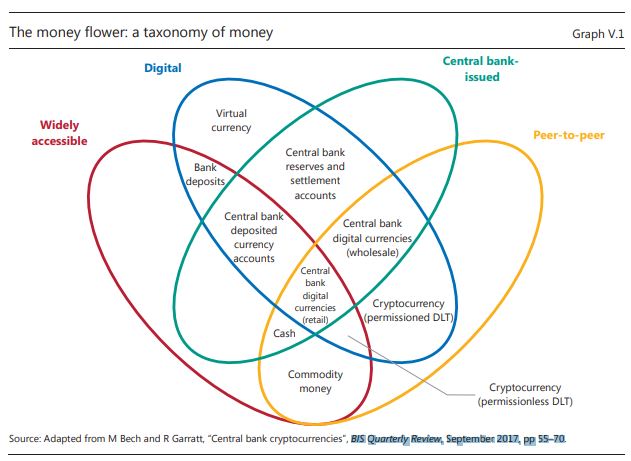
When we think back to history, we in the western world are brought up on the history of the Bible and the righteous position of the Jewish people. We are taught little of the growth and beliefs of the other regions of the ancient world. Egypt, Greece and Roman are seen as part of this history. The Persian empire is the enemy and that which is to the north and off to the east are known as trading alliances, maybe not people like those of biblical, Greek or Roman times.
One day a son is born into this culture. Pure of spirit and oh so wise capable of understanding much at the tender age of twelve. Already traveled, one can only imagine he continued to travel, to learn to embrace and to bring light to all he met. To imagine he traveled to the far reaches of the spice routes is so imaginable.
John 1
The Word Became Flesh
1 In the beginning was the Word, and the Word was with God, and the Word was God. 2 He was in the beginning with God. 3 All things came into being through him, and without him not one thing came into being. What has come into being 4 in him was life,* and the life was the light of all people. 5 The light shines in the darkness, and the darkness did not overcome it.
6 There was a man sent from God, whose name was John. 7 He came as a witness to testify to the light, so that all might believe through him. 8 He himself was not the light, but he came to testify to the light. 9The true light, which enlightens everyone, was coming into the world.*
In these words we learn of a teacher who will return. John his cousin, who did not travel east, instead shared beliefs and the letters he had receiving from this learned man. John’s childhood friend who traveled through and around all of the civilizations of ancient times.
Finally the thoughts and teaching from these other ancient lands and people would be merged together with the thoughts of Jesus’ original faith. A new loving and more holistic system of belief could rise binding all of human kind into one chosen people. One group of people not distinct from the other. All loved by the creator.
For some the idea all are equal is not easily, especially still, to accept. This is the great message we should have and must learn. This learned man moved around teaching, performing get things and creating a following embracing all.
The First Commandment
28 One of the scribes came near and heard them disputing with one another, and seeing that he answered them well, he asked him, “Which commandment is the first of all?” 29 Jesus answered, “The first is, ‘Hear, O Israel: the Lord our God, the Lord is one; 30 you shall love the Lord your God with all your heart, and with all your soul, and with all your mind, and with all your strength.’ 31 The second is this, ‘You shall love your neighbor as yourself.’ There is no other commandment greater than these.”32 Then the scribe said to him, “You are right, Teacher; you have truly said that ‘he is one, and besides him there is no other’; 33 and ‘to love him with all the heart, and with all the understanding, and with all the strength,’ and ‘to love one’s neighbor as oneself,’—this is much more important than all whole burnt offerings and sacrifices.” 34 When Jesus saw that he answered wisely, he said to him, “You are not far from the kingdom of God.” After that no one dared to ask him any question.
This is the greatest teaching to love one another, not to create divisions and ferment hate. Embrace each as you wish to be embraced is the true learning we must all learn.