Appendix 1 - 3DAS™ The Ultimate in Security
3DASä is a marker embedded into any object, for
example a credit card. Once embedded
into the designated object, 3DAS™ becomes that machine-readable token that provides
a coherent solution to all the issues surrounding assuring trust and insuring
security over the Internet.
 The digital interpretation of 3DAS™ is a unique
means of identification capable of authenticating and therefore guaranteeing
that the genuine object/card is present.
By binding data or transaction details to a unique read of 3DAS™ a
digital signature is established that assured the irrefutability of that card
being present when that data or transaction was altered or created.
The digital interpretation of 3DAS™ is a unique
means of identification capable of authenticating and therefore guaranteeing
that the genuine object/card is present.
By binding data or transaction details to a unique read of 3DAS™ a
digital signature is established that assured the irrefutability of that card
being present when that data or transaction was altered or created.
Using a simple 3DASä Reader connected to the
users PC and adding a unique 3DAS™ value as an index to a database, Unicate has
been able to create this authenticity of identity. Moreover, 3DAS™ can become the employee number, client account
number or credit card number.
By upgrading the 3DASä Reader to include an
integrated keypad, it is further possible to establish a relationship between
3DASä
and the cardholder’s 4 to 8 character password or PIN.
The Birth of 3DAS™ - the Ultimate Token for Identification and Authenticity
 In
1994 Unicate BV discovered that by employing non-woven fibers and stereoscopic
imaging technology, a physical authentication mechanism, “A Secure Token”, was
now available that is process efficient and impervious to external attack. The result of original research, conducted
by TNO the Dutch Research laboratory, revealed that the digital representation
of the 3DASä
"Three Dimensional Authentication System" is unique in a sample of 1036.
In
1994 Unicate BV discovered that by employing non-woven fibers and stereoscopic
imaging technology, a physical authentication mechanism, “A Secure Token”, was
now available that is process efficient and impervious to external attack. The result of original research, conducted
by TNO the Dutch Research laboratory, revealed that the digital representation
of the 3DASä
"Three Dimensional Authentication System" is unique in a sample of 1036.
In terms that are more technical, the False Acceptance Rate
FAR[1]
or "type one error" is one in 1036. The other key measure, the False Reject Rate[2]
FRR or "type two error" is one in a number approaching infinity. Compared to any known physical token or
human biometrics these results stagger the imagination and offer the users of 3DASä a
level of security and customer service that is near perfect.
3DAS™ Marker
 To take advantage of the unique power of
3DAS™, the un-woven fibers are put through a unique Unicate coating process and
ultimately inserted into a frame. This
frame is then affixed to or embedded inside a plastic card, paper check, brand
label or any other object that one wishes to be assured is authentic. Depending
on the application the marker can either be visible or invisible allowing the
security solution to be overt or covert.
To take advantage of the unique power of
3DAS™, the un-woven fibers are put through a unique Unicate coating process and
ultimately inserted into a frame. This
frame is then affixed to or embedded inside a plastic card, paper check, brand
label or any other object that one wishes to be assured is authentic. Depending
on the application the marker can either be visible or invisible allowing the
security solution to be overt or covert.
The
object now has a one to one association with a 3DAS™ Marker[3].
This physical token can be read at any time during the object's life and
by checking with an authority that has registered the 3DAS™ Marker one can be
assured that the object is the original one.
In
order to assure that the concept and technology was capable of operating in the
real world a series of trials took place in Holland. The results proved that under field conditions the 3DAS™ Marker
could be read accurately and that its integration into existing computer
systems could be achieved without significant effort[4].
Simultaneously, Unicate performed the necessary tests to prove that the
3DAS™ Marker adhered to all the ISO standards.
This therefore assures users of 3DAS™ that the marker will last longer
than the plastic card it is embedded in.
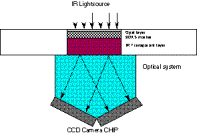
3DAS™ Reader
After the successful completion of the
trials, the Unicate team began the work to industrialize the optical element of
the reader and to miniaturize the sensor, processor, memory and electronics
used to perform the optical read and create a unique digital representation of
the 3DAS™ Marker. The production prototype
shown below resulted in a component designed to read the 3DAS™ Marker embedded
in a standard ISO 7810 plastic card integrated with an ISO 7816 Integrated
Circuit Card ICC.
