CanDo
Payment Card Construct and Dual Interface Deployment
Payment Card Construction
The discussion focused on the construction of the sandwich. Four layers. Clear front laminate to protect the ink, front with the banks design and brand logo, back with the banks back design and a clear laminate with the magnetic stripe integrated into it.
To enhance design additional layers may be added, such a metal foil.
These four sheets are then bonded together, at 120 degrees, in sheets of 21, 36 or 48 or other various sheet sizes. Next step punch out cards, add hologram and signature panel.
For a standard EMV card the next phase is to mill and embed the module with the chip inside. Last, the manufacturer typically loads the O/S & EMV application into the integrated circuit card.
When we move to dual interface caed, this process is modified to add an inlay, with the antenna embedded within. This inlay is inserted in the middle of the sandwich and during the embedded process the contacts exposed on the base of the module are connected to the antenna in the inlay.
Next step, personalization, when the appropriate data is loaded into the chip, along with the encoding of the magnetic strip and printing and/or embossing of the cardholders, name, expiry date, cvv2 and other information onto the card.
Contactless or Not That is a Question
Contactless NFC acceptance and dual interface issuance is all about the chicken and the egg. Who will go first? The merchant or the issuer? Each need each other. Both are wondering about the incremental value.
- Faster transactions – Yes
- Less cash – maybe
- More revenue – good question!
Given these questions and observations, one can only wonder.
Identity a brave new world
life, liberty and the pursuit of happiness
When I received this video
I wondered if prudish Americans would appreciate the continental humor.
For me and now I speak from my heart, mind and soul. I remember well going to Jones Beach with two special ladies. They made it clear they would bath as they wished and I needed to accept and not be some leering male. I then remember traveling to Paris and seeing beautiful people adorning those typical French round advertising pillars. The French simply use the beauty of the human body to promote perfume or some other sensual thing. After I moved to Europe and we venturing, children in hand, to the beaches of Holland, France, Spain and Italy we learned to simply accept. Even more telling, I attended an ITUG conference at a 5 star hotel in Budapest and ventured down to the spa.
I wonder why Americans are bound up in a moral turpitude.
We are either far to the right or fair to the left.
Arnold Schwarzenegger was interviewed today and argued our country must come back to the center. Morality is key to why we are so far apart. So many on the right so many on the left. Little room to find accommodation in the middle.
We purport to be a country of law, a country of freedom and a country of choice. Yet we are tangled up in imposing rules to govern choice. I read of how in Virginia back in the 30’s they attempted to ban interracial marriage and discovered that most of the population had some of Pocahontas in them. I then think about those that are marching today. They argue that the friends who died, are more important than the rights of those who want to let anyone bear arms. Yet that small minority, the NRA, seems to have control over the decisions of the peoples’ representatives. If we believe we can ban the mixing of races, yet we are unable, as the majority, to ban the type of arms, weapons, people are allowed to own, what are we!
Arnold today spoke of education, health and the environment.
If we want to Make America Great Again then why do we allow our system of education to stigmatize people based on where they live. Why do we not assure each citizen the right to equal education. He reminded the audience this country ranks 39th in the world. He said that regulating diversity was ridiculous. He argued that by offering equal education, we enable people equal opportunity. His argument made perfect sense. Using local property taxes to fund education, ultimately means where you live, hence your family income, defines who has opportunity to excel. If we want to remain the greatest country in the world and assure all citizens equal opportunity, then, we must invest in education.
Bottom line Education is the key to Making America Great Again.
Health, there are 4 living doctors in my family. Through my kinship to them, I have heard and listened to them speak of the issues with our system. For my simple mind the problem begins with Capitalism. It is all about big corporations wanting to profit from their skills. It is about insurance companies wanting to minimize risk (expense) by minimizing the amount of care they have to pay for. I am familiar with social medicine. Three countries provided me personally with exposure to how it can and does work.
Yes, if you can afford care in this country, you will get the best care.
The challenge, every American cannot afford care, without insurance. And, if everyone is not insured then those that are the least wealthy and healthy are without. For me this graph tells the whole store. 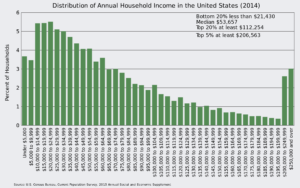
I am personally paying insurance under a Cobra plan. For Selma and I, one household, it costs 1,291.43 a month $15,520.92 a year.
