Cash is here to stay – cards are the true dinosaurs
This question of the extinction of the payment card is misleading.
What is a payment card? It is the carrier of a set of credentials, A means of Identification offering financial Attributes capable of being authenticated by a party seeking to sell something to the individual or entity presenting the credential as a mechanism to assure payment.
Back when credit cards were designed, the goal was to offer merchants a guarantee of payment and anonymous consumers a means of paying. Behind this means of payment, a financial institution, the issuer, provides the consumer with a “Line of Credit”.
On the merchant side, another financial institution buys these guaranteed receivables from the merchant and charges the merchant a “merchant discount”. Later that day the Issuing Institution advances payment to the Acquiring Institution based on an agreed set of terms and operating rules. Terms and conditions the involved financial institutions collectively agreed upon.
For this method of payment to be effective, a large number of consumers and merchants had to agree to participate; hence the financial institutions came together and formed what we now know as MasterCard and Visa.
Given the state of technology at the time it was essential this new mechanism work without the burden and expense associated with the merchant, supported by the acquirer, contacting the issuer to receive approval, or, in stronger terms be assured of a guarantee of payment. To achieve this result, the merchant needed something to acquire the necessary information to submit a request for payment. For both the merchants and financial institutions,, there had to be a means of authentication. Designed to assure the responsible parties of the authenticity of the person or entity to present their payment credentials.
 To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
Overtime criminals successfully counterfeited these security features.
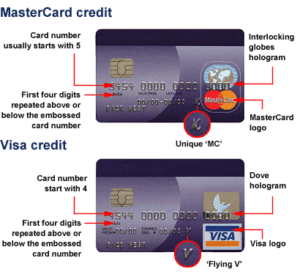
As these features were compromised additional features had to be added.
Today, a computer has been embedded inside the card, in order to assure the authenticity of the payment card credentials being presented to the merchant.
These computers embedded onto the front of a payment card exploit the power of cryptography. Cryptographic certificates and digital signatures are created by and for these computers, allowing:
-
- The Issuer (symmetric cryptography) to support Online Authentication
- The merchant (asymmetric cryptography) to support Offline Data Authentication
These two mechanisms prove to the merchant and issuer that the card is unique and the data, credentials, and digital signature it contains or produces are authentic.
Once all the merchants have are capable of reading the data from the chip card, the security features of the card become redundant.
As these features become redundant and the merchants embrace Near Field Communications, based on the ISO 14443 standard, the issuer can replace the card form factor with anything equipped with the necessary computational capabilities and ability to communicate with the terminal over the NFC interface.
This is exactly what Apple Pay and Google Pay have done. They replaced the card with a device. Yes, the Payment Card may become redundant. But, the Payment Credentials they contain, remain.
What we know as card payments, is fundamentally an account-based solution. Money, through the defined settlement process, ultimately move from the line of credit or deposit account of the buyer, through a series of accounts with the participating financial institutions, to the account of the merchant.
Card-based credential payments
simply become
Device-based credential payments












 When we think about the migration to contactless or Dual Interface cards it is important to have a general understanding of what goes into creating the card and the constraints one has to think about, as they work with their marketing teams to design these cards.
When we think about the migration to contactless or Dual Interface cards it is important to have a general understanding of what goes into creating the card and the constraints one has to think about, as they work with their marketing teams to design these cards.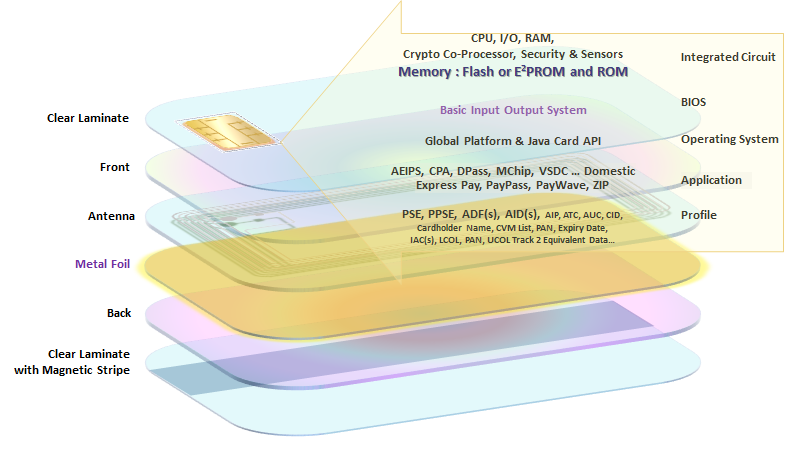




 and a Eurocard was all we needed to buy and enjoy life. Electronic payments was the norm, paper checks were a rare oddity and cash, well yes there was a very present grey economy.
and a Eurocard was all we needed to buy and enjoy life. Electronic payments was the norm, paper checks were a rare oddity and cash, well yes there was a very present grey economy.

 We could go on and talk about how Apple saw the possibility of a 0.15% income stream from ApplePay based mobile payments and how the EMVCo tokenization framework evolved to support their desire to protect the Apple Brand.
We could go on and talk about how Apple saw the possibility of a 0.15% income stream from ApplePay based mobile payments and how the EMVCo tokenization framework evolved to support their desire to protect the Apple Brand.