For some twenty plus years, I can remember hearing people speak of the dream of an economy without coin and paper money. A dream, driven by the desire to promote the use of electronic payments.
Over the last months, a number of articles focus on promoting the idea of a cashless society. They all speak to the advantages and attempt to promote the concept, arguing we can:
- Eliminate the concern of thugs insisting at gunpoint for the cash
- Reduce the risk of employee theft
- Stop paying people to count all those dirty coins
- Remove the need for an expensive safes
- Stop paying to have a specialist truck take the money to the bank
- Eliminate the grey market
The business case for a merchant to eliminate cash seems to be beneficial. Many have tried and succeeded to no longer accept cash.
At the same time articles report on the new regulations; various cities and states are implementing and considering. These regulations are intent on outlawing merchants from going cashless. The argument often focuses on how eliminating cash disadvantage the underbanked.
Then there is a reality! As a consumer, I recently have been surprised at the need to carry cash and the unsettling pleasure of finding out I still had cash in my leather wallet.
The first wake up to this reality took place while driving from St Simons, GA to the Orlando International Airport. In the trusting hands of Google Maps, I traveled down I-95, across I-4 and was directed to the FL-417. Suddenly a road sign informed me that I was on one of the various Florida toll roads. Above my head was a road sign indicating which lane, based on my preferred method of payment, to move into. Driving a car that was not mine and knowing it did not possess a PeachPass, my only option was cash.
Fortunately, I had cash and was able to continue my journey.
The following Friday my father and I went to The Lodge to play Sniff, a dominoes game. The game was competitive and cash was the only method to settle. With a bit of cash in my pocket, I was able to pay the few dollars I lost.
One Saturday a street vendor in front of the local Harris Teeter was selling spare ribs. When I went to pay they informed me, they only accepted cash. Once again I was fortunate, I had enough cash and was able to buy those delicious ribs for dinner.
On various Sundays, when the collection plate came around, I’ve had a check or a bit of cash and was able to leave my tithing.
On a number of occasions, the valet, tour guide or other service individual deserved a tip and I’ve had a few dollars in my wallet.
Two more events brought the reality of how society does not want cash to disappear.
One morning, I wanted to enjoy a pastry. Not having $2.75 to pay for the Danish, Sweet Mama’s, a local baker, charged me $0.50, an eighteen percent surcharge, simply to use a credit card
Finally, yesterday as a guest for lunch at the local Rotary Club, I was confronted with a series of cash only events. This time I did not have any cash and was not in a position to contribute to various worthy causes.
We dream of a cashless society. Yet churches, valets, toll booths, street vendors and the Rotary all continue to desire or require cash. Some are not even willing to accept anything but cash.
Looking at our society from two different angles, we must accept the continuing need for cash. Be it the underbanked, unable to acquire a credit or debit card; or those who carry many credit cards, both need to use cash simply to eat or enjoy life.
Later today I will have to visit the ATM and make sure I have a bit of cash in my wallet.
https://www.paymentssource.com/news/target-outages-show-the-failings-of-cash-as-backup
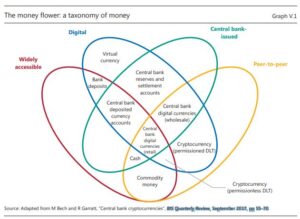
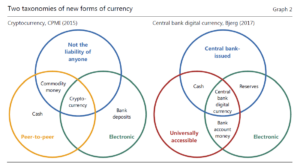

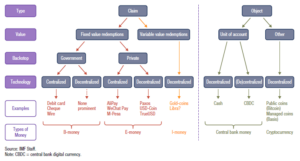
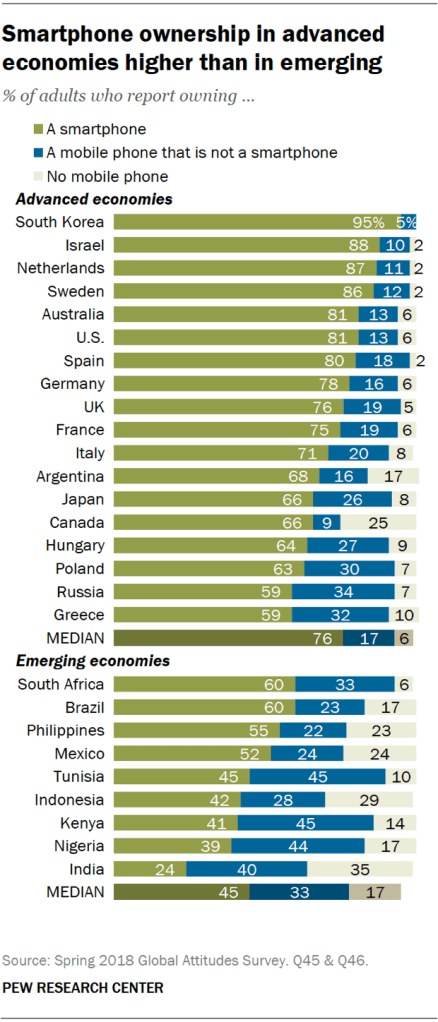








 will ultimately respond to the changes now taking place to how we Log-in to a website. Yesterday, or better said 10 years ago, we all understood that simple User Name password. A single screen with a reasonably consistent user interface. Sometime we might have to put up with two screens, One for the User name and the next for the password.
will ultimately respond to the changes now taking place to how we Log-in to a website. Yesterday, or better said 10 years ago, we all understood that simple User Name password. A single screen with a reasonably consistent user interface. Sometime we might have to put up with two screens, One for the User name and the next for the password.