We all need universal care. We need to require everyone to pay into our health system. This is the only way will we assure affordable care for all. How does one build such a system, I suggest, it must resemble what Switzerland has built.
Minimum care paid through taxes. Supplemental care, each households responsibility.
Next is our environment. Once, we worried about pollution and the quality of our air and water. Now, we must expand our thinking. We must remember we are stewards of this earth and realize our consumption of the earth’s resources will affect the balance of the earth and its ecosystem. We are here to protect the earth for our children and for the children they will bring into this world.
We can argue all night long about the science. What we do know is that if we change the balance of anything there is a result. The classic appreciation of cause and effect. We the USA, with less than 20% of the word population, recently were responsible for most of the carbon dioxide injected into the atmosphere. Today this no longer is true. But, we recently pulled away from helping to lead the world to a better place. Instead our President wants us to return our sources of energy back to those non renewable earthly resources, coal and oil. We all know they pollute!
Finding reusable means of generating energy, is good politics. The Economist March 17th 2018 had an excellent special report on the politics of energy.
If we do not embrace renewable sources of energy and reduce our dependence on Oil and Coal, we will no longer be the great national we are and seek to remain.
As I write, I am remember learning about the Fourth Industrial Revolution. As the first sentence so aptly says it
“The Fourth Industrial Revolution is changing everything – from the way we relate to each other, to the way our economies work, to what it means to be human”.
We must properly harness technology.
- Education is the key.
- Our environment can only benefit.
- Healthcare will simply become more efficient
In the end we will improve everyone’s life.
Yet?
As Adam Smith best explains, our global economy (yes we are a global economy), can only be successful when we view it as a closed system.
We must appreciate that we are all part of the whole. Only when we each give to our own abilities, will we find balance. If we allow labor arbitrage to take jobs away; then, those who lose their jobs must find new ways to contribute. They cannot expect the system to sustain them!
Yet they should expect those that profit to help re-educate.
Why am I writing. What am I asking.
Maybe to share. Maybe to speak out.
There is one other topic on my mind. Those who understand the loss of a friend in Parkland are speaking out, they are marching in Washington and around the country to get people to listen and vote to arrest the stupidity of how the second amendment is being mis-interpreted.
For me the key is found in the first part of that amendment
“ A well regulated Militia, being necessary to the security of a free State,
In my opinion, what resulted from District of Columbia v Heller (2008) was an unreasonable interpretation of the second amendment. I would suggest United States V. Cruikshank (1876) and United States v Miller (1939) are a better interpretations. Those interpretations, in my opinion, are not influenced by the political influence of the NRA and gun manufactures’. Their and the NRA’s focus is to market, sell and protect their right to profit! They are not focused on assuring the free state has a well regulated militia. If they were, they would insist on training, education and the formation of groups – in other words militias.
The second phrase
“The right of the people to keep and bear arms shall not be infringed.”
For me, this is why Switzerland ends up with guns in every home. The people are members of the armed forces. They are “The Militia”. They belong to a “well regulated” group of people focused on “the security of a free state”. They are trained. They understand the purpose of these weapons. The militia, in other words the people, can determine if there are mental issues and exclude those individuals as they are evaluated and introduced to their responsibility as a member of the militia of the people.
Looking back on the histogram above many of you are or will be part of the upper 10%. We are the ones most gifted. We therefore must be the ones that are the most interested in making this world is a better place. Simply accepting the way it is, means we are not working together to make the world, this country, a better and more equal place.
Going back to the video we must assure our freedoms. We must focus not on how we expect people to live. We must remember why we became a nation.
“We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness. — That to secure these rights, Governments are instituted among Men, deriving their just powers from the consent of the governed”
Our founders made it clear, we each have the right to life, liberty and the pursuit of happiness.
The way I interpret what we attempted, as a nation, to establish; is a body of people, a society, that respects each of our individual rights and seeks to protect each individuals right to life, liberty and the pursuit of happiness. If I want to expose myself in the comfort of a community that enjoys this way of life, as long as we do not imping on your rights, why not? Slavery, Blue laws, various interpretations based on the desire to impose your will on me is not why we declared independence. It is not what our constitution attempted to create.
I want clean air, clean water, not to see your litter in public view and be able to drink alcohol and/or smoke marijuana. I want the ability to see a doctor when I need to and not worry that I cannot afford to. I want to be able to to see all children attend school, knowing they will get a great education. I also do not want to worry that some lunatic will buy assault rifles and use these weapons reserved for a well regulated militia to kill children while they are at school. I want to be able to attend a music festival and not worry that some person up in some hotel room is capable of buying an arsenal simply to kill people.
