https://modernconsensus.com/technology/building-digital-dollar-requires-private-sectors-help-fed-chairman/
Clearly, I am a bit behind.
Category: Mobile Payments
The Card Was and Is Only a Credential Carrier
Cash is here to stay – cards are the true dinosaurs
This question of the extinction of the payment card is misleading.
What is a payment card? It is the carrier of a set of credentials, A means of Identification offering financial Attributes capable of being authenticated by a party seeking to sell something to the individual or entity presenting the credential as a mechanism to assure payment.
Back when credit cards were designed, the goal was to offer merchants a guarantee of payment and anonymous consumers a means of paying. Behind this means of payment, a financial institution, the issuer, provides the consumer with a “Line of Credit”.
On the merchant side, another financial institution buys these guaranteed receivables from the merchant and charges the merchant a “merchant discount”. Later that day the Issuing Institution advances payment to the Acquiring Institution based on an agreed set of terms and operating rules. Terms and conditions the involved financial institutions collectively agreed upon.
For this method of payment to be effective, a large number of consumers and merchants had to agree to participate; hence the financial institutions came together and formed what we now know as MasterCard and Visa.
Given the state of technology at the time it was essential this new mechanism work without the burden and expense associated with the merchant, supported by the acquirer, contacting the issuer to receive approval, or, in stronger terms be assured of a guarantee of payment. To achieve this result, the merchant needed something to acquire the necessary information to submit a request for payment. For both the merchants and financial institutions,, there had to be a means of authentication. Designed to assure the responsible parties of the authenticity of the person or entity to present their payment credentials.
 To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
Overtime criminals successfully counterfeited these security features.
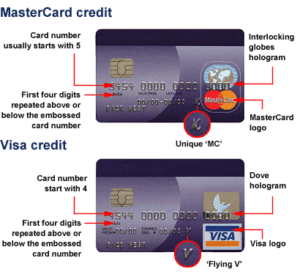
As these features were compromised additional features had to be added.
Today, a computer has been embedded inside the card, in order to assure the authenticity of the payment card credentials being presented to the merchant.
These computers embedded onto the front of a payment card exploit the power of cryptography. Cryptographic certificates and digital signatures are created by and for these computers, allowing:
-
- The Issuer (symmetric cryptography) to support Online Authentication
- The merchant (asymmetric cryptography) to support Offline Data Authentication
These two mechanisms prove to the merchant and issuer that the card is unique and the data, credentials, and digital signature it contains or produces are authentic.
Once all the merchants have are capable of reading the data from the chip card, the security features of the card become redundant.
As these features become redundant and the merchants embrace Near Field Communications, based on the ISO 14443 standard, the issuer can replace the card form factor with anything equipped with the necessary computational capabilities and ability to communicate with the terminal over the NFC interface.
This is exactly what Apple Pay and Google Pay have done. They replaced the card with a device. Yes, the Payment Card may become redundant. But, the Payment Credentials they contain, remain.
What we know as card payments, is fundamentally an account-based solution. Money, through the defined settlement process, ultimately move from the line of credit or deposit account of the buyer, through a series of accounts with the participating financial institutions, to the account of the merchant.
Card-based credential payments
simply become
Device-based credential payments
Where are we
Today.
How many passwords are you trying to manage! Does your LinkedIn contact list connecting you to more than 4,000 individuals? Does Facebook, Instagram, and other social media websites inundating you with news and stories about your friends, colleagues and interesting people?
How many cookies have your computers accumulated? How many databases have more information about you than they need? If we search the dark web, how valuable is your data?
Cando seeks to help you manage your data, identity, assets, and relationships.
Philip lives on Sea Island with his 93-year-old father, the Doctor. They pursue travel and Philip keeps his head into what is happening in financial services, blockchain, authentication, digital identity, and, whatever else people seeking to understand the transformation; particularly those in the identity and payments space.
What is happening means we can unlock our hotel rooms, cars, and homes from our phones. Our security system iwill be another app we have to find on our phone.
Instead, we need an intuitive assistant seeking to simplify our lives by taking on repetitive tasks like driving, working inside a data table or simply opening up the house for the season.
