Category: Payments
Payment Card Construct and Dual Interface Deployment
Payment Card Construction
The discussion focused on the construction of the sandwich. Four layers. Clear front laminate to protect the ink, front with the banks design and brand logo, back with the banks back design and a clear laminate with the magnetic stripe integrated into it.
To enhance design additional layers may be added, such a metal foil.
These four sheets are then bonded together, at 120 degrees, in sheets of 21, 36 or 48 or other various sheet sizes. Next step punch out cards, add hologram and signature panel.
For a standard EMV card the next phase is to mill and embed the module with the chip inside. Last, the manufacturer typically loads the O/S & EMV application into the integrated circuit card.
When we move to dual interface caed, this process is modified to add an inlay, with the antenna embedded within. This inlay is inserted in the middle of the sandwich and during the embedded process the contacts exposed on the base of the module are connected to the antenna in the inlay.
Next step, personalization, when the appropriate data is loaded into the chip, along with the encoding of the magnetic strip and printing and/or embossing of the cardholders, name, expiry date, cvv2 and other information onto the card.
Contactless or Not That is a Question
Contactless NFC acceptance and dual interface issuance is all about the chicken and the egg. Who will go first? The merchant or the issuer? Each need each other. Both are wondering about the incremental value.
- Faster transactions – Yes
- Less cash – maybe
- More revenue – good question!
Given these questions and observations, one can only wonder.
Financial Trade Groups Write to House Leaders in Support of Data Breach Notification Bill
https://bankingjournal.aba.com/2018/02/financial-trade-groups-write-to-house-leaders-in-support-of-data-breach-notification-bill/

The associations expressed support for draft legislation released by Reps. Blaine Luetkemeyer (R-Mo.) and Carolyn Maloney (D-N.Y.) that would create a level playing field of nationally consistent data protection standards and post-breach notification requirements. This bill would not create duplicative standards for financial institutions which are already subject to robust standards, but rather extend similar expectations to other sectors that handle consumer data.
“The goal of the bill is simple — raise the bar so that all companies protect data similar to how banks and credit unions protect their data, and create a common-sense standard to ensure consumers receive timely notice when a breach does occur,” the groups wrote.
The draft bill contains a provision that recognizes the existing, effective regulatory framework for covered financial sector entities. While the provision was intended to prevent banks and credit unions from being subject to duplicative notification requirements, it has been the target of recent negative campaigns circulated by the National Retail Federation and the Retail Industry Leaders Association, which incorrectly suggested that banks do not notify customers of breaches on their computer systems and The ads from the retailer groups also mischaracterize and exaggerate the share of data breaches occurring at banks and credit unions while omitting their members’ (higher) share of data breaches.
The financial trades refuted the notification assertion, noting that “banks and credit unions have long been subject to rigorous data protection and breach notification practices for financial institutions to follow,” and that in the event of a data breach, banks and credit unions work continuously to communicate with customers, reissue cards and enact measures to mitigate the effects of fraud. They added, however, that “no solution will work unless everyone has an obligation to take these steps.” For more information, contact ABA’s Jess Sharp.
The management of our identity
A few weeks ago I learned of the Sovrin Foundation a foundation interested in establish a concept to support the idea of a self Sovereign means of identity.
As an advocate for stronger forms of identification and more important Authentication I am pleased to have received your response today.
Back in 1993 I was part of Europay and drove the creation of the EMV specifications as a form of Authentication and frankly reflecting back a strong form of Identification with the Trust Anchor being the Financial institution issuing the card and the foundation anchor being the payment network that the issuer used to assure acceptance globally.
In 2013 I joined the Board of the FIDO Alliance and eventually become the Secretary of that Board.
Today I am engaged with a company called IPSIDY, that is promoting and selling Identity as a solution.
Clear the conversations we are having include:
- Device based versus centralized biometric authentication
- Identification based on a central repository of Biometrics or a simply identifier linked to a means of authentication
- Claims and assertions one points (URL) to or those that one has in their own possession
- Repositories or Distributed databases of information
- Privacy of attributes and rights to defining what can be shared
When I ask about the future of Sovrin, I hear people saying great concept how does it scale to be useful.
This, as was my experience in the Payments world, is the challenge of a two sided market
- Consumer – Merchant
- Individual – Rely Party and those seeking attributes and proofs of identity
The challenge is developing a value proposition and more importantly critical mass that will excite both sides of the market to want to participate.
To further complicate developing the market is the challenge of the “Go To Market” strategy. Who does one partner with given that the usefulness to the citizen/consumer is predicated on the number of parties or places this solution, token or Identity with a set of sharable attributes can be usefully used.
This is the question this is the challenge.
