President Donald John Trump
White House
1600 Pennsylvania Avenue
Washington, DC 20500
United States of America
July 6, 2018 Ref. Mine thoughts and Those of My Canadian Friend
Dear Mr. President, Tuesday, June 19, 2018
Mr. President as an American who had the opportunity to work in five states (NYC, NJ, Georgia, MN, & NC), four countries (USA, UK, Belgium and Canada), two super cities & three major cities (Manhattan, London, Brussels, Toronto and Atlanta); I have had the chance to see and hear about our great country from multiple angles and perspectives.
August of 2008, after 23 years away, I returned home, after spending 7 years in Toronto; in a 35-foot motor home. Parked across the river from the town of my birth, near Liberty State Park and with the Statue of Liberty as my morning view. I learned about and had to accept the misfortunate of the recession. A recession resulting from the creation of those mortgage backed derivatives. Compounded by the devious behavior and the greed of the speculators, I brand “Wall Street”.
I will remember September 15th 2008, the day Dick Fuld, who I had worked with while with Shearson Lehman, made that fateful announcement. Newly returned to the United States, I had to learn about what 8 years of Republican control of the Executive branch of our country had achieved, what the heightened religious fault lines across this country were and the anxiety of the terror emanating from the middle east had done to this nation. Like 9/11, we were swept into another spiral of despair and anger.
We have been a great nation; for most of my life, we were seen as the great white hope. A country willing to stand up to tyrants, bullies, jihadists and anarchists. A great nation capable of reaching any part of the world. Strength built on the military and diplomatic respect we established with both our enemies and most importantly our allies and friends. I will admit I am an urban dweller. I have lived a good life. I found success in the world of Financial Services and the application of technology. I do not appreciate the struggle those in the manufacturing and agricultural economy feel.
Words like labor arbitrate, outshore resources and outsourcing are familiar. What stands behind these words has much to do with the state of our nation and the situation in most of the developed world. It is the result of these actions so many people in middle America feel left behind.
In 1982, when I first began to build a Wall Street trading room for Bankers Trust, I saw how Shareholder value not Stakeholder value, had become the most important factor within our capitalistic system.
People, be they customers or employees, no longer mattered. What I learned and frankly was disheartened by is that the only thing that matters anymore is the returns, as seen from the superrich executives, the shareholders’ and the financial analysts’ perspective. We had become a nation focused on the balance sheet and the quarterly report.
Yes, I have my views and recommendation as to the state of this nation and what we need to do to make sure we remain the great nation we live and believe in.
If I think about the economy. We do not need to bring the manufacturing or restart coal mining. We need to embrace the fact that our nations wealth is now in our service economy. A national of American healthcare works taking care of the sick and wounded, American call center operators serving Americans, American programmers developing systems for our digital world, American innovators creating for all and American business leaders is what we need. Yes, we need to rebuild our infrastructure and address public transportation. Yes, since 2010 our economy is growing, I hope we can sustain that growth and assure the people good wages, good jobs and a bright future.
If I think about healthcare. I felt the most exposed when I returned to the USA and discovered I did not have healthcare. I was unemployed and did not have the funds to simply go out and buy an individual healthcare plan. Healthcare was a big topic on the news as Washington worked through what ended up being a terrible mess of a healthcare plan. In my immediately family there are 5 Doctors. four practicing and one just finishing med school. As you can imagine it has been a topic of conversation since I was very young. Now the conversation is about how broken our system is. I take the view of someone who has lived within multiple national health programs. It bothers me that this great nation cannot figure out how to assure the health of every American, affordably.
If I think about education. We as a nation should make sure that every person living in this country is WELL EDUCATED. There should be no excuses. There should be no bias. Property taxes tend to pay for primary schools. It is primary education we must make the best in the world. Unfortunately, the way our system works the poor get poor schools – the rich have great schools. We need to figure out how to assure everyone an equal chance with a GREAT PRIMARY EDUCATION. Your idea of apprentice programs is exactly what our primary education system should assure exist. Everyone should be able to walk into the world with a set of skills at age 18. Graduating from primary school everyone should be able to go our and find a job, join an apprentice program, join the military or decide to invest in higher education. A college degree should not be required to succeed. A University education should be there to allow those who are gifted the ability to excel.
If we think about the environment. Please listen to the majority of scientist who know we are affecting the environment. It is the pollution we create and the materials we inject into our environment that is responsible for the state of our environment. We the people and our corporations are responsible for all the islands of floating plastic, all the Carbon, Sulphur or who knows what we inject into the atmosphere and all those chemicals we pour into our rivers and oceans. We must continue the good work, you and I saw, when we cleaned up the rivers around Manhattan. Environmental work making it possible to breath the air in central park, swim in the Hudson river or taking a cruise from the East 23rd street mooring, you used all those years ago.
If we think about our military and our role as the defender of peace. We need a strong and well-funded military. Not too much and not too little. We need to make sure we have strong alliances. Frankly, Mr. President, I would hope we would discourage other country form investing in military hardware. Our goal should be to have the best. Our goal should be to watch and gain as the cost of maintaining the peace and avoiding war and conflict falls to zero.
If we think of our role as a global leader. What more is there to say. We need to be diplomatic. We need to pursue the growth of democratic societies. We need to focus on quelling violence and protecting human rights. We need to be the partner everyone wants to have on their side and the enemy those who seek to do us harm; do not want to enter into a conflict with the United States of America, because they know they will lose, before they start.