Normalizing data and performing the analysis capable of earning value is the name of the game. Management is about stimulating a team to work in the mutual interest of the organization. Executives define the strategy and articulate the vision in a manner conducive to success.
Cando seeks to help you manage your assets and relationships. Assets those places and things you use doing your daily life and those interactions you have with people and entities seeking to serve, sell and partner with you.
Then there are friends who we expect to be part of our lives and therefore have privileges and access capabilities.
All of this with a target of selling integration services to the top million and simply assuring each person has an identity thus serving the bottom billion. ultimately earning $1 per year per user to simply be there when it all breaks and you wish to restore your digital life.
At the core, your digital security will be based on the use of cryptography and sophisticated matching algorithms designed to assure anyone that you are that one individual in the populatations of the universe.
What You possess, What You Are, What You Claim … Your Certificates
NCCOE NIST Multi-Factor Authentication
What you Possess — The Thing
What you Are — You
Your Relationships
Responsibilities
Authority
Advice
— Secrets
My Certificates
World Wide Web Consortium
FIDO Alliance
Global Platform
The Trusted Computing Group
- EMVCo
- ISO
- ANSI
- ABA
Future interests
- Artificial Intelligence
- Machine Learning
- Nature Language Interface
- Predictive Analytics
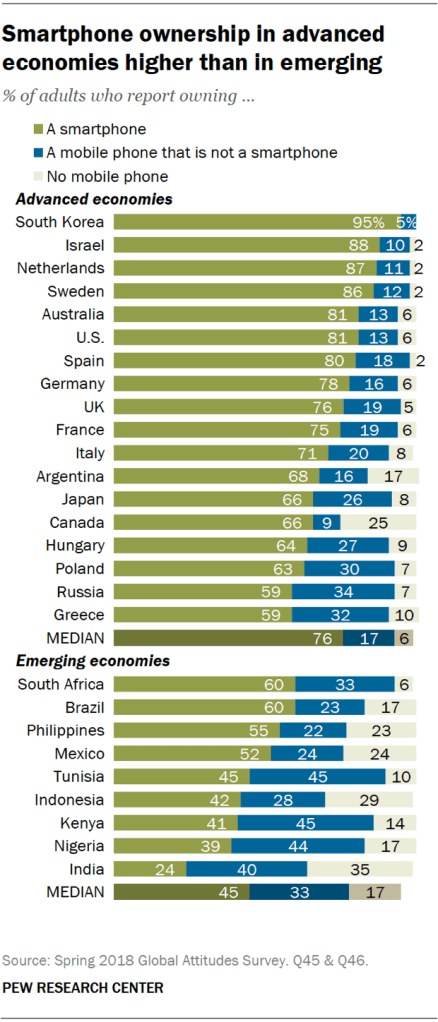
Smart Phone Ownership
Cash is King especially when the battery dies or the power goes off
Digital payments are growing, but consumers aren’t ready to abandon real money
Cash is king let us never forget it. Cash has always been the primary form of payment. It was until very recently accepted everywhere. Most likely will once again be accepted everywhere especially given the need to make sure we do not disenfranchise the unbanked and underbanked will remain the default form of payment
This said, what always amazes me is how so many authors forget Apple Pay, Google Pay and the other NFC based mobile phone based payment solutions are simply another device capable of carrying your debit and / or credit card credentials.
What many of these authors are starting to remember is how much it costs a merchant to accept these alternate forms of payment. I wonder when they will also begin to appreciate how many if not all of these alternate forms of payment only work when the power is on. Our always on society assumes power never goes off. We dream of everything in our mobile phone and forget when we last could not use our phone because the battery was empty. Or the store clerk who could read your card because the power went down.
This is one of the redemining facts about cash. Cash exists without power and can be used whenever.
What Happens When the Lights Go Out
 Since 1984, when I was told I needed to carry this mobile phone with me, there has been that nagging issue of needing to make sure it had enough life to get me to the next charge point. My first phone was luck if it could last a half a day so they gave me two, one was always being charged while the other hung on my shoulder. In 1993 while working on the development of the EMV Specifications we focused on the ability to authorize a transaction when the Point of Sale POS device was unwilling or unable to reach the issuer. In 2013 I listened to Visa representatives explain how 100% of all payment transactions could be executed online. Then I ponder getting a Tesla Model 3 and learn it is only capable of traveling a maximum of 310 miles, it make me wonder; how do I finish the last 19 miles to my fathers home.