 Inside
the 3DAS™ reader is an infrared LED, a light train, the sensor array, a digital
signal processor, a gate array, volatile and non-volatile memory, chip card
contacts and appropriate input output logic.
Given that its core function is to guarantee that an optic read has
occurred and that external agents cannot view what is taking place during the
processing cycle, security is inherent in its design.
Inside
the 3DAS™ reader is an infrared LED, a light train, the sensor array, a digital
signal processor, a gate array, volatile and non-volatile memory, chip card
contacts and appropriate input output logic.
Given that its core function is to guarantee that an optic read has
occurred and that external agents cannot view what is taking place during the
processing cycle, security is inherent in its design.
Unlike smart cards and other hardened
security devices, no secrets are stored within the device thus eliminating the
risk from an external attack. In the
event that applications employing 3DAS™ require enhanced security to protect
the algorithm or other persistent elements of application specific data, then
the design already includes the ability to add an ICC, like those used for the
GSM SIM, bank issued electronic purses and proposed by EMV.
Core to the 3DAS™ philosophy is that the 3DAS™ Reader must be able to fit inside any
device that one might consider using to authenticate an individual or
effect an electronic transaction. This
has led the Unicate team to further miniaturize the 3DAS™ Reader. Future releases of the hardware are being
designed in such a way that they can fit into set top box, personal digital
assistants, mobile phones and an array of emerging Internet access devices.
Later in the description of the 3DAS™
capabilities, there is a description of how to perform cardholder verification
using 3DAS™. In the case that this
function is required, a tamper evident keypad is integrated into the 3DAS™
Reader allowing the buyer to enter their PIN and then allowing the internal
logic to perform PIN verification or create a mechanisms to facilitate on-line
PIN verification without need for network security. The 3DAS™ solution eliminates the need for hardened security
hardware used to encipher the PIN during transmission.
3DAS™ Table
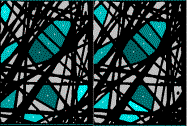 To
create the 3DAS™ Table, the optics generates a stereoscopic image of the 3DAS™
Marker on a single sensor (camera chip).
The result, as seen by the sensor, is two images. The first, the right view at +20°. The
second, the left view at -20°. These
two images result in a digital representation of the black or white value of
each pixel. In other terms, where the
filaments of the 3DAS™ Marker exist the pixel is black and the space between is
white.
To
create the 3DAS™ Table, the optics generates a stereoscopic image of the 3DAS™
Marker on a single sensor (camera chip).
The result, as seen by the sensor, is two images. The first, the right view at +20°. The
second, the left view at -20°. These
two images result in a digital representation of the black or white value of
each pixel. In other terms, where the
filaments of the 3DAS™ Marker exist the pixel is black and the space between is
white.
Working with this digitized image, the software
identifies the ten largest planes. The
process within the 3DAS™ Reader then calculates the area and the center of
gravity for each of these planes. The
software then sorts the 10 planes of the left and the 10 planes of the right in
descending order. The result is the
3DAS™ Table[5].
3DAS™ Key
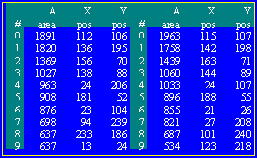 To
activate a 3DAS™ Marker the 3DAS™ Table must be registered in an organization's
database. The registration takes place
during the card personalization process and includes a few of reads of the
marker. The result of merging the 3DAS™
Tables creates the 3DAS™ Key. The 3DAS™
Key is then linked within the organizations database, to the card.
To
activate a 3DAS™ Marker the 3DAS™ Table must be registered in an organization's
database. The registration takes place
during the card personalization process and includes a few of reads of the
marker. The result of merging the 3DAS™
Tables creates the 3DAS™ Key. The 3DAS™
Key is then linked within the organizations database, to the card.
From this point forward card authentication
and identification is achieved by comparing a 3DAS™ Table to the 3DAS™
Key. If they match, the card is
authentic with a risk of one in 1036.
3DAS™ Algorithms
Since the initial trials of the 3DAS™ technology, the power
has been in the ability to apply the 3DAS™ Table. The first application saw the table as a pointer to a
database. The most recent innovation
has identified how to use 3DAS™ as a mechanism to secure information in such a
way that any number of copies can exist.
