https://andreae.com/Videos/Identity_basics
Today.
How many passwords are you trying to manage! Does your LinkedIn contact list connecting you to more than 4,000 individuals? Does Facebook, Instagram, and other social media websites inundating you with news and stories about your friends, colleagues and interesting people?
How many cookies have your computers accumulated? How many databases have more information about you than they need? If we search the dark web, how valuable is your data?
Cando seeks to help you manage your data, identity, assets, and relationships.
Philip lives on Sea Island with his 93-year-old father, the Doctor. They pursue travel and Philip keeps his head into what is happening in financial services, blockchain, authentication, digital identity, and, whatever else people seeking to understand the transformation; particularly those in the identity and payments space.
What is happening means we can unlock our hotel rooms, cars, and homes from our phones. Our security system iwill be another app we have to find on our phone.
Instead, we need an intuitive assistant seeking to simplify our lives by taking on repetitive tasks like driving, working inside a data table or simply opening up the house for the season.
Normalizing data and performing the analysis capable of earning value is the name of the game. Management is about stimulating a team to work in the mutual interest of the organization. Executives define the strategy and articulate the vision in a manner conducive to success.
Cando seeks to help you manage your assets and relationships. Assets those places and things you use doing your daily life and those interactions you have with people and entities seeking to serve, sell and partner with you.
Then there are friends who we expect to be part of our lives and therefore have privileges and access capabilities.
All of this with a target of selling integration services to the top million and simply assuring each person has an identity thus serving the bottom billion. ultimately earning $1 per year per user to simply be there when it all breaks and you wish to restore your digital life.
At the core, your digital security will be based on the use of cryptography and sophisticated matching algorithms designed to assure anyone that you are that one individual in the populatations of the universe.






Seven Words
I ran into this site today and am happy to see how Josh has offered a listing of sites, across multiple verticals, who have and have not embraced Multi-Factor Authentication.
What the primary factor is, is the key to the strength of authentication.
“What You Know” could be extremely secure, except we depend on the human to make sure they protect it, make it unique and complex.
“What You Are” can only be as secure as the quality and accuracy of the sensors and the algorithms used to match what is sensed now to what was registered then.
For me a “Restricted Operating Environment” capable of securing secret and private KEYS and use them to securely performing cryptographic functions, be they Symmetric and / or Asymmetric is the primary factor. The DEVICE(s) we use to access the service provided by the relying party simply needs to be registered, recognized and therefore the UNIQUE “What We Have” factor.
If we know the device is UNIQUE. Then the only outstanding question is, is the registered user using it, while not under duress. If the relying party is not comfortable with the presence of the registered user, then the Relying Party needs an additional factor to assure presence. Be it the “What You Know” and / or “What You Are” one adds to assure presence during the transaction or the authentication dialogue.
If the Relying party is comfortable the registered user is using their registered device, why add friction?
Prevention is what we need to focus on. Lock the door with strong keys . Detection is after the fact and necessary. Investigation helps to punish the evil doer and improve the quality of security.
We need to focus on making sure the methods used to allow someone onto the relying parties website or when they execute a transaction. Like in the physical world, it is about making sure the user’s KEY is unique and the right individual is in possession of the the key.
In other words. The user is present using a registered and recognized device.
Karen Webster
CEO, Market Platform Dynamics
President, PYMNTS.com
Karen,
Last week in your publication I read the article Deep Dive: Security In The Time Of Faster Payments and I had to offer the following thoughts:
The concept of Multi-Factor Authentication is based on the idea of layering multiple authentication techniques on top of each other.
We typically speak of three factors “What You Have”, “What You Know” and “What You Are”.
When we think of “What You Have” we think of a “Thing”. An object that cannot be replicated or cannot be counterfeited.
An object “a secure computer” that can be upgraded and made more secure as threats like Quantum emerge.
A unique object with a False Reject Rate FRR and a False Accept Rate FAR approaching zero.
In the physical world “the thing” is a card or passport. You will remember our first discussion, we came to agree the “secure computer” embedded inside provides a future proof mechanism. In the digital world, we depend on Cryptography. This Thing, inside our computers, mobile phones and other technologies; many refer to as a ROE “Restricted Operating Environment”. Technology people may call it a Secure Element, a SIM, an eSIM, a TPM, a TEE, an eUICC or even Security in Chip. Companies like ARM specialize in creating the design of these things and silicon manufacturers embrace and license their designs.
Today these connected devices (be they: personal computers, identity & payment cards, FOBs, mobiles phones, bracelets, watches and hopefully every IoT device) need to be secured. This array of cheap ~$1 security circuitry provides a place to create and/or store private keys & secrets keys, perform cryptographic functions and assure the integrity of the BIOS and software being loaded or currently running in these computers.
Think Bitcoin for a second. The key to its architecture is the Private Key associated with your store of coins. Lose it and they are lost. Many people store these in hardware, based on the use of a ROE.
The second factor is all about proving that you are present. Behavior, location, PIN, fingerprint or passwords are second or even third factors, be they something you know or something you are.
This is what FIDO and what WebAuthN is all about. Especially since they introducing the security certification regime. This is what the Apple Secure Enclave is and Samsung and others embed into their devices. This is what we put into payment cards, government identity cards and the Yubico keys we see various enterprises embracing. This is what Bill Gates started talking about in 2002. BILL GATES: TRUSTWORTHY COMPUTING
As we move to Faster Payments we must move to Secure payments. Immutability and irrefutably become key requirements. To achieve this goal I suggest we need to understand one fundamental security principle.