Yes we should have the right to hunt and protect ourselves. Assuming we are trained and capable and more importantly are of stable mind and body.
We must each remember the ten commandments Exodus 20 or simply put the two found in Matthew 22:37-40, Mark 12:29-34 and Luke 10:25-37
Most importantly we must read, appreciate and be the Samaritan described in Luke 12:30-37.
Each of us is bestowed with skills and abilities. We have the funds to be able to help drive policy we have the responsibility to assure each is given the right to life, liberty and the pursuit of happiness.
These are my beliefs.
I hope those reading my thoughts are willing to respect them and share theirs. Only if we engage in discourse can we assure ourselves life, liberty and the ability to pursue happiness.
Obviously to avoid spam I do moderate comments. As long as there is no profanity, I will not censor anyone’s comments. I am also posting the existence of this Blog on Twitter and Facebook. In those environments and as Cambridge Analytica has demonstrated, these thoughts will simply expand the public’s awareness of my habits, patterns and thinking.
Respectfully,
Financial Trade Groups Write to House Leaders in Support of Data Breach Notification Bill
https://bankingjournal.aba.com/2018/02/financial-trade-groups-write-to-house-leaders-in-support-of-data-breach-notification-bill/

The associations expressed support for draft legislation released by Reps. Blaine Luetkemeyer (R-Mo.) and Carolyn Maloney (D-N.Y.) that would create a level playing field of nationally consistent data protection standards and post-breach notification requirements. This bill would not create duplicative standards for financial institutions which are already subject to robust standards, but rather extend similar expectations to other sectors that handle consumer data.
“The goal of the bill is simple — raise the bar so that all companies protect data similar to how banks and credit unions protect their data, and create a common-sense standard to ensure consumers receive timely notice when a breach does occur,” the groups wrote.
The draft bill contains a provision that recognizes the existing, effective regulatory framework for covered financial sector entities. While the provision was intended to prevent banks and credit unions from being subject to duplicative notification requirements, it has been the target of recent negative campaigns circulated by the National Retail Federation and the Retail Industry Leaders Association, which incorrectly suggested that banks do not notify customers of breaches on their computer systems and The ads from the retailer groups also mischaracterize and exaggerate the share of data breaches occurring at banks and credit unions while omitting their members’ (higher) share of data breaches.
The financial trades refuted the notification assertion, noting that “banks and credit unions have long been subject to rigorous data protection and breach notification practices for financial institutions to follow,” and that in the event of a data breach, banks and credit unions work continuously to communicate with customers, reissue cards and enact measures to mitigate the effects of fraud. They added, however, that “no solution will work unless everyone has an obligation to take these steps.” For more information, contact ABA’s Jess Sharp.
What scares me most
Tonight while preparing to listen to the Atlanta Symphony Orchestra play a bit of Beethoven I have a moment to reflect on the Worldview.
Once upon a time one could turn on the news and get a glimpse of what is happening at home and round the world. One could pick up a newspaper and think this will provide me a glimpse of the truth.
Then! In emerged the capabilities of communications and the capacity to write and distribute anything to a vast number of individuals. Otherwise called the Internet.
Yet, what is different? In the past books were burned, history was rewritten and lies were told. The challenge,today we can manipulate what people believe, on a global scale, in realtime. We can spread disinformation and drive the masses to believe anything people with a voice and the power to thrill want to convince them to believe.
Starting in 2016 who would become the American President proved this to be possible. The media demonstrated that they can spin the truth in whatever direction they so desire.
This week the story is about how the DOJ and the FBI obtained warrants from one of the strictest courts in the land. Every 90 days bringing new information, they convinced the FISA court to allow them to continue to investigate the potential actions of our enemy, Russia, or, what was the USSR. What the Russians did was evil and manipulative. I somehow doubt the GOP’s version of the trutb.
Vindicated! Donald thinks he is. Yet, for those who take the minutes to read, one can only wonder what does this incomplete review of the facts actually prove? Nothing!
I wonder why I waste so much of my time listening, reading and worrying. Is there truly a risk? Are we so divided that it matters. Maybe!
Part of the challenge, many think President Trump is doing good. They accept his narcissistic personality and read his tweets with a simply, oh please stop. The rest of us cringe and worry. We consider the risks. We watch our leaders splinter and the divide expand, and we hope for a better day tomorrow.