Since 1984, when I was told I needed to carry this mobile phone with me, there has been that nagging issue of needing to make sure it had enough life to get me to the next charge point. My first phone was luck if it could last a half a day so they gave me two, one was always being charged while the other hung on my shoulder. In 1993 while working on the development of the EMV Specifications we focused on the ability to authorize a transaction when the Point of Sale POS device was unwilling or unable to reach the issuer. In 2013 I listened to Visa representatives explain how 100% of all payment transactions could be executed online. Then I ponder getting a Tesla Model 3 and learn it is only capable of traveling a maximum of 310 miles, it make me wonder; how do I finish the last 19 miles to my fathers home.
Today, I was reading an article emanating from the Money 2020 event when IDEMIA spoke of the idea of the mobile drivers license and that nagging feeling emerged. What happens when the power goes off after the hurricane hit and someone asks me for my drivers license. Its locked securely inside my dead mobile phone. I then saw that their competitor Gemalto and even NIST are working on this concept of the mDL.
We live in a world where electricity is becoming as essential as water and food. Yet, we hear of power outages that last weeks and even months.
It is like with Mobile Payments, if the phone is dead and in order to pay it must, then what?  The card remains the essential element of a successful payment transaction.
The card remains the essential element of a successful payment transaction.
I dream of the day when I can merge my leather wallet and my mobile device into one. Yet, I appreciate there are technical challenges like the need for electricity. Until we lead with these technical challenges and not simply the dream. Exciting concepts and ideas will go where so many have gone before.
The case for Identification and Authentication
As we continue to explore the case for Identification and Authentication I share the below article.
What is becoming clear is standards are being embraced.
In the Payment space
Will it be W3C WebAuthN, 3DC and Webpayments or EMVCo SRC & Tokenization?
My guess depends on if standards bodies can play well together. EMV (contact or contactless) will remain the many stay for physical world commerce, until the App takes over the Omni Channel shopping experience. then the merchant will properly authenticate their loyal customer and use card on file scenarios for payments. The question of interchange rates for CNP will see a new rate for “Cardholder Present&Authenticated/ Card Not Present.”. In time when a reader is present I can see an out of band “tap to pay” scenario emerging using WebPayments and WebAuthN.
In the identity space
I contend the government and enterprise market will go for a pure identification solution with the biometric matched, in the cloud, in a large central database. In order to maintain a unique and secure cloud identity, they might probably make use of various opportunities that come their way (you can hover over at this website to learn more).
However, does that mean it includes what you know username, email address or phone number? Maybe! If it is simply the captured image or behavior, then it is a 1 to many match. If it is with an identifier, it is classic authentication with a one-to-one match.
In the pure authentication space where the relying party simply wants to know it is the person they registered. Then, the classic FIDO solutions work perfectly and will be embedded into most of our devices. Additionally, the use of a visitor sign in sheet synced with the security database could expedite the sign-ins of visitors. It could also see its applications with employee log authentication and verification. Or, as we’ve seen with some enterprises, the relying party will embrace U2F with be a FIDO Key, like what Yubico and Google recommend.
The classic process needs to be thought about in respect to what can be monetized.
- Enrollment = I would like to become a client or member
- Proofing = Ok you are who and what you claim, we have checked with many to confirm your Identity – This is where federation comes in.
- Registration – Verification = Ok, now we confirm it is you registering your device(s)
- Authorization & Authentication = Transaction with multiple FIDO enabled relying parties using your duly registered authentication.
How Microsoft 365 Security integrates with the broader security ecosystem-part 1
by toddvanderark on July 17, 2018
Today’s post was coauthored by Debraj Ghosh, Senior Product Marketing Manager, and Diana Kelley, Cybersecurity Field CTO.
This week is the annual Microsoft Inspire conference, where Microsoft directly engages with industry partners. Last year at Inspire, we announced Microsoft 365, providing a solution that enables our partners to help customers drive digital transformation. One of the most important capabilities of Microsoft 365 is securing the modern workplace from the constantly evolving cyberthreat landscape. Microsoft 365 includes information protection, threat protection, identity and access management, and security managementproviding in-depth and holistic security.