A Shift from Check-out to Check-in will reshape the way merchants engage with their consumers
Think Uber, think order ahead, think account on file. With these ideas in your mind think engagement and Omni channel. Then consider the need of merchants to assure revenue by delighting and engaging with their customers in meaningful ways. Their focus, increasing basket size, more frequent visits and loyalty; in other words increased sales.
Then remember, Check-out is about friction, payments and long lines. These characteristics merchants seek to eliminate, reduce the cost of and enhance the experience around.
If we think Check-in, using big-data, geo-location, BLE, facial recognition, consumer centric apps and other techniques, we can image a world where human and device based personal assistants engage with the merchants loyal customers in a friendly, informed and satisfying way.
For payment people this means we need to remember that merchants want lower cost payments and friction-less check-out.
Bottom line, for loyal customers solutions that retain the payment credentials securely in the cloud. For one time and infrequent customers, they will look to incent loyalty and registration or simply accept classic means of payments e.g. cards.
This drive to move from recording a loyal customers visit to engaging when the customer arrives or better yet when they are doing their research is what we the consumer seek.
We are all about saving time, enjoying life and satisfying our needs and wants. Merchants that focus on the customer and their shopping experience will succeed and prosper./ Those that do not focus on delighting their customer will learn.
DIY the Cyber Guy a conversation about Bitcoin and EMV
https://www.voiceamerica.com/promo/episode/104814
A interesting discussion withDavid the the Cyber Guy. We spoke of the inherent risk of Bitcoins and the essential issue of the secret and a BitCoin folders resoponsibility to make sure they never lose the secret.
We then wandering off to talk about EMV or Chip and Pin.
Always a pleasure to work with David.
Words all bound to who we claim to be – How do we identify ourselves on the Internet or in Cyberspace?
Identifier – Something you create or are provided to digitally identify yourselves. Identifiers are things like an alias, user name, email address are examples.
Identity – This is who we are or wish to represent ourselves to be. These are attributes and information about: where we live, who we work for, which banks we have relationships with, who our friends are, which clubs we belong to, our certified skills, what schools we graduated from, which country(s) we are citizens of, our LinkedIn profile, Our Twitter handle, our Facebook identifier, our phone number … . It is the sum of the attributes we can and will share with others, be they individuals, governments, entities or organizations; as we establish relationships and prove to them who and often what we are.
Authentication – The method we employ to assure that you, based on the identifier presented, are who we (the relying parties) thinks you are. You are the person the relying party accepted when you registered that Identifier as how you would digitally identify yourself. By itself the method of authentication should not allow another party to be able to determine anything about your identity. Privacy is the goal. FIDO Alliance and W3C have defined standards to support authentication.
Verification – The process of confirming that the secret or biometric match the secret or biometric that where originally registered to that Identifier.
Identification – A means of authentication that is bound to your identity. A EMV payment instrument “Chip and PIN”, a PIV card, an electronic passport, a membership card, a drivers license, a national ID are all forms of identification issued by a party that should be trusted to have performed a proof of the individuals Identity, based on a defined and often published criteria.
This particular word, for many, has an alternate meaning. In the biometric community they see Identification as the ability to use a biometric to determine ones Identity. This is achieved by performing a one (the person present) to many match (persons registered). The goal is the same, bind Identity to the mean of Authentication by using the Biometric as the Identifier.
Proof – The method a relying party or an individual uses to validate your claim of a specific Identity. In many cases this is achieved by relying on knowledge of another party. The relying party accepts the due diligence to proof your claimed identity was done to their satisfaction by another party. This other party is often referred to as a Trusted party. This effort to proof the identity of an individual is linked to words and acronyms like KYC “Know Your Customer”, ID&V “Identity and Verification” and Self Sovereign Identity. We classically assume that documents provided by a Government e.g. drivers License and Passports are a solid proof of the claims asserted on those same documents.
In a digital world this is the most important element of a how we as people, entities, governments and corporations can be assured that you are who we believe you to be.
I am once again am reminded of the 1994 New Yorker Cartoon
We must take care when we speak or sell the power of that which may not be
I always enjoy reading the words David writes.
This particular post creates a moment to reflect. As we consider the implications of the Fourth Industrial Revolution, we must remember the significance many have attributed to Artificial Intelligence. Those two letters AI are clearly key to the what, why and wherefore of the change ahead.
Clearly machines that work faster, search deeper and are capable of studying vast realms of data are changing the nature of so much. Simply consider the risks to our security cyber hackers and terrorists wrought on this world or the shenanigans many claim the Russians use to disrupt as they explore and exploit the power of social media.
Moreover as we look afield many industries are being disrupted: movies, books, music, news … to name few. Outsourcing and robotics is changing the nature of work and the skills necessary to compete and ultimately survive to enjoy the pleasures available in our increasingly digital world.
David makes the point that the intelligence Isaac Asimov and other science fiction envisioned has not yet emerged. I think he is right. The message I take aware -we who market these solutions should walk forward with care.