Fir thise that seek out the truth, we explore and we become aware of the elements that are driving us into the Fourth Industrial Revolution. It causes us to wonder what can we do to bring the masses, those unskilled workers, who have been marginalized by intelligent robots, programmers, engineers and managers out of desolate. We work to reduce the numbers of workers and expand productivity all while ignoring the realities of the human repercussion ahead.
When I started this note, the thinking was about those who do not accept science, believe the world is flat and maybe 9,000 years old. They do not accept, we human kind, are responsible for the wrath of our planet’s climate. They do not appreciate the dangers ahead, as we change the balance of our atmosphere and pollute the lands and oceans that sustain us.
What next?
The management of our identity
A few weeks ago I learned of the Sovrin Foundation a foundation interested in establish a concept to support the idea of a self Sovereign means of identity.
As an advocate for stronger forms of identification and more important Authentication I am pleased to have received your response today.
Back in 1993 I was part of Europay and drove the creation of the EMV specifications as a form of Authentication and frankly reflecting back a strong form of Identification with the Trust Anchor being the Financial institution issuing the card and the foundation anchor being the payment network that the issuer used to assure acceptance globally.
In 2013 I joined the Board of the FIDO Alliance and eventually become the Secretary of that Board.
Today I am engaged with a company called IPSIDY, that is promoting and selling Identity as a solution.
Clear the conversations we are having include:
- Device based versus centralized biometric authentication
- Identification based on a central repository of Biometrics or a simply identifier linked to a means of authentication
- Claims and assertions one points (URL) to or those that one has in their own possession
- Repositories or Distributed databases of information
- Privacy of attributes and rights to defining what can be shared
When I ask about the future of Sovrin, I hear people saying great concept how does it scale to be useful.
This, as was my experience in the Payments world, is the challenge of a two sided market
- Consumer – Merchant
- Individual – Rely Party and those seeking attributes and proofs of identity
The challenge is developing a value proposition and more importantly critical mass that will excite both sides of the market to want to participate.
To further complicate developing the market is the challenge of the “Go To Market” strategy. Who does one partner with given that the usefulness to the citizen/consumer is predicated on the number of parties or places this solution, token or Identity with a set of sharable attributes can be usefully used.
This is the question this is the challenge.
A Shift from Check-out to Check-in will reshape the way merchants engage with their consumers
Think Uber, think order ahead, think account on file. With these ideas in your mind think engagement and Omni channel. Then consider the need of merchants to assure revenue by delighting and engaging with their customers in meaningful ways. Their focus, increasing basket size, more frequent visits and loyalty; in other words increased sales.
Then remember, Check-out is about friction, payments and long lines. These characteristics merchants seek to eliminate, reduce the cost of and enhance the experience around.
If we think Check-in, using big-data, geo-location, BLE, facial recognition, consumer centric apps and other techniques, we can image a world where human and device based personal assistants engage with the merchants loyal customers in a friendly, informed and satisfying way.
For payment people this means we need to remember that merchants want lower cost payments and friction-less check-out.
Bottom line, for loyal customers solutions that retain the payment credentials securely in the cloud. For one time and infrequent customers, they will look to incent loyalty and registration or simply accept classic means of payments e.g. cards.
This drive to move from recording a loyal customers visit to engaging when the customer arrives or better yet when they are doing their research is what we the consumer seek.
We are all about saving time, enjoying life and satisfying our needs and wants. Merchants that focus on the customer and their shopping experience will succeed and prosper./ Those that do not focus on delighting their customer will learn.
DIY the Cyber Guy a conversation about Bitcoin and EMV
https://www.voiceamerica.com/promo/episode/104814
A interesting discussion withDavid the the Cyber Guy. We spoke of the inherent risk of Bitcoins and the essential issue of the secret and a BitCoin folders resoponsibility to make sure they never lose the secret.
We then wandering off to talk about EMV or Chip and Pin.
Always a pleasure to work with David.
Words all bound to who we claim to be – How do we identify ourselves on the Internet or in Cyberspace?
Identifier – Something you create or are provided to digitally identify yourselves. Identifiers are things like an alias, user name, email address are examples.