Across our Azure, Office 365, and Windows platforms, Microsoft offers a rich set of security tools for the modern workplace. However, the growth and diversity of technological platforms means customers will leverage solutions extending beyond the Microsoft ecosystem of services. While Microsoft 365 Security offers complete coverage for all Microsoft solutions, our customers have asked:
- What is Microsofts strategy for integrating into the broader security community?
- What services does Microsoft offer to help protect assets extending beyond the Microsoft ecosystem?
- Are there real-world examples of Microsoft providing enterprise security for workloads outside of the Microsoft ecosystem and is the integration seamless?
In this series of blogs, well address these topics, beginning with Microsofts strategy for integrating into the broader security ecosystem. Our integration strategy begins with partnerships spanning globally with industry peers, industry alliances, law enforcement, and governments.
Industry peers
Cyberattacks on businesses and governments continue to escalate and our customers must respond more quickly and aggressively to help ensure safety of their data. For many organizations, this means deploying multiple security solutions, which are more effective through seamless information sharing and working jointly as a cohesive solution. To this end, we established the Microsoft Intelligent Security Association. Members of the association work with Microsoft to help ensure solutions have access to more security signals from more sourcesand enhanced from shared threat intelligencehelping customers detect and respond to threats faster.
Figure 1 shows current members of the Microsoft Intelligent Security Association whose solutions complement Microsoft 365 Securitystrengthening the services offered to customers:
Figure 1. Microsoft Intelligent Security Association member organizations.
Industry alliances
Industry alliances are critical for developing guidelines, best practices, and creating a standardization of security requirements. For example, the Fast Identity Online (FIDO) Alliance, helps ensure organizations can provide protection on-premises and in web properties for secure authentication and mobile user credentials. Microsoft is a FIDO board member. Securing identities is a critical part of todays security. FIDO intends to help ensure all who use day-to-day web or on-premises services are provided a standard and exceptional experience for securing their identity.
Microsoft exemplifies a great sign-in experience with Windows Hello, leveraging facial recognition, PIN codes, and fingerprint technologies to power secure authentication for every service and application. FIDO believes the experience is more important than the technology, and Windows Hello is a great experience for everyone as it maintains a secure user sign-in. FIDO is just one example of how Microsoft is taking a leadership position in the security community.
Figure 2 shows FIDOs board member organizations:
Figure 2. FIDO Alliance Board member organizations.
Law enforcement and governments
To help support law enforcement and governments, Microsoft has developed the Digital Crimes Unit (DCU), focused on:
- Tech support fraud
- Online Chile exploitation
- Cloud crime and malware
- Global strategic enforcement
- Nation-state actors
The DCU is an international team of attorneys, investigators, data scientists, engineers, analysts, and business professionals working together to transform the fight against cybercrime. Part of the DCU is the Cyber Defense Operations Center, where Microsoft monitors the global threat landscape, staying vigilant to the latest threats.
Figure 3 shows the DCU operations Center:
Figure 3. Microsoft Cyber Defense Operations Center.
Digging deeper
In part 2 of our series, well showcase Microsoft services that enable customers to protect assets and workloads extending beyond the Microsoft ecosystem. Meanwhile, learn more about the depth and breadth of Microsoft 365 Security and start trials of our advanced solutions, which include:
Digital Identity
Question for all those who advocate migration from card to electronic
We all are aware and many of us dream of a time when all of our physical identity artifacts are digital. We dream of consolidating these credentials in our electronic wallet, otherwise known as our mobile phone.
Today while visiting an outpatient imaging center, I was asked for my driver’s license. She would only accept the physical document, I offered to send an image by email. Her goal to scan my identity document into the electronic patient file she was creating. The idea of an image of the driver’s license in an email, well.
Sure the system could easily be changed to record digital credentials delivered by NFC or BLE. The first question, given the expensive medical system we have here in America; at whose cost?
Time could not be argued as a saving, she would only have saved a second or three of time to pass the card back to me.
