each individuals right to life, liberty and the pursuit of happiness. If I want to expose myself in the comfort of a community that enjoys this way of life, as long as we do not imping on your rights, why not? Slavery, Blue laws, various interpretations based on the desire to impose your will on me is not why we declared independence. It is not what our constitution attempted to create.
I want clean air, clean water, not to see your litter in public view and be able to drink alcohol and/or smoke marijuana. I want the ability to see a doctor when I need to and not worry that I cannot afford to. I want to be able to to see all children attend school, knowing they will get a great education. I also do not want to worry that some lunatic will buy assault rifles and use these weapons reserved for a well regulated militia to kill children while they are at school. I want to be able to attend a music festival and not worry that some person up in some hotel room is capable of buying an arsenal simply to kill people.
Yes we should have the right to hunt and protect ourselves. Assuming we are trained and capable and more importantly are of stable mind and body.
We must each remember the ten commandments Exodus 20 or simply put the two found in Matthew 22:37-40, Mark 12:29-34 and Luke 10:25-37
Most importantly we must read, appreciate and be the Samaritan described in Luke 12:30-37.
Each of us is bestowed with skills and abilities. We have the funds to be able to help drive policy we have the responsibility to assure each is given the right to life, liberty and the pursuit of happiness.
These are my beliefs.
I hope those reading my thoughts are willing to respect them and share theirs. Only if we engage in discourse can we assure ourselves life, liberty and the ability to pursue happiness.
Obviously to avoid spam I do moderate comments. As long as there is no profanity, I will not censor anyone’s comments. I am also posting the existence of this Blog on Twitter and Facebook. In those environments and as Cambridge Analytica has demonstrated, these thoughts will simply expand the public’s awareness of my habits, patterns and thinking.
Respectfully,







 and a Eurocard was all we needed to buy and enjoy life. Electronic payments was the norm, paper checks were a rare oddity and cash, well yes there was a very present grey economy.
and a Eurocard was all we needed to buy and enjoy life. Electronic payments was the norm, paper checks were a rare oddity and cash, well yes there was a very present grey economy.

 We could go on and talk about how Apple saw the possibility of a 0.15% income stream from ApplePay based mobile payments and how the EMVCo tokenization framework evolved to support their desire to protect the Apple Brand.
We could go on and talk about how Apple saw the possibility of a 0.15% income stream from ApplePay based mobile payments and how the EMVCo tokenization framework evolved to support their desire to protect the Apple Brand.






 Tokenization why is everyone so excited?
Tokenization why is everyone so excited? They simply wanted the PAN to be an index, “a pointer” “an Identifier”, to an account, or relationship, a card issuer (financial institution) created between itself and the cardholder. In our quest to take advantage of the telephone, the mail and ultimately the internet as a set of sales channel. The Payment System actors agreed if the card acceptor “merchant” would accept liability. Then, they could simply use the PAN, the expiry data and cardholders name to effect a card payment. This acceptance of liability was an acknowledgement they could not inspect the card and verify that the physical security features where present, hence the token was not present to be authenticated.
They simply wanted the PAN to be an index, “a pointer” “an Identifier”, to an account, or relationship, a card issuer (financial institution) created between itself and the cardholder. In our quest to take advantage of the telephone, the mail and ultimately the internet as a set of sales channel. The Payment System actors agreed if the card acceptor “merchant” would accept liability. Then, they could simply use the PAN, the expiry data and cardholders name to effect a card payment. This acceptance of liability was an acknowledgement they could not inspect the card and verify that the physical security features where present, hence the token was not present to be authenticated.