Identity – This is who we are or wish to represent ourselves to be. These are attributes and information about: where we live, who we work for, which banks we have relationships with, who our friends are, which clubs we belong to, our certified skills, what schools we graduated from, which country(s) we are citizens of, our LinkedIn profile, Our Twitter handle, our Facebook identifier, our phone number … . It is the sum of the attributes we can and will share with others, be they individuals, governments, entities or organizations; as we establish relationships and prove to them who and often what we are.
Authentication – The method we employ to assure that you, based on the identifier presented, are who we (the relying parties) thinks you are. You are the person the relying party accepted when you registered that Identifier as how you would digitally identify yourself. By itself the method of authentication should not allow another party to be able to determine anything about your identity. Privacy is the goal. FIDO Alliance and W3C have defined standards to support authentication.
Verification – The process of confirming that the secret or biometric match the secret or biometric that where originally registered to that Identifier.
Identification – A means of authentication that is bound to your identity. A EMV payment instrument “Chip and PIN”, a PIV card, an electronic passport, a membership card, a drivers license, a national ID are all forms of identification issued by a party that should be trusted to have performed a proof of the individuals Identity, based on a defined and often published criteria.
This particular word, for many, has an alternate meaning. In the biometric community they see Identification as the ability to use a biometric to determine ones Identity. This is achieved by performing a one (the person present) to many match (persons registered). The goal is the same, bind Identity to the mean of Authentication by using the Biometric as the Identifier.
Proof – The method a relying party or an individual uses to validate your claim of a specific Identity. In many cases this is achieved by relying on knowledge of another party. The relying party accepts the due diligence to proof your claimed identity was done to their satisfaction by another party. This other party is often referred to as a Trusted party. This effort to proof the identity of an individual is linked to words and acronyms like KYC “Know Your Customer”, ID&V “Identity and Verification” and Self Sovereign Identity. We classically assume that documents provided by a Government e.g. drivers License and Passports are a solid proof of the claims asserted on those same documents.
In a digital world this is the most important element of a how we as people, entities, governments and corporations can be assured that you are who we believe you to be.
I am once again am reminded of the 1994 New Yorker Cartoon
The challenge of voice recognition and the need for multiple modalities to the question of authentication
A Good Mimic Can Bypass Voice Recognition Authentication, Research Suggests
The idea of voice many see as one of the more interesting biometric solutions as seen from an ergonomic perspective and something that can readily enhance the call center consumer experience and related security. The user simply needs to say something into a microphone (telephone) and presto they can be identified or authenticated.
But is it a safe and secure approach or simply the starting point for the identification and therefore associated with additional authentication processes.
Personally I am not convinced a voice is a good solution to the challenge of authentication. Yes, as one element of a multi-factor multimodal approach it is an excellent modality. But not as the only biometric modality. My fear emerged from a conversation with a sound engineer. She told me they could, at the level of a single vowel, splice and change the intonation of a word in a movie sound track.
The above article clearly identifies real world examples of voice biometrics being fooled and concludes by remind us that a multimodal solution is essential.
Classic Multi-Factor Authentication wants to pair multiple unique and none replicable elements together.
- Some thing you have
- Some thing you know
- Something you are
When I think about multi-factor authentication I wonder what would happen if the object “what you have” can be stolen. This therefore means the second factor must to assure that only the legitimate user is presenting the object. If a mime can replicate a voice, after stealing the object, then, this combination of factors can be compromised.
EMV, when implemented as Chip and PIN, matches a unique chip card (what you have) with a PIN (what you know). Apple Pay is EMV and stores the secrets and executes the cryptographic functions, inside hardware, the Secure Enclave (what you have) and combines this with a sensor to capture the Biometric (what you are). The electronic passport ICAO use similar chips and carries within it a facial image. The US PIV & CAC cards uses the same style Chip and are paired it with a fingerprint and sometimes also requires the user to enter their PIN.
Yet are they truly secure? We know Apple X’s, facial recognition, as currently implemented, can be fooled. We know that Touch ID was spoofed. Without liveness testing, most if not all biometrics, will accept a clone or replica of the biometric it employs.
The challenge is establishing the appropriate benchmarks for the various biometric implementations such that enterprises, governments, merchants and corporations can select and implement a consumer experience that satisfies the needs of security and convenience.
Acronyms like FRR, FAR and PAD become critical to selecting the appropriate implementation of a biometric solution.
