After a conversation about my four Chat GPT produced

After a conversation about my four Chat GPT produced

Which God was asked
The God
Was answered
Who is this God was asked?
The one creator.
The one beginning that which always was and always will be.
It is so easy to write blasphemous Tweets, or conspiracy nonsense. Our digital age has given those who cannot find love a channel to express anger and frustration. They expose their lack of empathy, and their inability to grasp the basic peace established Via love.
I must begin with an apology to the lady who caused me to start this post. I am sorry about how things evolved, yet I am thrilled at a new beginning. I was looking forward to exploring what could be now I am.
I also appreciate how my spiritual foundation differs from many. In this post, I will attempt to share what I believe.
There are four great teachers Lao Tzu, Siddhattha Gotama, Confucius, and finally the King of Kings Jesus. To these four, we must add the Chinese, Egyptian, Greek, and the other great scholars whose words graced the libraries of Alexandra and other great centers of ancient learning.
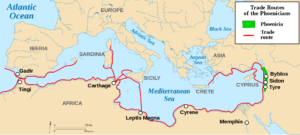
 Jesus, between age twelve and thirty, I suspect, walked the northern silk route and traveled home along the southern maritime route, searched, and explored all of their thinking. He probably voyages around Europe with the Phoenicians.
Jesus, between age twelve and thirty, I suspect, walked the northern silk route and traveled home along the southern maritime route, searched, and explored all of their thinking. He probably voyages around Europe with the Phoenicians.
When he emerged, he taught.
He was a truly enlightened man.
He taught us a new way of living together.
He was the conclusion of all of the world’s thinking into one simple rule. In order to honor the creator God, we must adhere to the Golden Rule.
Stories told of Jesus established a deep feeling of love for Jesus son of Mary and Joseph a martyr who died on the cross preaching peace and harmony.
I f only those in power had embraced the love, he shared. Instead, they took control of the image of Jesus and God.
f only those in power had embraced the love, he shared. Instead, they took control of the image of Jesus and God.
Instead, those in power use his name and their version of his teaching to assure their GREEDY, that one sin, need for wealth and power. I then must simply remind all of you of what Lord Acton said – “Power tends to corrupt and absolute power corrupts absolutely” (1887).
Western civilization wants to claim it is superior. In earlier times the lord God was used to establish the power of the monarch. The hubris of one tribe to claim their Book was better than any other book is where the division across this great planet emanate.
That arrogant better than thou feeling is our greatest sin.
Look at the tower of Babel. We once were one. The people who wrote that passage wrote of our inability to work together. They blamed God for our human failures. The story is of us. Instead, we turn the text around and blame God for our inability to live together in peace.
My return from a world where chaos ultimately produced the order we see 》 Happened in 2005 while living in Canada. 19 year abroad thinking of coming home. I stopped drinking; we joined the three-week-old community church in Markham, Ontario. There, I began to study the bible. When I came back to the United States in 2008 and settled for a time on St Simons Island, Georgia, I joined the local community church. Moving up to Atlanta, I joined with my sister and attending Johnson Ferry Baptist Church.
Is that not what Jesus told us was our task?
I was taught that he died on the cross so in his name we would come together as one, both Gentile and Jew? Instead!
What happened next resulted from several evangelicals better than thou experiences.
This better-than-thou attitude caused me to run back to the Episcopal church.
Party, nationalist, MAGA, slave owner, racist, sexist, cults, schools, churches, temples … whatever holds one group together divides us. This is our failure.

With this ancient depth, even he has not convinced those now living and those who came before to come together as one family. He asked us, in the name of the creator, to be the stewards of this planet and friends to any who enters our space.
This is who we are expected to be
Look at us today. We have not been true to his teaching.
Those that follow, including Mohammed, Luther, Calvin, Joseph Smith, Guru Nanak, and so many others, sought to promote their unique way of thinking. Instead, they ended up creating even more division.
In 2017 my mother died. It was late February. We had just elected a racist President. Two priests Robert and Tom stood talking as friends. Of two different disciplines, these men told me the local spiritual leaders met for Lunch – Dinner – Musical … whatever.
Years later Tom and Allan (Robert’s replacement) along with the local rabbi took a group to Palestine.
They told me who did not wish to be part of their ecumenical movement.
The Imam did
At the beginning of 2020, living once again in the Golden Isles, I attended three of the churches here on St. Simons. I listen with great respect to Alan & Tom as they tended to their Presbyterian and Episcopalian flocks. I also had a chance to experience Catholics sharing their faith. The feeling of being connected to God is absolutely present in each of these congregations.