People are clearly feeling threatened by the change impacting their towns, families and livelihood.
We must be mindful that complexity breeds confusion. Confusion drives disillusion. This then causes people to react, often in nonsensical ways.
Take On Payments
Federal Reserve Bank of Atlanta
How Intelligent Is Artificial Intelligence?
Posted: Nov 27, 2017 10:51 am
At the recent Money20/20 conference, sessions on artificial intelligence (AI) joined those on friction in regulatory and technological innovation in dominating the agenda. A number of panels highlighted the competitive advantages AI tools offer companies. It didn’t matter if the topic was consumer marketing, fraud prevention, or product development—AI was the buzzword. One speaker noted the social good that could come from such technology, pointing to the work of a Stanford research team trying to identify individuals with a strong likelihood of developing diabetes by running an automated review of photographic images of their eyes. Another panel discussed the privacy and ethical issues around the use of artificial intelligence.
But do any of these applications marketed as AI pass Alan Turing’s 1950s now-famous Turing test defining true artificial intelligence? Turing was regarded as the father of computer science. It was his efforts during World War II that led a cryptographic team to break the Enigma code used by the Germans, as featured in the 2014 movie The Imitation Game. Turing once said, “A computer would deserve to be called intelligent if it could deceive a human into believing that it was human.” An annual competition held since 1991, aims to award a solid 18-karat gold medal and a monetary prize of $100,000 for the first computer whose responses are indistinguishable from a real human’s. To date, no one has received the gold medal, but every year, a bronze medal and smaller cash prize are given to the “most humanlike.”
Incidentally, many vendors seem to use artificial intelligence as a synonym for the terms deep learning and machine learning. Is this usage of AI mostly marketing hype for the neural network technology developed in the mid-1960s, now greatly improved thanks to the substantial increase in computing power? A 2016 Forbes article by Bernard Marr provides a good overview of the different terms and their applications.
My opinion is that none of the tools in the market today meet the threshold of true artificial intelligence based on Turing’s criteria. That isn’t to say the lack of this achievement should diminish the benefits that have already emerged and will continue to be generated in the future. Computing technology certainly has advanced to be able to handle complex mathematical and programmed instructions at a much faster rate than a human.
What are your thoughts?
By David Lott, a payments risk expert in the Retail Payments Risk Forum at the Atlanta Fed
Europe Led the way with EMV yet Europe appears to prefer cash
Europeans still love paying cash even if they don’t know it
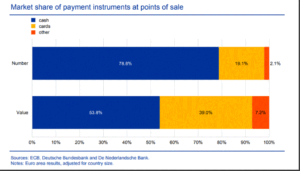
Interesting to reflect on how much we allow Europe to lead as we think about EMV and the technology we use to secure our payment cards. Maybe American’s need to embrace and take over the management of these key standards that drive an economy.
Identity and Payments
A presentation provided at the December United States Payment Forum to an audience of 50 plus individuals
USPF-Dec-2017- Identity_and_PaymentsWill Wal-Mart Pay surpass Apple Pay, Samsung Pay and Android Pay
Walmart Pay to surpass from pymnts.com – from the Washington Post. – and another
To open the news and find more than a press release in fact true commentary describing the success of a merchant mobile payment solution. This is big news and speaks to the value of loyalty and the power of largest global merchants willingness to focus and innovate.
Thinking about cards
In 1991 I had to learn the difference between million dollar transactions and hundred dollar transactions. As I came to explain, when telling my life story, I had to shift my thinking from 100 transactions at a million to 1,000,000 for a hundred. This transition took me from capital markets to payment cards.
Today, I wonder about the future of the ID-1 based payment card? A piece of plastic 3 3/8 x 2 1/8 with rounded corners.
In another blog I spoke of how this ID-1 object became a token responsible to act as the first factor, something you have. Printed, encoded and embossed characteristics were the security features. Today, with EMV as the global standard for payment CARD security; cryptography and the “secure element” replace those physical security with digitally mastered circuitry embedded inside something capable of protecting those secrets cryptography requires. We digitized the payment card. What we now must do is shift our vocabulary to tokens and credentials.
We need to embrace a new way of speaking we need to think about our “Payment Credentials”.
Today, we now tap our phone to pay, we use our phone to browse the internet, we shop & book tickets with apps and we listen to music & watch movies all from this device we apparently use, thousands of times a day. For those of us who remember computers that filled floors, we now are capable of buying more powerful computers, similar in size to those same cards. Think about the Raspberry Pi, a computer almost as small as a card, not quite! Yet!
The embedded secure element integrated inside our payment cards are being integrated into phones, bracelets, rings and things. The question; will they replace the card we are now comfortable with? Yes – maybe? Will we embrace these objects as the new carriers of our payment credentials? Many hope so.