However, to read the data the 3DAS™ Marker, a trusted 3DAS™ Reader (with
the appropriate algorithm inside) and the owner of the information must be
present.
As Unicate looks to the Internet all of these algorithms can
be put too good use. The power is that
3DAS™ is a physical token not limited by mathematics. However, mathematics can exploit it.
During the development of a 3DAS™ solution to fraud problems
of the plastic payment card industry, Unicate discovered a series of additional
capabilities of 3DAS™. Most of these
resulted from determining that the entire 80 byte 3DAS™ Table does not need to
be transmitted to the card Issuer in order to guarantee unparalleled levels of
authenticity.
In fact, after consulting with TNO, it was determined that 8
bytes would produce a FAR of 1 in 60 billion and by increasing the number of
bytes transmitted to 16, results in a false acceptance rate of 1.5x1021. These findings allowed Unicate to propose a
solution to the payments industry that does not require any modifications to
the numerous systems that attach the point of sale device to the Issuing Bank's
host. More importantly, Unicate was
able to create a solution that secured today's magnetic stripe and cheap secure
memory chip based relationship cards.
Bottom line, Unicate has designed a series of functions that
assure the Identity, Authenticity, Irrefutability, Integrity and Uniqueness
of any object and the transactions it engages in.
The 3DAS™ FastKey
The 3DAS™ FastKey is an extract of the 3DAS™ Table that can be used as a common index to extremely large databases. The 3DAS™ ™ FastKey is the digital representation of a physical key belonging to an object, card or person.
A simple application of the 3DAS™ FastKey is to use it as the employee's key to corporate access control systems. The solution requires a simple plastic card with a 3DAS™ Marker inside. The 3DAS™ Marker is read at a door, a security gate or the terminal with access to corporate secrets.
The 3DAS™ Reader would create the 3DAS™ FastKey and request from the corporate security database permission to allow this person through a particular door in a building or campus complex. An inexpensive solution that is impervious to attack, easy to install and comparable in price to the magnetic stripe and PIN based systems in use today.
Unlike today's magnetic stripe cards, or for that matter chip cards, a 3DAS™ Marker cannot be duplicated. It must be located from within a pile of 1036 markers.
The algorithm implemented within the 3DAS™ Reader to create the employee id simply must know the length of the security systems database's index and understand which elements of the 3DAS™ Table will be used to define the 3DAS™ FastKey. In essence, the 3DAS™ Marker becomes the employee’s identity card. Thinking in terms of payment systems the 3DAS™ FastKey can be an account number.
As an example, using the 3DAS™ Table represented on page 5, and applying an organisations specific algorithm[6], the 3DAS™ FastKey of this marker would be 112 106 136 195 115 107 142 198.
The 3DAS™ FastKey is the unique an indisputable means of identifying that that physical token is or was present and read by a 3DAS™ Reader.
The Hash
In the development of solutions to assure the integrity of data transmitted electronically, mathematicians have been exploring the field of large numbers. During their research they have developed a series of mechanisms that allow one to calculate a value that offers the sender of electronic data assurance that the receiver of the same element of data will know that no one has altered the content of the message. Simultaneously these mechanisms, unlike what we all learned in mathematics, cannot be reversed, they are "one way" functions. Because of this unique property and their acceptance in the marketplace, they have become an integral part of the 3DAS™ solution.
To receive the assurance of data integrity the recipient simply takes the data received and performs the exact same mathematical calculation. The result will be a value that must be the same as the value calculated by the sender, or, the recipient knows that data has been altered.
Various forms of these algorithms, a Hash, have been defined and tested by a number of recognised authorities. Which Hash algorithm is employed is not important, the only requirement is that all parties agree on the one that will be used.
In the E*MERGE® solution, data pertinent to the terms of the payment transaction are input into the Hash calculation, thus, providing the consumers, merchants and banks comfort in knowing that the contents of the transaction have not been altered by outside parties.
What the Hash does do is provide data or transaction integrity. The Hash does not provide a means of identifying and authenticating who sent the message. To achieve this more important task of identification and authentication of the parties engaged in the transaction is where the 3DAS™ Marker is employed.