People discuss contactless cards and contrast them to the convenience of a Mobile Wallet. What we often forget is the reality. As long as we need to carry other physical identity artifacts, the convergence of our leather wallet into our electronic device is not happening.
In my humble opinion, it is an all or nothing situation. Yes, I will add digital credentials into the mobile wallet. But, unfortunately, the leather wallet is still part of my attire.
Better still, it does not need to be recharged. My leather wallet still works after the phone’s battery has died.
Mobile Payment – Thoughts after listening
Thoughts resulting from The webinar Doug King of the Atlanta Federal Reserve gave on “Future Proofing Payments”
The long standing question of the future of Mobile Payments, again discussed and again similar conclusions.
- Will the American market embrace the idea of mobile payments?
- Is it a question of when or a question of why?
- Why do emerging markets embrace new ways and mature markets resist?
- Is it all about acceptance and the merchants investment in contactless reader capability?
- Is it an all or nothing concern?
- Could it be simply reality, as ling need our wallet with other cards e.g. our drivers license, why eliminate payment cards from the physical wallet?
Doug touched on all of these questions. He shared relevant statistics demonstrating the slow and possibly indistinguishable grow in usage of mobile wallets. He shared the success of several of the merchant proprietary mobile payment approaches.
Which leads me down the path of another question. What is the value proposition that will ignite the use of our phone and devices as carriers of our means of payment? The possibility to create value simply with a electronic wallet carrying only means of payment, does not create an exciting proposition.
Our mobile phones and connected devices provide us with such value
We have embraced dozens of apps. They help us to navigate, shop, explore, play and learn. Our phones are beginning to become security devices, taking advantage of sensors to integrate biometrics into how we access and authenticate ourselves as we browse and explore the ever increasing digital place we now call cyber space.
There is another phenomena emerging as a result of how we are transforming how we engage. Some called it the “Uberization” of payments, the ability to make payments frictionless. A change so profound we must stop and reflect and ponder what next.
I recognize there is a repetitive theme to my musing.
When physical world merchants fully embrace the concept of omni channel and build their virtual and physical experiences to complement and augment one another, then, with the ability to integrate payment seamlessly into the shopping experience a value proposition emerges.
What is EMVCo goal with the release of their SRC framework
October 2017 EMVCo published version 1.o of their Secure Remote Commerce Technical Framework. Today I decided to read and appreciate what they are trying to accomplish and then consider how it ties into what I remember and think we need to do moving forward.
Clearly the challenge links back to the now infamous New Yorker Cartoon.  We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card.
We have not successfully established a means of assuring the identity of an individual when presenting payment credentials (the PAN, Expiry date, name, billing address and CVV. The first attempt, still not 100% implemented, was the introduction of CVV2, CVC2 or CID a 3 or 4 digit number printed on the back or the front of the payment card.
We then developed something called SET or Secure Electronic Transactions and unfortunately the payment networks were not willing to allow Bill Gates and Microsoft to earn 0.25% of every sale for every transaction secured by SET he proposed to build into Microsoft’s browser. Without easy integration into the consumer browser, the challenges of integrating SET into the merchant web pages and the Issuer authorization systems caused this effort to fail the death of some many other noble but complicated attempts to create a means of digital authentication.
Next came 3D-Secure, a patented solution Visa developed. It offered what was considered a reasonable solution to Cardholder authentication. Unfortunately, given the state of HTML and the voracious use of pop-ups, the incremental friction, led to abandon shopping carts and consumer confusion. Another aborted attempt at Internet fraud mitigation.
Yet 3D-Secure was not a total failure. Many tried to enhance it, exploit it and avail themselves of the shift of liability back to the Issuer. Encouraging consumer engagement and adoption was futile in some markets mandated and cumbersome in others.
Now let’s consider what EMVCo is attempting to do with their Secure Remote Commerce Technical Framework. As I started to read, I ran into this:
“As remote commerce becomes increasingly targeted and susceptible to compromise, it is important to establish common specifications that protect and serve Consumers and merchants.”
Clearly the authors do not have institutional memory and cannot remember the various attempts alumni of these same organizations spent time on and encouraged many to invest in their implementing. Clearly this lack of historic context will leave some pondering the purpose of this paper.