I stayed away from most people during the pandemic, especially those rude people who would not wear a mask and do not want to accept the free vaccine and become part of the herd immune society.
A lovely woman asked the question of my spiritual beliefs.
https://www.albany.edu/faculty/miesing/teaching/assess/hell.html
In my many reading, this essay has caused me to want everyone to remember one thing.
The question the student causes me to ask each of you.
Ea ch time I reread the student’s essay, I find the humor and feel the deeply thought words. I then wish all could accept this simple thought.
ch time I reread the student’s essay, I find the humor and feel the deeply thought words. I then wish all could accept this simple thought.
When it comes to spirituality, everyone is right. No one is wrong. None of us can truly understand the mysteries of the unknown.
While cycling one beautiful afternoon along the Chattahoochee, I listened to one particular way of interpreting the Tao.
After listening to the full series, the Trinity became nothing more than an element of the mythology used to help people find a common purpose.
For me, our purpose should be to find union with all. People should not insist we all believe in the Jesus described in the Nicene Creed. Instead,
Many tell me I must give God my full and undivided attention. They tell me he will fill my mind with heavenly wisdom and knowledge.
They tell me – he has plans for me.
They tell me they see and hear greatness in my ideas. Can it be true?
Is God calling and asking me to step up
Reach higher and prepare to do more than I can imagine?
My therapist believes I have a calling. Others cause me to fear the burden God wants to place on my shoulders. The woman who caused me to write told me she heard greatness in my ideas.

In 1976 I grasped hardware, software & networks achieving the equivalent of a 4-year master’s in computer sciences. 1982, while replacing the back pages of the WSJ with computer screens, I saw how marginal satisfaction is not a human instinct and was confronted with trying to grapple with the advantages and disadvantages of socialism and capitalism. 1986 off to Europe for 15 years.
1991, I moved into senior management and saw the world through the eyes of Mastercard and Visa. I helped them grow while focusing on securing the world of payments and heralding in eCommerce.
The fourth industrial revolution is underway; it calls us to embrace machine learning, natural language interfaces, 3D printing, and the internet of things.
How God fits in begs the question of why God would put Putin and Trump in power. Why would income inequality be so raw and health a profit center? Those waving the Trump and MAGA flags worry me. Their supremacist attitude solidifies for me one thing. Tribalism is our greatest sin.
 Stop believing in the absolute truth of One book. Instead, we need to collectively believe in the one creator who taught the four or more ancient scholars the truth. They all have one common message.
Stop believing in the absolute truth of One book. Instead, we need to collectively believe in the one creator who taught the four or more ancient scholars the truth. They all have one common message.
It is time to listen and embrace
The Golden Rule.
If this is my destiny, I need help. I need the OMI cheerleader. Moreover, I need to meet men and women of faith who have experienced a truth and have grown to see the truth.


Jesus the King of the World for 18 years wandered this earth. As our teacher he stands before us with one truth. Love each other. In so doing you love and honor God.
Matthew 25:40 And the king will answer them, ‘Truly I tell you, just as you did it to one of the least of these who are members of my family,* you did it to me.’
Such big words. The idea something is once written can never be changed, altered, or deleted as well as elegant. Or that there is no need to worry about anything, what is presented simply is one instance of knowledge not until more than two can be found is there the possibility of trust. But if more than a few assemble and not sure then!
In a trustless environment, there is no single entity that has authority over the system, and consensus is achieved without participants having to know or trust anything but the system itself. A definition from one of the major institutions helping to establish this new. New what?
https://academy.binance.com/en/glossary/trustless
It is the removal of relationships so they can be replaced by something, no someone new that is bothersome. Words like usury invade reality, and a few get very wealthy as the mass spend to survive, always being driven to need more.
We have lost the ability to commune. We lost track if the responsibility to be good stewards of the garden we were given responsibility for .
https://modernconsensus.com/technology/building-digital-dollar-requires-private-sectors-help-fed-chairman/
Clearly, I am a bit behind.
Democrats cannot give up on voting reform. The nation can’t afford it.
Opinion by the Editorial Board
https://www.washingtonpost.com/opinions/2021/06/23/voting-reform-cannot-die-future-democracy-is-stake/
When I think about democracy I wonder about how long it will take to truly become democratic.
This transformation requires the agility to accept change as society moves forward and expands on all sides, Be our differences density, education, technology, automation, learning, health, family, place, or position.
The Supreme Court’s Van Buren decision earlier this month aimed to clarify the ambiguous meaning of “exceeding authorized access” in the Computer Fraud and Abuse Act, the federal computer crime law.