- The False Reject Rate or FRR is all about convenience and not refusing the legitimate user. Perfection is a ratio of 0 in ∞
- The False Accept Rate or FAR is all about not approving a transaction or event by an imposter. Perfection is a ratio of 0 in 1
- The Presentation Attack Detection or PAD is all about addressing the reality that anything can be duplicated; therefore it is essential to make sure the biometric presented in alive and genuine. Perfection is a ratio of 0 in 1.
The challenge is establishing a balance between the cost and the acceptable FRR, FAR and PAD.
Measuring and establishing the test results of a particular element of a multi-factor solution is not cheap. EMV, PIV, ICAO software and “Secure enclave” / “Chip Card” / “Secure Element” suppliers spend 100’s of thousands of dollars developing and certifying the functional and security characteristics of the “what you have” element of these solutions. We know that passwords and PIN can and have been compromised with Phishing attacks and hidden cameras.
When we think about biometrics there is complexity in the read and match processes. When the user established their identity and their biometric the reference template is create. This reference template is then used in the matching process to identify if template resulting from the biometric just presented, is the same. Unfortunately reality dictates that each presentation of the user’s biometric will generate a unique result. This unique result will never absolutely match the reference template. Hence the need to understand and test the sensor and establish its FRR, FAR and PAD. The more foolproof the match must be, dictates the complexity of the solution and the number of different individual needed during the test process to establish the sensors FRR, FAR and PAD.
Therefore selecting the most appropriate solutions means quantify the risk of the event or transaction and measuring it against the cost and certified characteristics of the authentication mechanisms.
A layered approach that combines two or more factors must also considered including multiple modalities for at least the “what you are modality” is what we must consider. Using cryptography and hardware to address what you are, Passwords and demographic information to match what you know and layering various elements like location, behavior and some set of biometrics to understand who you are, will offer the highest level of security with the lowest degree of inconvenience.
Bottom Line Multi-Modal & Multi Factor
Authentication of Identification is what we must implement
Always mindful a modality will lose its ability to assure uniqueness
Over time.
We must take care when we speak or sell the power of that which may not be
I always enjoy reading the words David writes.
This particular post creates a moment to reflect. As we consider the implications of the Fourth Industrial Revolution, we must remember the significance many have attributed to Artificial Intelligence. Those two letters AI are clearly key to the what, why and wherefore of the change ahead.
Clearly machines that work faster, search deeper and are capable of studying vast realms of data are changing the nature of so much. Simply consider the risks to our security cyber hackers and terrorists wrought on this world or the shenanigans many claim the Russians use to disrupt as they explore and exploit the power of social media.
Moreover as we look afield many industries are being disrupted: movies, books, music, news … to name few. Outsourcing and robotics is changing the nature of work and the skills necessary to compete and ultimately survive to enjoy the pleasures available in our increasingly digital world.
David makes the point that the intelligence Isaac Asimov and other science fiction envisioned has not yet emerged. I think he is right. The message I take aware -we who market these solutions should walk forward with care.
People are clearly feeling threatened by the change impacting their towns, families and livelihood.
We must be mindful that complexity breeds confusion. Confusion drives disillusion. This then causes people to react, often in nonsensical ways.
Take On Payments
Federal Reserve Bank of Atlanta
How Intelligent Is Artificial Intelligence?
Posted: Nov 27, 2017 10:51 am
At the recent Money20/20 conference, sessions on artificial intelligence (AI) joined those on friction in regulatory and technological innovation in dominating the agenda. A number of panels highlighted the competitive advantages AI tools offer companies. It didn’t matter if the topic was consumer marketing, fraud prevention, or product development—AI was the buzzword. One speaker noted the social good that could come from such technology, pointing to the work of a Stanford research team trying to identify individuals with a strong likelihood of developing diabetes by running an automated review of photographic images of their eyes. Another panel discussed the privacy and ethical issues around the use of artificial intelligence.
But do any of these applications marketed as AI pass Alan Turing’s 1950s now-famous Turing test defining true artificial intelligence? Turing was regarded as the father of computer science. It was his efforts during World War II that led a cryptographic team to break the Enigma code used by the Germans, as featured in the 2014 movie The Imitation Game. Turing once said, “A computer would deserve to be called intelligent if it could deceive a human into believing that it was human.” An annual competition held since 1991, aims to award a solid 18-karat gold medal and a monetary prize of $100,000 for the first computer whose responses are indistinguishable from a real human’s. To date, no one has received the gold medal, but every year, a bronze medal and smaller cash prize are given to the “most humanlike.”