In oder to think about the probability of cards disappearing, one must begin by think about the number of cards now in circulation. In round numbers we can think about 1.2 billion debit and credit cards, 300 million prepaid cards and 300 million retail branded cards. In round numbers, 1.8 billion payment cards. We next must think about our population and how many people now carry cards – 115 million households and 242 million Americans over the age of 16, according to a recent census. We now has a numerator and a set of denominators.
The question then becomes, how many payment cards does an American want to carry and how many payment credentials will an American end up having.
I would argue a debit card and a credit card is all we need to carry in our leather wallet, purse or pockets. Those other payment credentials can easily be accessed from wallets in the cloud or in our digital objects.
Merchants can integrate payment capabilities and focus on factoring their consumer receivables, behind relationships designed to service, thrill and sell. In an App and API enables economy, cards become a burden as the experience becomes the essential component of our lives.
Deciphering Digital – Your Phone is Your Wallet
Today Wednesday October 18, 2017. I had the opportunity to provide the closing keynote to the EPCOR Annual Payments conference. Today, I was reminded of the reality that payments is not only about cards it is the engine that fuels the revenue of a financial institution. ACH, Wires, Cards, checks, transfers and even cash are revenue earning services; our community banks call payments.
My speach was about the future and focused on the evolution of our phone in this new digital age we all must learn to embrace.
A look at the actors that support Internet Payments

The payment landscape is a complex space with an array of stakeholders specializing a focusing on various aspects of the processing of a payment. This diagram is oneof several used to form a backdrop to various educational sessions Philip offers to organizations and executives seeking to identify and position themselves in the payments landscape.
This particular one seeks to help people understand who the key actors to a card not present eCommerce transactions.
IoT Payments Wednesday Morning
Continuation of my running thoughts as I listen and participate at the Secure Technology Alliance.
Role of the TSP
- Wearables a small part of the IoT market and to scale the vendors need to not have to worry about “Payments”.
- Should device manufactures understand payments? Can they?
- The TSP must appreciate its role and what it is not.
- As we look at IoT we need to recognize the scale of the shift from a issuer centric to a consumer centric model. The payment credential carrier no long belongs to the Issuer.
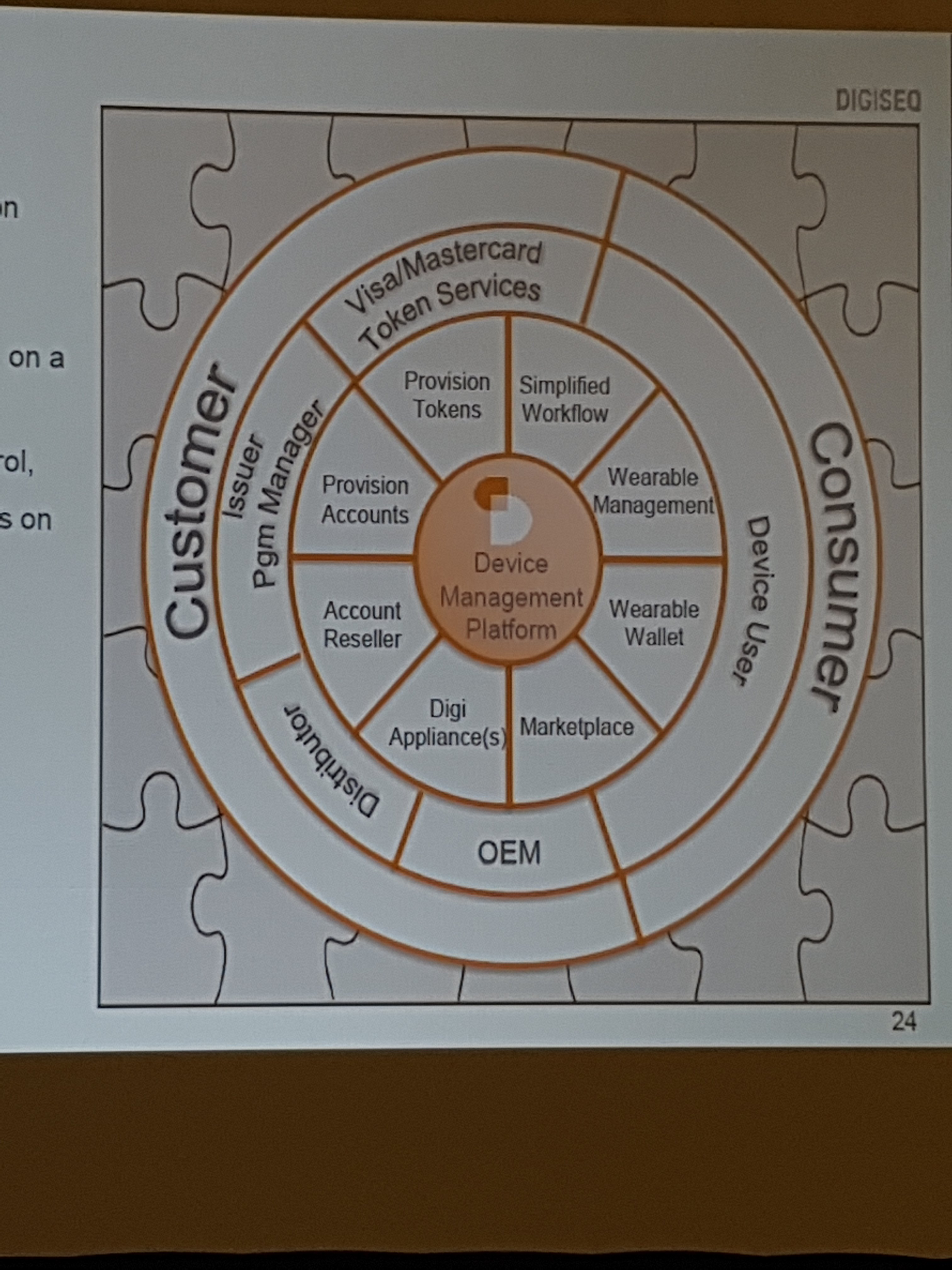
- What is the role of the Token Requestor? It provides a consolidated view for the consumer. It consolidates rhe view of all the edge devices.