In the context of protecting critical infrastructure from hackers, this particular ruling will define how we manage, report, and handle unauthorized access.
It also raises some foundational questions that, if weighed carefully, have the potential to foster a collaborative relationship between researchers and companies. How should good-faith researchers conduct themselves? Does this redefine the relationship between companies and hackers? Is every researcher considered to be in violation of CFAA if they’ve not sought permission to access a system?
Jared L. Hubbard and Christopher Hart have followed this ruling closely and worked on amicus briefs to aid the Court in this matter. They will discuss the case and answer questions.
Follow us on Twitter and LinkedIn to stay in the loop with updates!
Copyright © 2021 Voatz. All rights reserved.
Today we seek to ensure each citizen eligible to vote can vote. Issues like location, geography, education are all elements of the values we must embrace as we work to assure the citizens ability to vote.
The first question of voter and eligibility takes us into the realm of who or how elections are managed. Candidates, contests, question are all elements of what is presented to the voter as a ballot. According to practices and rules, contests involve selecting candidates. While questions focus on yes/no answers or a score.
Anonymity creates a need to construct a mechanism to assure one vote per voter while preserving the privacy of the voters identity. This one requirement solved reduces the risk landscape significanttly and complicates the angle of attack.
Adhering to a security first continous improvement principles and integrating prevention and detection into the design of the source code.
I believe Voatz has solved the most challenging task and embraced best of breed components and partners to build a secure immutable record of each unique anonymously signed ballot.
The rest, as long as vendor certification mechanisms and coherent standards exist, has been done over and over again in: financial services, government services, defense, health, and retail. With sound software design and release procedures, built on quality principles inherent in the companies ethos
All we need is the right to improve democracy.
How can any tribe claim to be chosen? When so many other cultures and tribes emerged in other parts of the globe. Each grew up with an understanding of the unimaginable Creator. God, by whatever name.
This elemental craving to be better than another goes back to the emergence of language. When we learned to communicate with together we began to wonder: how or why?
These two questions get more complicated when we wonder how those lights appear in the night sky or why the rain does not soak the earth.
Yet up against the Mediterranean this band of escaped Egyptian slaves claim lands from the inhabitants.
A long time ago out of Northeastern Africa Homosapien emerged.
Homo sapien an interesting evolution of the primate. They settled in tribal communities. Evolved and seeking shelter, food source, drinking water, and sanitation together.
A new world order seems to be the next step in man and woman’s evolution. Division twin tribes, cultures, people and religion create animosity. It is this animosity built on fear often times we we must address as we evolve.
Where would I live if both ice caps melted and all glaciers disappeared. How much water did you put on the Earth? Somewhere on what will become Eastern seaboard is where Philip wants to build, I’m home.
The next question, when does it matter. If I think of myself 2050 I would be 96. If I think beyond, 21 sounds like a good number.
Distributed autonomous organizations, a DAO.
When we think of governance and how we control society, we immediately must consider the realities of people in the tribes they belong to.
Recently the emergence of bitcoin, the understanding of the power of a distributed ledger, the use of a hash chain, the power of cryptographic processes, and the security of the devices we carry establishes a foundation for a brave new world.
What is governance? It is the method processes and mechanisms a society puts in place to establish order and ensure harmony?
The ancient Turks, Greeks, slave spoke of democracy, the idea that each member of the tribe, the town, the city, or the state could assemble and determine new laws, regulations, and best practices. We then evolved into Republican governments the concept of a group of people representing a larger number of citizens.
Influence and power define what shall evolve. In my lifetime, the idea of being able to plug the handset of your telephone into the back of a terminal and establish a connection to a computer somewhere out there was a novelty. For my father it is Time in Geneva when Aryanism stood out as a challenge, opportunity or threat. Telephones were just emerging and radios were available. TV was still not present. Paper books and libraries surrounded the environment we will call Geneva.
City on the Lake, what is this thing place in his history his is as relevant as your or mine.
One question why anonymity at the profound process of engagement. When you are something called anonymous I am not sure I want to play. If your anonymous is mandatory; I don’t want to play.
The innovative spiritual and the. Nurturing essence of life.. How this evolves involves countless engagements.
Each sublime note to the fabric of the virtual environment we present to the public is.
And, all of us form the fabric of the public.
He answered them, “And why do you break the commandment of God for the sake of your tradition? 4 For God said,* ‘Honor your father and your mother,’ and, ‘Whoever speaks evil of father or mother must surely die.’ 5 But you say that whoever tells father or mother, ‘Whatever support you might have had from me is given to God,’* then that person need not honor the father.* 6 So, for the sake of your tradition, you make void the word* of God. 7 You hypocrites! Isaiah prophesied rightly about you when he said:
8 ‘This people honors me with their lips,
but their hearts are far from me;
9 in vain do they worship me,
teaching human precepts as doctrines
“Listen and understand: 11 it is not what goes into the mouth that defiles a person, but it is what comes out of the mouth that defiles.”