3DAS™ Signature
The 3DAS™ Signature is the means of assuring the parties engaged in a transaction that the identity of the individual involved in the transaction can be authenticated and that the Hash can be proven to be the one created by that individual. In the case of a payment transaction, it proves that an authorised seller and an authorised buyer were present and executed that particular transaction.
To achieve the security goals of authenticity, irrefutability and integrity the only requirement is that the party interested in being assured of the identity of the physical token register the 3DAS™ Marker in their database. In the E*MERGE® payment system this means that the Consumer Bank and the Merchant Banks register the 3DAS™ Marker of their customers card.
To be able to assure authenticity of who signed the transaction, the party who registered the 3DAS™ Marker simply compares a 3DAS™ Signature they create, using the 3DAS™ Key stored in the database, to the 3DAS™ Signature generated, by the 3DAS™ Marker, used to sign the transaction.
To create a unique 3DAS™ Signature for each transaction, a Hash is created over pertinent data such as the terms and condition, the date, the time and the location of the transaction. This Hash is submitted to the 3DAS™ Reader. The reader uses the Hash as a set of pointers[7] to select values from the 3DAS™ Table of the optical read of a 3DAS™ Marker present at the time of the transaction. The resulting 3DAS™ Signature provides irrefutable proof that the card belonging to the person authorising the transaction was present.
Upon receipt of the Hash and the 3DAS™ Signature, the bank duplicates this process using the 3DAS™ Key as its equivalent of the read. By comparing this value to the 3DAS™ Signature just received provides irrefutable proof that the card was present.
If irrefutability of the terms of the transaction is the requirement then all that is required is that the bank receives the data (terms and conditions) that was hashed, and the original 3DAS™ Signature. By using the 3DAS™ Key as its base, the bank can re-compute the Hash and the 3DAS™ Signature and prove that those are the terms and conditions that the parties agreed to.
In the event that the cardholder disputes that their card was present, then by simply asking them to submit their card as part of the dispute resolution process the bank can use the 3DAS™ Card to re-calculate the 3DAS™ Signature and prove that that card was or was not used to sign the transaction. Obviously, if the card was stolen then the same issue exists as today unless PIN was also used. The cardholder must report this event allowing the Issuer to block future transactions.
The Unique 3DAS™ Transaction Serial Number
One of the properties of the 3DAS™ system is that each optic read of a 3DAS™ Marker is a random event. Therefore, converting this random characteristic into a digital value creates a unique serial number. This unique value can then be used to assure the bank that no one is attempting to defraud the system by signing multiple transactions with a single read of a 3DAS™ Card.
This random feature results from the fact that each sensor converts a visual image into a digital image based on a defined number of pixels. Each time a card is read the position of the marker is spatially unique, therefore which pixels are black or white will never be the same. In the case of the X and Y values Unicate has developed software specifically to eliminate the randomness of the output whereas in the case of the areas of each plane the randomness has been emphasised.
Combining an appropriate set of these values creates a unique serial number. This data element is then included in the message. Later the recipient checks this value against any previous message making sure there are no duplicates. This assures the Issuer this transaction was signed by a unique read of a 3DAS™ Marker.
On-line Card and Data Authentication
The first enhance Unicate can offer to the typical credit card payment process is to develop a means of assuring in an on-line authorisation request that the card present is the one that the Issuing Bank had registered to that cardholder. To achieve this goal, a Hash (see page 5) and a 3DAS™ Signature (see page 5) of each transaction is created. This digital signature guarantees that the transaction details were not altered and the card was present. Next, the 3DAS™ Reader creates the unique transaction serial number (see page 5). This unique value assures the Issuer that this transaction resulted from a unique read of the 3DAS™ Marker. As the ultimate warning, this unique transaction serial number can identify any duplicate transactions generated by fraudulent merchants or criminals.
The 3DAS™ Signature and the unique transaction serial number are transmitted within both the standard authorisation and clearing messages to the Issuer’s host. Once received, the Issuer can authenticate the card in the 3DAS™ Reader and issue an authorisation. In the case of the clearing message the Issuer is in a position to further validate the transaction before authorising payment.