- Who is the ultimate revenue source? The consumer? How does one create the consolidated view with so many instances of tokens?
- What is the life of a token? This then leads to the question of the relationship with the manager (issuer) of the Means of Payment.
- With the pre-provisioned credential how does one manage long term life cycle.
Root of Trust
- Is PKi the right approach to the necessary level of trust this emerging environment requires.
- We must remember the complexity of a PKi infrastructure.
- In the payment space the use of secure devices e.g. HSM was mainly on the acquiring side. Now as a result of EMV issuers became much more concerned with keys and key management.
- As we move into a mobile and more broadly connected world the need to assure trust in the software, device whatever.
- This discussion is very much about the value and need for HSMs.
- The question is raised as to the future of PKi given the US Gov’t perspective.
- And, what of the introduction of Quantum Computing and the associated risk to the available cryptographic algorithms and keys?
In-Vehicle Payments
- A car can be used a place to shop, it could pay for service rendered, it can be linked to service providers. NFC/BLE/In-app and Card on File.
- The car can host merchant apps.
- The idea of a POS device in the car leaves me lost. Who is the seller?
Smart Cities and Multi-Modal
- To address smart cities one has to think across the wider context.
- What are the roles the FTA can support, becomes a question of what the cities want.
- Mobility on Demand driven by the needs to reduce congestion and improve life.
- Built on local partnership within the community
- A recognition that a multimodal approach is necessary. A focus on user centric approaches to transport.
Multimodal Payment Integration
- The challenge begins with the fragmentation of the transit environment. It is not transit it is all about Mobility.
- They want a brand and system agnostic solution that is intelligent and can help better manage spend.
- How large is transit, public only, 6,500 transit operators supporting 1 trillion rides per year.
- The roadmap is in development, it is early days.
Wearables – lessons learned
- What ìs a wearable? Do define them based of feature and function. Cloths, jewelry…
- We use a wearable when we need them. Athletic, climate, entertainment or work.
- These electronic wearable needs to consider the use cases that should be integrated into a limited number of devices we would wear.
- Three words – simple – connected – enablements
- How will we enable more specifically load the various certificates we need to access, employ and pay for.
- Interoperability will become the challenge. Do we imagine a world restricted by brand / manufacturer? Or, open to a wide array of designs and capabilities then how do we get there.
-
Secure element
Data management & personalization
Mobile device software integration
Device life cycle managementTokenization as a methodology ans ecosystem is essential to the growth of payment in the IoT space.
BLE of IoT Payments
- The cloud may restrict what could be communicated.
- BLE is “local” allowing secure application management and secure transactions.
Managing Trust and Security
- Identity is the key to much.
- The next question therefore it trust in the Identifier.
- Authentication with what, in what where?
- Life cycle management. How do you know your device been wiped clean of all your credentials.
IoT 2017 Payments Tuesday Afternoon
Continuing the learning and commentary
IoT Payments 2017 – Austin TX October 10th and 11th
Context-based payments
- Security has always been an after thought as devices were deployed and solutions were developed. Security needs to be built in as a fundamental layer in these emerging IoT objects.
- Growth in fraud in online payments is typically a result of the deployment of EMV.
- As we think about Dash buttons and the myriad of other interfaces that can access a card on file style shopping and payment experience we must think anew about security.
- What is context? Our digital footprint as we go through our daily lives.
- The growing number of IoT devices can help to establish context, which can then be used as a fourth factor in an authentication scheme.