I then read this sentence and reflect back on a recent hearing on “Social Security Numbers Loss and Theft Prevention” in front of The House Ways and Means Subcommittee on Social Security
“Over time the Consumer has been trained to enter Payment Data and related checkout data anywhere, making it easy for bad actors to compromise data and then attempt fraud.”
Once again, I stand troubled by how the Payment Data clearly printed on the face of the card and especially the PAN, 11-19 digits, designed to simply be an identifier, was converted into an authenticator. Like the social security number, the drivers license number, the passport number and your library card number, the PAN and other “Payment Data” was never designed to be an authenticator. It was meant to be data a merchant could freely record.
The secure features of the card now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC”
now the EMV cryptographic techniques otherwise referred to as the Application Request Cryptogram “ARQC” 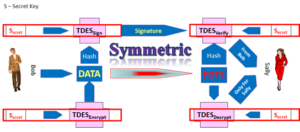 were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
were meant to offer the “What You Have” factor in a multi-factor authentication scheme.
As I began to appreciate the scope of this document, the term “Consumer Device” becomes critical. I began to wonder if a PC is a consumer device or if a consumer device is only something like a mobile phone, watch or other like appliance. Fortunately, later in the document, the definition clears up any confusion created by the earlier use of this term.. This said, I then wonder about the difference between what they define as Cardholder Authentication and Consumer Verification?
After reading through all the definitions, I ponder why the authors had to change terminology? Why could they not embrace known and recognized nomenclature. Do we need a new vocabulary?
I wondered:
If this is another attempt to create a revenue stream for the payment networks?
Or, is this the effort of a “closed standards” body to reduce the potential value of the W3C WebPayments activity?
In search of an answer to this last question, I found this discrete comment inside the SRC FAQ.
9. Are any other industry bodies working in this area?
EMV SRC is focused on providing consistency and security for card-based payments within remote payment environments.
EMVCo aims to work closely with industry participants such as W3C to capitalise on opportunities for alignment where appropriate.
Having read bits and pieces of this and the WebPayments efforts one does wonder what is EMVCo trying to do. We shall see?
Will Wal-Mart Pay surpass Apple Pay, Samsung Pay and Android Pay
Walmart Pay to surpass from pymnts.com – from the Washington Post. – and another
To open the news and find more than a press release in fact true commentary describing the success of a merchant mobile payment solution. This is big news and speaks to the value of loyalty and the power of largest global merchants willingness to focus and innovate.
Philip Andreae & Associates is Open for Business
ISIS the new Mobile Commerce JV … What next
This goes back to november 2010 when the announced ISIS (renamed SoftCard now dead and buried)
Over the last week many of us have read and attempted to understand what are the goals and objectives of Isis and its owners AT&T, Verizon and T-Mobile.
Visa reacted, pundits speak of ISIS becoming a new payment brand/system and Google, Ericson, Apple and RIM all are embracing NFC and speaking to inclusion in the mobile phone.
To include all these links would take more space than appropriate. A simple Google search with key words like ISIS Mobile Commerce etc. will quickly get you to more than you could digest.
Doc: EPC 220-08, Version 1.0 January 2010
What occurred to me is that Isis could set itself up as a “Trusted Service Manager” TSM, taking on a trust function supporting Issuers and Mobile Network Operators MNO and why not the merchant; who all all talk about the capabilities of the mobile phone and will want to dematerialize their cards and install their certificates, data and applets within the context of a mobile wallet. ISIS can then derive their revenue from fees assocaited with “Trust” and assuring the identity of the owner of the phone,.
I do not see ISIS becoming a new means of payment. I see them becoming an enabler that helps build the business case to drive the necessary investments merchants and carriers must make to assure the consumer that they can move all their cards into their mobile phone. Mobile Commerce is the key words that leads me to think about coupons, loyalty, rewards, push marketing …
As we all know contactless and NFC are not getting the traction one might have expected. Mobile loyalty, Mobile commerce, services branded as a means of enhancing the customer experience those I do imagine will excite merchants and consuemrs to demand NFC capabiliites. Imagine walking into a store and getting coupons and discounts as you tap and add to your shopping cart. Clearly merchants appreciate that they can drive consumers to buy more it they can excite them.