In reviewing the specifications of the authorisation and clearing messages of Europay, MasterCard and Visa, Unicate identified two existing fields that can carry this information without modification to the intervening systems. The net result is an on-line solution that requires the inclusion of the 3DAS™ Reader in the terminal and two modules within the Issuers environment. The first module adds the 3DAS™ Key to their database. The second, to compare the 3DAS™ Table to the 3DAS™ Key when an authorisation or clearing transaction is received.
When considering typical business to business transactions, the key is to be assured that the person present is authorised to transact and that the content of the instructions are as entered. When considering other types of transactions simply substitute the appropriate transaction for the authorisation and clearing message, just described, and the organisation can achieve the exact same guarantee of card authenticity and transaction integrity.
Off-line Card, Data and PIN Authentication
Merging the 3DAS™ technology with the power of Public Key cryptography "PKi" Unicate has been able to develop a series of algorithms in the 3DAS™ Reader. These algorithms assure the seller, off-line, of the authenticity of a card, the integrity of data associated with the card and optionally that the rightful cardholder is present.
By creating a digital certificate, a card authentication method "a CAM" and optionally a cardholder verification method "a CVM" is available. To create the certificate the 3DAS™ Table along the data on the card and optionally the buyer PIN is Hashed together and signed with the secret component of a public key algorithm. This is then stored in track three of the magnetic stripe or within an inexpensive memory chip.
The certificate allows a public key algorithm within the 3DAS™ Reader to authenticate that the 3DAS™-enabled card is present, the data is unaltered and the consumer knowing the PIN is there with unparalleled accuracy and at an extremely reasonable per card cost[8]. When the card is present, the 3DAS™ Marker is read, the appropriate data is retrieved and optionally the cardholder enters their PIN. A standard algorithm within the 3DAS™ Reader is executed and it uses the appropriate public key to validate the certificate. The result, without the expense of on-line communications, the merchant has irrefutable proof of the authenticity of the card, the data and the cardholder.
3DAS™ Can Protect Today’s Magnetic Stripe Payment Cards
While validating the ability to implement the 3DAS™ off-line PKi based solution, it became clear that many countries employed track three and many banks could not justify the expense of implementing even cheap chip cards.
This meant that Unicate had to create
a new algorithm that could provide an off-line CAM that could use a certificate
that was a maximum of seven digits[9]
long.
Unicate
created a solution that offered a level of protection (6.5 million to one) with
certain associated risks[10]. The solution employs a randomising algorithm
that can use a mere four digits to provide a CAM. In order to protect the algorithm, it is stored and executed
within a smart card chip identical to those supporting EMV[11].
Furthermore,
there is minimal financial risk to the banks.
The clearing message contains the much more robust On-line CAM employing
the 3DAS™ Signature. Therefore, no payment would occur unless the merchant can
prove they are not in collusion with the cardholder who has broken the secure
algorithm.
Like
the on-line approach, the off-line approach does not require any modifications
to any of the network and systems between the POS or ATM device and the Issuers
host.
Cost-effective Implementation of an On-line PIN
Today's use of PIN demands encryption of the PIN inside a secure box at each point on a network where it passes to another legal entity. A typical debit card transaction could involve transiting nine security modules with five sets of security keys and associated procedures.
The
Unicate team has designed a means of implementing on-line PIN without the need
for expensive cryptographic hardware or associated technology inside the
Internet or today’s secure networks. To
achieve the result Unicate acknowledges that the PIN is simply a piece of data known to two parties: the
Issuing Bank and the cardholder.
By
requesting the cardholder to enter the PIN into the keypad, that optionally
comes with the 3DAS™ Reader, the reader is in a position to produce a 3DAS™ Signature
that hides the PIN from anyone but the cardholder and the secure computer
system of the Issuer.
To
provide cardholder verification, the Hash of the transaction and the PIN are
merged together, using Modulo 16 arithmetic, by the 3DAS™ Reader. The resulting
value is a set of pointers used to produce the 3DAS™ Signature.
Knowing
the PIN the Issuer is able to replicate the calculation and create a 3DAS™
Signature from the 3DAS™ Key. The two
3DAS™ Signatures are compared and if they match the Issuer is confident that
the card is present, then that card is
authentic and the cardholder entered
the correct PIN.