- It is all about acquiring data and building a profile, your context.
- What is the unique identifier that links all the objects to the individual.
Bridging the Security Gap
- Brightsight a lab focused on security looking at both physical a logical security at both the operating system and application layer.
- The IoT landscape is a world of objects where to goal is sell fast. No security has been built in and the attack surface is broad and wise.
- The fear of who is able to access the vast array of data available through these connected devices.
- Security is about managing risk. Risk evolves over time. Therefore security must evolve to stay ahead of the current level of risk – continuous improvement.
- In the world of IoT who will define the security requirements and who shall pay becomes the key question.
- We should consider using Common Criteria as a baseline for the security of IoT devices.
- Bottom line – the implementation of security is all about the developer and the use of already certifies components e.g. Integrated Circuit and the Operating System.
The key to top of wallet
- Changing our top of wallet card is not something we are driven to do.
- So many sites drive to Card on File
- The objects will end up with an embedded payment within
- There is a hierarchy of needs
-
BASIC WANTS & NEEDS
-
MASS & PERMITTED RECOMMENDATION
-
SOCIAL & RELEVANT 1REFERRALS
-
ON-BEHALF
As he speaks of On-behalf a document produced back in 1996 must be found
- Will the IoT evolution increase consumption, Maybe?
Wearables 101
- What is the connectivity
- Where are the credentials stored
- Is it a configurable device relative to which credentials
- Types
-
Contactless cards and devices
The mobile ecosystem introduces the token requestorA solid overview of the world of tokenization
- The tap experience with a wearable is an interesting design experience.
- A wearable is smaller and much more personal.
- As seen from the payment networks
- Like a card
- Mobile device (secure element)
- HCE
- Wearable are in market today
- Wearable are in market today
Risk Based Payment Security
- Beth took a walk through the history of payment acceptance
- The Internet of Things creates the tsunami effect on our world of risk. Both scary and empowering.
- Risk is or was always about the balance between security and convenience.
- Tokenization moves the authentication responsibility from the Issuer to the payment brand. In this case who has the responsibility in the event of. Has the threat of penetration moved to the payment brand.
- The move to mobile devices as a result of the inherent transaction security to the registration and ID&V process.
- Interoperability and security standards who controls? IoT is not a market. It is a collections of vertical and closed environments.
- We need to agree on a common set of security values not necessarily on a common standard.
- When we think about the wider question of the how and what of security. We need to think about the security of the device and the cloud. We need to remember it is also about the ability to spoof and acquirer the credentials of a user.
- Security must be designed in from the beginning.
The day came to a close.
Tokenization and the search for Identification and Authentication
These two words began to fascinate me as I began to understand the value of cryptography while working through the goals we established when developing EMV and attempted to secure the payment credentials when used on the Internet.
With EMV we were trying to address the challenge of the fraud (an issuer cost) resulting from the ease of counterfeiting the token of the token which was a token of a token already.
This last broken token is the magnetic stripe on the payment card.
The payment card, in and of itself, is a token. An instrument imbued with physical security features e.g. the hologram and signature panel. Security features the merchant is supposed to check when attempting to allow a buyer, the consumer, to use the payment credential associated with the card to make payment for good and services.
The PAN is just a unique number, another token. This unique number is simply the index, The identifier within the payment credentials, which associates the payment with the underlining source of funds.
The source of funds, the PAN or Token pointing to, is then either a line of credit, prepaid balance or bank account.
The card, the hologram, the magnetic stripe and the printed security features and the PAN had reached the end of their useful life, as security features or tokens. The criminal knew how to compromise the card and associated static data.
As we entered the 90’s, the card as the carrier of the payment credential, with those physical security features, was longer a means of Authentication. These layers of authentication had been compromised. In other words the token was broken!
To address this concern, in 1993 the founders of EMV embraced the chip card and its Cryptographic capabilities. In particular, the use of symmetric and asymmetric algorithms to provide a new set of tokens the merchants (asymmetric) and Issuer (symmetric) could use to Authenticate the unique carrier of the payment credential – the token – the chip card.

On the Internet the challenge is different. The physical features of the card are not easily accessible, hence useless. In 1993, when WWW became the thing of conferences, everyone said lets think of the internet in the same way we allow merchants to sell stuff via mail and telephone. Everyone simply decided and agreed to exploit the acceptance rules agreed on for those other virtual environment, the phone and the mail.
Bottom line, in the world of mail order / telephone order and now a browser; merchant simply agrees to accept the cost of fraud, given the CARD is NOT PRESENT. Worse still how do they prove the right cardholder in present?. For the merchant, given the potential of the Internet, it is was a small price to pay.
Everyone simply accepted that be capturing the data embossed on the front (PAN, expiry date and cardholder name) and the CVV printed on the back of the card and, in some cases, using the power of AVS “Address Verification Service” a modicum of security could be factored in. At least for a time!