Today Wednesday October 18, 2017. I had the opportunity to provide the closing keynote to the EPCOR Annual Payments conference. Today, I was reminded of the reality that payments is not only about cards it is the engine that fuels the revenue of a financial institution. ACH, Wires, Cards, checks, transfers and even cash are revenue earning services; our community banks call payments.
My speach was about the future and focused on the evolution of our phone in this new digital age we all must learn to embrace.
Continuation of my running thoughts as I listen and participate at the Secure Technology Alliance.
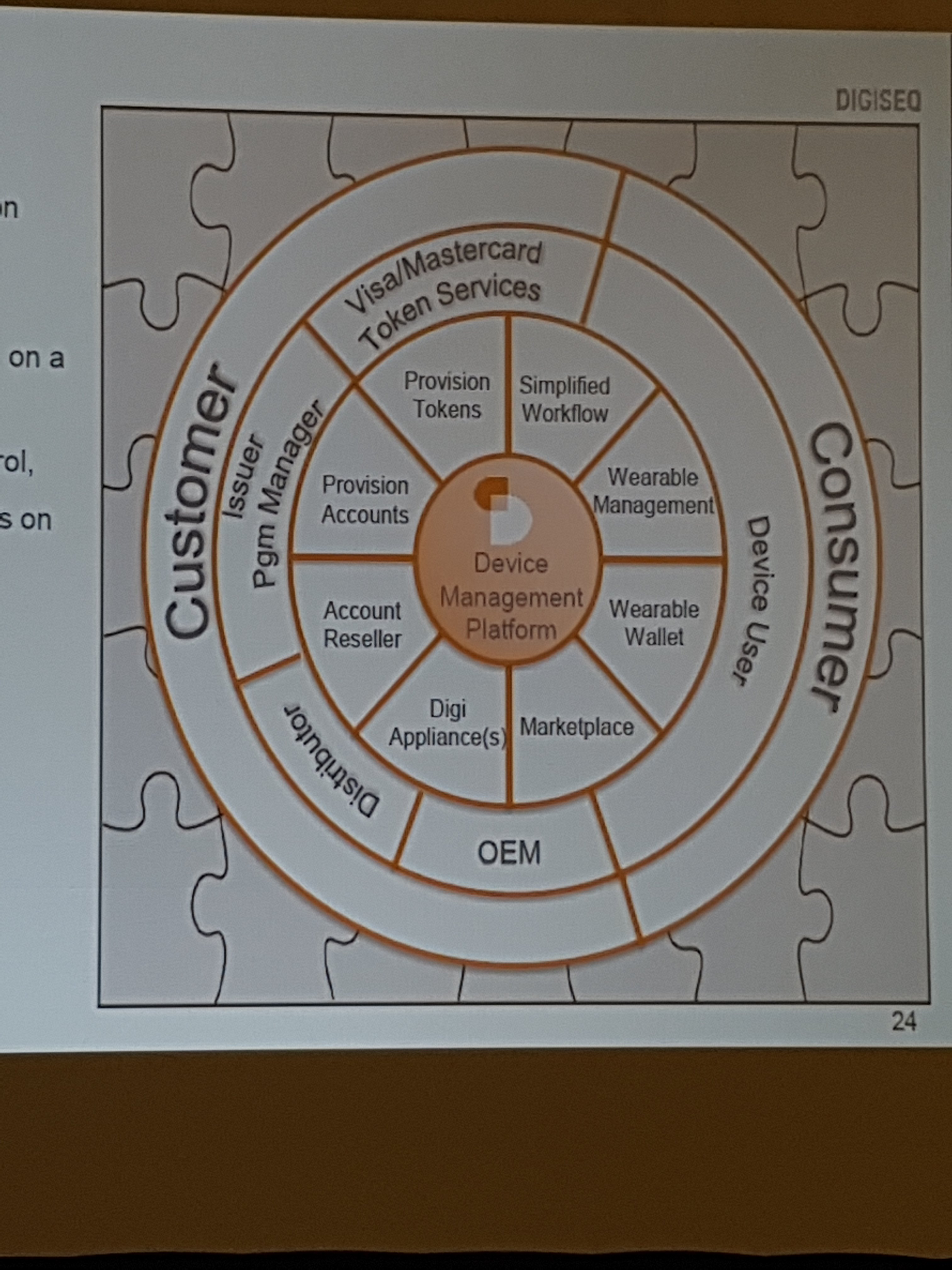
Secure element
Data management & personalization
Mobile device software integration
Device life cycle management
Tokenization as a methodology ans ecosystem is essential to the growth of payment in the IoT space.
Continuing the learning and commentary
IoT Payments 2017 – Austin TX October 10th and 11th
BASIC WANTS & NEEDS
MASS & PERMITTED RECOMMENDATION
SOCIAL & RELEVANT 1REFERRALS
ON-BEHALF
As he speaks of On-behalf a document produced back in 1996 must be found
Contactless cards and devices
The mobile ecosystem introduces the token requestor
A solid overview of the world of tokenization
- Like a card
- Mobile device (secure element)
- HCE
- Wearable are in market today
October 10th
Random comments offered as the various speakers speak at the conference at the Hyatt Regency Austin.
Lunch