If we think about the Statue of Liberty. She stands proud in the harbor of New York beaconing people to our shores. Yes, we need to manage the flow of immigrates into this great nation. We must remember those that come seek the opportunity this nation promotes. We need to accept all with kindness, grace and dignity. When necessary only then should we return those, who have not followed the published policy, back from where they came, gently.
We must also remember they come because they know they can find work. As long as employers can hire people who do not have the right to work in this nation they will come. Stop American companies from hiring illegal immigrants and they will stop coming. Simple economics – reduce the demand will eliminate the supply.
If we think of our nation and its people. You must lead by example. You are the President of all of us. Whatever our color, race, religious views, social position, economic situation or sexual preferences you are the President and you must be an example for our children and our nation.
We do not want our children to believe lying is OK. We do not want our children to believe bullying is ok. We do not want our children to shun someone because they are different. It is your role to bring the parties together, to lead the left and the right back to the middle ground and restore civil discourse.
On these next pages is the note my Canadian friend wrote.
Given you are into social media I will also post this via Twitter, Facebook and on my own website.
Yours sincerely,
Philip Andreae
Dear Mr. President:
I am writing you as an outsider, someone who has always loved your country for the values it represents and has fought for.
I was going to write you to express my appreciation for your efforts to dial down the risk of nuclear war by meeting with Kim Jong-Un and initiating a peace process which should make life less stressful for our Asian neighbours as well as for us here in North America.
But the euphoria didn’t last long, only because of the children. The ones separated from their parents at the US/Mexico border. You see them on either the front pages of the major newspapers or on the various media outlets and you know, this is not going away.
Children are ever the fly in the ointment which disturb our individual and collective conscience. Riding in the back seat of a car downtown on any New York or Toronto street and they are the ones asking, ‘Why is that man sleeping on the sidewalk?’ or ‘See that military vet begging in front of Dunkin Donuts? Is that the way we treat our soldiers?’
The children are invariably the ones who ask how did we let our world become so uncaring that we confine the elderly to institutions where nobody visits them, or send our street youths to jail when they had no opportunity to succeed?
And now they are congregating at the border asking ‘why are we being separated from our parents?’ ‘Is that how America treats its most vulnerable people?” ‘Isn’t this the land of the free, the land of opportunity, the land who has inscribed on its Statue of Liberty:
“Keep, ancient lands, your storied pomp!” cries she
With silent lips. “Give me your tired, your poor,
Your huddled masses yearning to breathe free,
The wretched refuse of your teeming shore.
Send these, the homeless, tempest-lost to me,
I lift my lamp beside the golden door!”
However, it has occurred that there are now over 2000 children separated from their parents along your southern border, you are the one person who can fix this. It doesn’t mean you have to allow them all in – which would be my preference – or decide to send them all back home.
That’s not the issue. The issue here is the trauma your administration and by extension, all freedom loving grown-ups, are foisting on innocent children for which there are lifelong implications.
That is the issue which you alone can change.
Unzero the Zero in Attorney General Session’s Tolerance Policy, so the one thing that isn’t being tolerated is the confinement of children in cages and gymnasiums separated from the people who love them and who have risked everything, in the hope of a better life here.
Again, whoever is to be blamed for things ending up the way they are now is not the issue. The issue is – what is happening now is wrong, and you are the one person who can make it right.
I know as someone who relies on Christians of sincere conviction to help shape the bigger decisions one has to make in life, the one thing devout Christians all agree on is that God so loved the world, not that we would put our children in cages, but love them in such a way that regardless of who they are or where they are from, our treatment and care for them would reflect God’s thinking about them, that ’theirs in the kingdom of God.’
I can assure you, that kingdom does not include a cage. Nor should ours.
Thanks for hearing me out on this.
Sincerely,
John Deacon


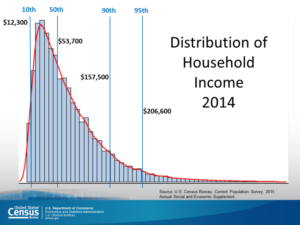




 We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card.
We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card. now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC”
now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC” 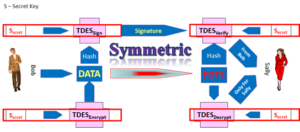 were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
 Apple and Google, supported by their friends, the payment network operators.
Apple and Google, supported by their friends, the payment network operators.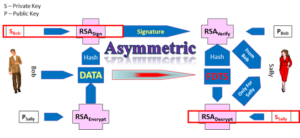 If the Issuer or their processor is in control and understands
If the Issuer or their processor is in control and understands  Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure.
Card Not Present space, this question of cardholder presence, has not been properly addressed. Visa and MasterCard (when they were not for profit associations) created the utility of the Card Verification Result CVV2, CID or CVC2 which would be printed on on the card and not part of the magnetic stripe, the problem the bad guys could still steal the card or get hte card number and capture CVV2.. MasterCard and Visa then created SET, 3D-Secure and now, as for profit owners of EMVCo, are proposing, maybe even will mandate, the industry implement EMV 3D-Secure. be they criminals, state actors and terrorists to find alternate another channels for their financial gain.
be they criminals, state actors and terrorists to find alternate another channels for their financial gain.