Incidentally, many vendors seem to use artificial intelligence as a synonym for the terms deep learning and machine learning. Is this usage of AI mostly marketing hype for the neural network technology developed in the mid-1960s, now greatly improved thanks to the substantial increase in computing power? A 2016 Forbes article by Bernard Marr provides a good overview of the different terms and their applications.
My opinion is that none of the tools in the market today meet the threshold of true artificial intelligence based on Turing’s criteria. That isn’t to say the lack of this achievement should diminish the benefits that have already emerged and will continue to be generated in the future. Computing technology certainly has advanced to be able to handle complex mathematical and programmed instructions at a much faster rate than a human.
What are your thoughts?
By David Lott, a payments risk expert in the Retail Payments Risk Forum at the Atlanta Fed
Europe Led the way with EMV yet Europe appears to prefer cash
Europeans still love paying cash even if they don’t know it
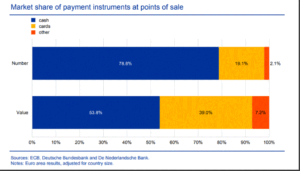
Interesting to reflect on how much we allow Europe to lead as we think about EMV and the technology we use to secure our payment cards. Maybe American’s need to embrace and take over the management of these key standards that drive an economy.
Identity and Payments
A presentation provided at the December United States Payment Forum to an audience of 50 plus individuals
USPF-Dec-2017- Identity_and_PaymentsDigital Identity
Words to ponder as we think about the best way to secure our digital persona.
Identifier – A text string we use to uniquely identify ourselves to a relying party, person, government, employer, club or entity we wish to have or need to maintain a relationship with. This group of entities hereafter will referred to as a replying party.
Identity – We each are unique and have attributes
Verification – A process the entity we seek to establish a relationship with uses to determine the truth of the attributes we share. One could argue this is or should be a mutual process. Many call this identity verification or identity proofing.
Registration – When we take these three words identifier, verification and identification and think about the first time we present ourselves to a relying party in the global digital environment. We typically present ourselves through a user interface to the entity we are interested in establishing a relationship with. We register and the relying party creates a record of our existence. They seek to recognize and record our identity.
This process typically requires us to invent or the relying party to present us with a unique identifier and agree to identify ourselves with this unique string, often called a user name, email address, bank account number, social security number, employee id, passport number, drivers license number or payment (card) account number ‘PAN’. The ultimate goal of registration is for the relying party tonassure themselves we are unique and that the attributes we share are linked to our person. They verify our identity.
Today the challenge is to find an efficient, convenient and none intrusive method of Verification.
Authentication – We exist, we can be recognized and are able to present oneself over and over again to the relying party, using our identifier. The challenge is how do we prove or assure our identity to the relying party each time. We need to authenticate ourselves.
Identification – Many confuse the dialogue above with this word. The difference is how we present ourselves or better said how the relying party expects us to present ourselves.
With the wide use of biometrics and many of the identifier we spoke of earlier, our identifier many not simply be some random string. A biometric is personal and linked to our body or actions. This biometric can be converted into an identifier and therefore once accepted as genuine and integrates the act of authentication into recognition of our identity.
Certain identifiers create a level of assurance, because the relying party trusts the attributes it asserts based on who issued that identifier. They are willing to trust in our identity and associated attributes because of the verification done by the isuing party. It a passport, an employee id, bank card or a drivers license. The instrument has characteristic, privileges and attributes linked to the issuing party, not simply attributes associated with the individual.
As we move from a physical world to a digital world. As people seek to use our identity to present themselves as someone they are not. As we seek to separate the various relationships we establish. Requires that we find ways of assuring our privacy while securing our relationships. All this demands we find more secure methods of authentication that are convenient.
Will Wal-Mart Pay surpass Apple Pay, Samsung Pay and Android Pay
Walmart Pay to surpass from pymnts.com – from the Washington Post. – and another
To open the news and find more than a press release in fact true commentary describing the success of a merchant mobile payment solution. This is big news and speaks to the value of loyalty and the power of largest global merchants willingness to focus and innovate.
Thinking about cards
In 1991 I had to learn the difference between million dollar transactions and hundred dollar transactions. As I came to explain, when telling my life story, I had to shift my thinking from 100 transactions at a million to 1,000,000 for a hundred. This transition took me from capital markets to payment cards.
Today, I wonder about the future of the ID-1 based payment card? A piece of plastic 3 3/8 x 2 1/8 with rounded corners.