SET “Secure Electronic Transactions”, a cryptographic mechanism Visa and MasterCard cooked up, was developed circa 1995-1996 and deployment was attempted. The challenge, the limitations of the then deployed technologies and the inability to provide a reasonably convenient user interface. The problem begins with loading payment credentials into the browser and more importantly figuring out how to use them when shopping.
A set of great ideas foiled by convenience.
Next came 3D-Secure, an invention of Visa. This time the idea was to exploit the power of passwords and secret questions to authenticate the user.
Nice idea, well thought out; but, unfortunately not designed with the consumer in mind.
Another feeble failed attempt to develop a mechanism to authenticate the buyer. Or better put, solve the dilemma the New Yorker so aptly described
“On the Internet nobody knows your a dog”.

All this begs the question – how will we secure payments on the Internet?
3D-Secure 2.0, maybe? Or maybe W3C and the FIDO Alliance have the answer in what is called WebAuthN.
To address this question we must begin by defining the problem.
When we think about payments and we think about shopping on the internet it is all about someone or something {read issuer} agreeing that the consumer will make good on the promise to pay and therefore the issuer is willing to guarantee payment towards the merchant. The challenge, how do we confirm it is the legitimate person seeking to pay with their means of payment.
In other spheres of endeavour it’s about granting access to someplace or some website. In the physical world we have a key that we can insert into the lock or a security device {card} we can insert or tap on a reader programmed to recognize our credential and allow us access.
On the Internet, the use of a physical card with physical security features, numbers, letters, and a magnetic stripe was not feasible. Instead, we ended up employing user names, passwords, and payment encryption. Payment encryption, which secures sensitive financial information during online transactions, offers a crucial layer of protection. The user name – a unique identifier, and the password, a secret, support the identification of the person using the browser or connected device, from somewhere out there.
If we could each create and remember complex secrets, these cumbersome things call passwords. And, more importantly, never share them with nefarious individuals seeking to take advantage of our naiveté. All would be at peace in the world of security and convenience. The problem is expecting you and I to remember the myriad of complex passwords and not get tricked into sharing our secrets.
Is there an answer, I believe so and at Money 2020 October 25 we will be discussing this very topic. Wednesday Morning at 8:30 in the Titian room at The Venetian in Las Vegas on Level 2, join us as we discuss Identity is Fundamental: What You Need to Know About Identity & The Future of Money.
Philip Andreae & Associates is Open for Business
In the News as the Vice President of Oberthur Technologies
Oberthur Technology seeks to educate and support the migration to EMV
An Interview with George Peabody of Glenbrook
From a merchant perspective Oberthur offers thoughts for consideration
Healthcare is in need of secure authentication an Interview with Karen Webster
An Article published by Pymnts.com as we consider the last days before the migration
Digital Identity is what we require to secure our world an interview with Karen Webster
W3C and the WebCrypto Working group considering payments and Same Origin Policy
Why EMV and Why Now with Pymtns.com
A Founders of EMV’s view of the US migration to EMV
Understanding EMV in Our Digital Future an interview with Karen Webster
Counting Down to the migration to EMV
The ABCs of EMV
An interview with the Atlanta Constitution
Interchange fact, fiction and myths
Interchange a word that describes a method that allows cars and truck to move from one road to another. Interchange a
word that describes the exchange of ideas or data between two or more individuals. Interchange a fee paid to an Issuer of a payment card.
It is this third definition that this blog will explore. A fee or income paid to an Issuer of a payment card.
Some would call it a tax on merchants. Merchants who wish to sell products and services to individuals and corporations who wish to pay with moneys loaned to them by a financial institution (credit card) or held on deposit by a financial institution (debit card and pre-paid card). Wikipedia offers the following; Http://en.wikipedia.org/wiki/Interchange_fee. To add to this sound Wikipedia definition, I offer a little story of how Interchange was described to me was a way of helping people appreciate the way interchange has changed over the years.
In 1991 I joined EPSS, a technology company then owned by Eurocard International (50%), Eurocheque International (35%) and MasterCard International (15%). EPSS or European Payment System Services ran and managed a set of technologies designed to support the authorization, clearing and settlement of payment transactions initiated by a payment card being presented to a merchant. We supported both credit and debit card transaction and would when they emerged also supported pre-paid card transactions.
As part of the settlement process we calculated and assured acquirers (merchant bank service provider) were paid, less interchange and scheme fees, for those payment card transactions they had submitted on behalf of the merchants they serviced. Therefore understanding and assuring the accuracy of these calculations were essential to assuring the successful operation of those systems we managed.