The 3DAS™ Tunnel
Data confidentiality is a critical issue when an organisation considers the sensitivity of data that it may wish to provide to its mobile work force over the Internet. Built into most browsers is either SSL or PGP: both tools to provide a measure of confidentiality.
Unicate began looking at the issue of confidentiality not from the perspective of the Internet but from the perspective of data carried by an individual in an inexpensive protected memory chip or a diskette. What Unicate is able to create, is a solution that enciphers the data by deriving a symmetric key from the 3DAS™ Table employing a password known to the individual authorised to read the information. To achieve the result the encrypted data is read, the 3DAS™ Marker is read and the authorised individual enters a password. Software in a 3DAS™ Reader designed to support this capability then decrypts the data and returns it to the authorised individual. When altered, the authorised individual resubmits the data to the specially configured 3DAS™ Reader and the information is re-encrypted.
When Unicate began to look at the Internet it developed a way of adapting this process to allow the server that has a registered copy of the 3DAS™ Key to send a challenge to the PC who would present this challenge to the 3DAS™ Reader. The 3DAS™ Reader would return a key 3DAS™ that could then be used as the symmetric session key by SSL or other line or data encryption software. The mechanism makes it possible to tie the encryption of client specific data to the 3DAS™ Marker and eliminate any dependency on exchanging keys over the network or requiring keys to be stored within software in a PC. 3DAS™ is capable of establishing data confidentiality.
The
All in One Solutions
3DAS™ the Simplest Means of Identification
By exploiting
the power of 3DAS™, Unicate has been able to create a solution that allows an
organization to identify and authenticate both off-line and on-line its card
bearing clients or employees. 3DAS™ can
then be employed to create irrefutable proof that the card and
cardholder were present and did execute the transaction.
Considering the
growth of business-to-business eCommerce and the desire to be able to provide
secured access to business partners and effect transactions in a secure and
confidential way the 3DAS™ family of services is one of the most effective
solutions available.
3DAS™ & E*MERGE® the Securest Means of Payment
When
considering the world of consumer to business eCommerce the issues that must be
addresses begin with the need for a means of authenticating both the buyer and
the seller but it also requires a means of payment that does not demand the use
of cryptography to protect the sensitive payment details from external
elements. This protection of consumer
and merchant details is the responsibility of the banks, the third party to any
payment transaction.
3DASÔ affords the Issuer secured irrefutability by card authentication, cardholder "PIN" verification and unique transaction integrity. Simultaneously the 3DAS™ solution makes sure that the Acquirer remains in complete control of the merchant relationship, UNLIKE the EMV approach that transfers the decision to go on-line from the merchant's terminal to the smart card.
The power of the off-line authentication method is that can be used to protect today's magnetic stripe cards with the robust on-line authentication method that will assure that only authentic transactions involve the transfer of money. Unicate has created a solution that allows the payments industry to bridge the period between today and when track three can be made available or the Issuers decide to add inexpensive (.15 to .20 US dollars) protected memory chip cards to create customer relationship cards. This approach is a cost effective solution to fraud and a profitable strategy focused on allowing the Issuers to segment their card portfolios and only offer relationship programs requiring additional memory capacity of a 3DAS™ secured inexpensive chip cards to their profitable clients.
The net result is that
Unicate expanded the capabilities of the 3DAS™ Reader from simply analyzing the
digital image to also perform the following on-line and off-line functions;
·![]() On-line account identification
On-line account identification
·![]() On-line card authentication
On-line card authentication
·![]() Off-line card authentication
Off-line card authentication
·![]() On-line data authentication
On-line data authentication
·![]() Off-line data authentication
Off-line data authentication
·![]() On-line PIN verification
On-line PIN verification
·![]() Off-line PIN verification
Off-line PIN verification
·![]() Generation of a digital signature or transaction
certificate
Generation of a digital signature or transaction
certificate
·![]() Protection from replay with a unique transaction
serial number
Protection from replay with a unique transaction
serial number
3DAS™ and the Chip Card
One of the most important results of the work Unicate has
been doing to develop a solution to the banking industries payment card fraud
problem, is the recognition that 3DAS™ offers an effective way of employing
inexpensive (.15 to .20 US Dollar) protected memory chips. 3DAS™ is able to provide all the security
benefits much more expensive smart cards claim to provide, for a fraction of
the cost.