In another blog I spoke of how this ID-1 object became a token responsible to act as the first factor, something you have. Printed, encoded and embossed characteristics were the security features. Today, with EMV as the global standard for payment CARD security; cryptography and the “secure element” replace those physical security with digitally mastered circuitry embedded inside something capable of protecting those secrets cryptography requires. We digitized the payment card. What we now must do is shift our vocabulary to tokens and credentials.
We need to embrace a new way of speaking we need to think about our “Payment Credentials”.
Today, we now tap our phone to pay, we use our phone to browse the internet, we shop & book tickets with apps and we listen to music & watch movies all from this device we apparently use, thousands of times a day. For those of us who remember computers that filled floors, we now are capable of buying more powerful computers, similar in size to those same cards. Think about the Raspberry Pi, a computer almost as small as a card, not quite! Yet!
The embedded secure element integrated inside our payment cards are being integrated into phones, bracelets, rings and things. The question; will they replace the card we are now comfortable with? Yes – maybe? Will we embrace these objects as the new carriers of our payment credentials? Many hope so.
In oder to think about the probability of cards disappearing, one must begin by think about the number of cards now in circulation. In round numbers we can think about 1.2 billion debit and credit cards, 300 million prepaid cards and 300 million retail branded cards. In round numbers, 1.8 billion payment cards. We next must think about our population and how many people now carry cards – 115 million households and 242 million Americans over the age of 16, according to a recent census. We now has a numerator and a set of denominators.
The question then becomes, how many payment cards does an American want to carry and how many payment credentials will an American end up having.
I would argue a debit card and a credit card is all we need to carry in our leather wallet, purse or pockets. Those other payment credentials can easily be accessed from wallets in the cloud or in our digital objects.
Merchants can integrate payment capabilities and focus on factoring their consumer receivables, behind relationships designed to service, thrill and sell. In an App and API enables economy, cards become a burden as the experience becomes the essential component of our lives.
ICO Independent Coin Offer
Fantasy or a new reality. November 2nd 2017 I attended a conversation about the legal, accounting and tax implications of an ICO. Nelson Mullins was our host and brought their legal might to the discussion.
Language is the first concern in embracing and understanding. The first phrase requiring an appreciation is the “White Paper”. For me, this is something people or entities write to explain a concept; most often intended to educate and inform. In the world of ICOs the meaning is very different. This document is intended to explain what the entrepreneur is trying to do and what the investor is investing in. In other word the “White Paper” is the “Business Plan” or better said the Prospectus.
Next word is “Security”. Here I must admit I was out of my depth. First let’s be clear, the use of this word is not about securing something, it is about an instrument one invests in and ultimately expects to profit from. Having spent 9.
Years immersed in Capital Markets understanding what stocks, bonds and commodities are, this should have been easy. The challenge is we are trying to figure out how to not be classified as a security.
To fully appreciate the discussion one needed to be steeped in the regulations and opinions of the courts and regulators at a national and regional “State” level. What I understood, a key reason ICOs emerged is as a method to avoid the complexity of the regulations surrounding the sale and trading of securities.
Next term is “token”. Once again a term we are constantly confronted with as we move from a physical to a digital environment. I am not exactly sure what a “token” is in the context of the ICO discussion, save ti say it represents something. I appreciate it is another term one must properly framed when discussing ICOs.
With these familiar terms with new meanings it is clear, this digital ecosystem built on the complexity of Block Chain, as a technology, is either a long term transformational technology or a magical mystery tour that will end in confusion and discomfort.
The Fourth Industrial Revolution
A new term was added to my learning today The Fourth Industrial Revolution. Better said the age of Disruption.
Is the common man able to embrace the change ahead. Yes, those of us who have the education, the experience and the desire to embrace change; can fathom this new world. What of those that live in the middle – what happens to them in this new age
The Fourth Industrial Revolution – A video to help people understand the change ahead
Then in this weeks issue of the economic
Money 2020 – 2017 – Las Vegas – Wednesday Digital Identity and Payments
With David Birch We asked the Question. Identity – Authentication – Identification – Authorization and ultimately verification, where are we.
Simple. We have the technology. We have the standards and more are coming. Authenticate, is done, use FIDO.
Identification with Biometrics is illuminatingly possible. Even the one I know how to spoof, Voice, with other factors layered in, does the job very well.
The challenge is Privacy and Confidentiality must be inherent while regulatory practices must be incorporated.
PA&A Money 2020 FINAL