In the first few weeks of starting, general counsel sat me down and described Interchange. What I learned is that on a biannual basis we hired a consulting firm, Edgar Dunn; to conduct an anonymous survey of the member organizations, the banks that issued credit cards. Their role was to ascertain what it cost the issuers to support the processing of payment card transactions. Three elements were key to these calculations:
- Cost of Carry – The interest charge or income the bank had to pay or forego in order to to fund payment card transactions conducted on the credit cards they issued to their customers. This cost was calculated based on the reality that the issuing bank paid to payment network (MasterCard, Eurocard or Eurocheque) either immediately or within a few days of submission; and, the fact that credit
card charges are billed to the cardholder periodically. This time between paying the merchant and the card holder paying their credti cards bill was assumed to be about 45 days. - Systems costs – The depreciation of assets and cost of operation of the systems necessary to process these payment card transactions. These systems included those that authorize, in real time, payment card transactions and receive, each evening, the clearing transactions and reconcile the moneys the Issuer had to settle, daily, with the payment network.
- Fraud costs – The loses the issuing bank incurred for payment card transactions where the consumer claimed they did not recognize the charge and the merchant proved that they had accepted the card and followed all the rules and procedures associated with the acceptance of that brand of payment card.
Our consultant then would amalgamate all the data they collected from the issuing members and submit a recommendation of what interchange should be for the next two years. These recommendations recognized that interchange must vary based on two key characteristic:
- Location of Merchant and home country of cardholder
- Global
- Regional
- Domestic
- Nature of transaction
- Card present and electronically read
- Card present and paper voucher with card imprint
- Card Not Present (mail order telephone order and in time eCommerce)
We then discussed how the Issuer earned income from payment cards. I learned; yes for those efficient issuers there were profits, whereas for inefficient issuer they might actual lose money. Bottom line the calculation was designed not to create profits. It was designed to cover cost.
Management then took these recommendations to their board to seek approval. At this stage the boards where a balance view with both the issuing and acquirering institutions represented. Unlike today when it is fundamentally the Issuers that sit on these boards.
In 2002 I joined Visa and again was asked to visit with general counsel to make sure I understood what interchange was. My first statement was that I understood and explained what I had been taught all those years ago. I was informed that although I understood the foundation, things had changed. Two additional components had been added to the calculation and moreover instead of being limited to a few easy to understand categories, the structure of interchange has been MADE complex.
While it still was calculated through the use of anonymous survey of issuers, interchange now included:
- Rewards – this was meant to cover the cost of the reward programs Issuers used to entice cardholders to adopt a particular card product.
- A Reasonable Profit
As to the characteristics used to identify what interchange fee would be earned by the issuer, the original two categories of transaction location and the presence of the card continued. Yet now to complication matters two new ones were added:
- Type of card – In order to justify the addition of the cost of rewards into the formula the payment network attempted to sell merchants
on the idea that corporate cards and premium “Gold” cards where used by people or organizations who would be more loyal, spend more hence more valuable customers for the merchant. - Merchant size and category – This distinction was driven by the reality that certain merchant categories are prone to fraud. But more importantly, certain merchant segments where essential to the expansion of card usage and were known to sue or complain about the cost of interchange.
Interchange had morphed from a cost recovery mechanism to a complex formula that takes into consideration the complexity of the payment ecosystem and a source of revenue to financial institutions.
With all this change there are also challenges. With only two global “4 party” payment brands (Visa and MasterCard) regulators, merchants and politicians seek to manage and control interchange. Words like monopolistic powers are used to describe the way interchange is calculated. Therefore you find lobbyist speaking on behalf of merchants, arguing these fees create excessive profits for the issuer. You here people complaining that the fees and the rules not allowing them to charge consumers for the use of these more expensive payment products, ends up that interchange simply gets embedded into the cost of sale and cash paying customers are seen to be subsidizing card paying customer.
As a prime example Wal-Mart and a consortium of merchants, banded together and successfully won an argument against both Visa and MasterCard. They argued that interchange associated with debit cards processed through the credit card networks should not be the same as credit card interchange given that the cost of carry was near euro. When all was said and done 3 billion dollar was paid by the payment networks to the merchants and their lawyers.
The Australian Central Bank also decided to regulate interchange, although the benefit a reduction in the price did not occur thus the perceived benefit to the consumer was not achieved. Currently the European Union continues to evaluate interchange with the argument that domestic and regional interchange must be the same and that monopolistic powers are used to manage interchange.
Here in the United States Senator Durbin succeeds in imposing significant change to debit interchange.
Interchange will continue to be scrutinizes. My hope, let us return to original definition of interchange and focus on being a mechanism designed to simply cover the issuers’ cost of processing payment transaction and offer a reasonable profit for their efforts.
Let the issuer earn the core of their income through revolving Interest charges, annual card fees and other services paid for by their customer the Cardholder. Why should the merchant subsidize the rewards offered to entice cardholders to take an issuers product without also garnering a demonstrable increase in sales?