By using 3DAS™, public key cryptography and these
inexpensive protected memory cards Issuers can quickly introduce profitable value-added
programs to targeted segments of their cardholders. These applications are assured that only authorized entities can
alter the data held within the cheap memory and more importantly can link that
data to a unique 3DAS™ Marker and the bona-fide cardholder, thus protecting the
Issuer from external fraud and consumer abuse.
By simply reading the 3DAS™ Marker and the data held within
the memory and verifying that the data and the marker belong together and are
unaltered provides all the protection loyalty schemes, electronic ticketing
programs, stored value systems, identification mechanisms, logical access
controls and consumer information profiles require.
The 3DAS™ Business Case
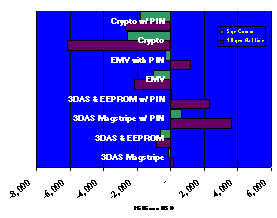 As
part of the work to develop a business proposition for 3DAS™ as the cost
effective solution to the problem of fraud on plastic payment cards Unicate
developed a set of business cases that demonstrates that 3DAS™ is the most cost
effective means of creating a Card Authentication Method as well
as enabling a secure Cardholder Verification Method. The banking industry would no longer suffer
losses resulting form counterfeit and lost & stolen fraud.
As
part of the work to develop a business proposition for 3DAS™ as the cost
effective solution to the problem of fraud on plastic payment cards Unicate
developed a set of business cases that demonstrates that 3DAS™ is the most cost
effective means of creating a Card Authentication Method as well
as enabling a secure Cardholder Verification Method. The banking industry would no longer suffer
losses resulting form counterfeit and lost & stolen fraud.
In this graph data
acquired for USA Visa and MasterCard cards in issue, terminal population, transaction
values, transactions volumes and fraud levels circa 1996, were put through a
model similar to the one employed by MasterCard and Europay when they justified
the migration to smart cards. Please
note that this model grossly underestimated the implication of systems changes
imposed by EMV and yet it still demonstrates that the 3DAS™ approach that does
not have these same costs is significantly less expensive.
The results are clear. 3DAS™ is the only solution that makes economic sense.
The Migration to Customer Relationship Management
As banks work to improve
shareholder value, the focus has shifted from product to customer
profitability. With this focus on
customer relationship management, banks now recognize that 10% of their clients
generate 110%[12] of the
profit. The realization that many
clients are not profitable has lead segmentation of the custom and unique value
propositions that serve the interests of thee profitable client while
maximizing the bank's return on investment.
The 3DAS™ solution is 110% compatible with this approach. The solution allows an Issuer to determine
when it makes sense to spend money to expand the feature functionality it
offers its clients. It does not force
them to implement expensive smart card technology on a portfolio wide basis, as
EMV seems to suggest, simply to achieve the tangible and intangible benefit of
fraud reduction. Instead, it protects
today's investment in magnetic stripe technology while leveraging the expanded
memory capabilities afforded by inexpensive chip cards to those individuals in
its portfolio that will generate a profitable return.
Furthermore, once a bank
determines that it makes sense to add new value added programs to its cards the
security provided to the basic credit or debit function is instantaneously
increased. Migrating from off-line
authentication of the magnetic stripe to off-line authentication using e2PROM
and PKi enhances security. The result,
security increases from 6,500,000 to 1 to 1,000,000,000,000,000,000,000,000,000,000,000,000
to 1 and the risk is that someone can replicate a specific 3DAS™ Marker.[13]
The Unicate approach is
an affordable approach to creating consumer value while also affording fraud
protection without the enormous up front expense of EMV.
The 3DAS™ solution affords all of the requisite requirements
of a robust security solution. It
assures the identification and authentication of the token (the card)
associated with the person performing a transaction. By providing a means cost
effective means of verification,
assuring that the person holding the card is the rightful owner, the solution
is then complete. The 3DAS™ Reader
finally provides a digital signature and a transaction identifier designed to
guarantee that the transaction is both unique
and irrefutable.
All of this security,
without the need for complex cryptographic or expensive and disruptive changes
to the existing EFTPOS networks and systems.
Moreover, the one element never qualified in the EMV business case, the implementation of an infrastructure to
create the opportunity to create value added services, is finally cost
effectively assured.