What shall we do? Simple honor the one Jesus answered, “The first is, ‘Hear, O Israel: the Lord our God, the Lord is one; 30 you shall love the Lord your God with all your heart, and with all your soul, and with all your mind, and with all your strength.’ 31
You commit to what you believe in with a robust desire to adhere to the moral imperatives. The one God is the same God written about in so many different ancient lore.
Anyone you engage in an event. An event is is anything we all seek to record. By the way any unit of one can record as long as all parties are aware. It is our contracts and promises. Those such as payment, voting, identity and influence.
See you next time.
When we think of investing in various businesses the goal, of course, is revenue. One of the keys to such success is loyalty. Loyalty is all about the relationship companies create with their customers and the revenue these relationships assure.
If the buyer has something the seller wants, in exchange for the good or service they desire, then a transaction occurs. The challenge is simple, each party defines the value of what they are providing or exchanging and presto the trade occurs.
When society grows and the complexity of what each of us produces and when our needs are not aligned to this process called barter, a means of monetization is established. Society creates a trusted means of exchange – pebbles, coins, money, a promissory note or now even, some would argue, cryptocurrencies.
In other words, society created an answer to enable the exchange of goods and services between parties, who do not have the goods and services the other party seeks.
With cash, coins or other tangible representations of value, commerce is easy. When society does not develop a secure and trusted means of facilitating the exchange of things commerce, innovation and a good life cannot be achieved. To this end, paper money is imbued with ‘value’ based on the integrity of the party issuing the physical or now electronic ‘money’. The addition of the word ‘electronic’ brings technology, computers, and networks into the conversation. One network, typically referred to as the Automated Clearing House ‘ACH’ allows banks to electronic instruct the movement of ‘money from an account at one bank to an account at another.
The addition of the word ‘electronic’ brings technology, computers, and networks into the conversation. One network, typically referred to as the Automated Clearing House ‘ACH’ allows banks to electronic instruct the movement of ‘money from an account at one bank to an account at another. The use of an ach check processing system for business transactions between vendors and customers has become increasingly common in addition to banks. The advantage of this system is that it usually allows businesses to transfer money automatically between bank accounts so that their payments can be cleared out in a short period of time.
In the 1958 Bank of America created Visa Inc., in 1964 the Wallenberg family created Eurocard, and then in 1966 a collection of banks banded together to create the Interbank Card Association, Mastercharge and now MasterCard.
These payment networks, by necessity, add complexity. They create the need to establish a two sided market. On one side the relationship with the buyer, consumer, or cardholder. On the other side if this market the seller, merchant, or retailer.
Issuance and Acceptance. Two words to describe the two sides of a network. It’s only when the two sides of the market have sufficient participants. Only at the tipping point, when critical mass exists, can one claim to have created a self-sustaining network. A network of people promoting use to buyers and a network of merchants willing to accept payment based on the terms and conditions defined by the network. Beginning at this tipping point, the network and it’s Brand blossoms. If either side of the market does not achieve critical mass, the network collapses.
Any two entities familiar and trusting in the Brand, or each other, can easily establish a temporary relationship with entities associated with the brand. If one or more of the entities require anonymity increases the level of trust and recognition the Brand must establish with these participants.
In a digital environment, we are in need of mechanisms to share and establish trust across trillions of electrons. The two sides of a relationship, in other words, the market, will not take the time to understand or appreciate the need for network and endpoint security; until the risk exceeds a threshold understood by the participants.
When a mutually trusted set of parties gives the citizen, consumer, employee or courtier a letter, card, device or any uniquely registered object, and provides every acceptor with a reader capable of recognizing the trusted thing. Then the two parties are in a position to establish “trust”. The consumer has a thing which is recognized and trusted by the acceptor. This is often referred to as “What You Have”.
Once the thing is recognized by the acceptor, then, the process of identification and authorizations (the transaction) can take place. The object – the artifact – carries an identifier. It possesses unique characteristics. The object also possesses a means of assuring the acceptor the presentation of that identifier represents a unique representation of that identifier.
The simplest artifact of establishing “trust” is a handheld thing, be it a key, fob, card, watch, pendant, phone, earpiece. It does not matter what it is, all that counts is that the merchant recognizes it and that the consumer is willing to carry and present it.
Trust, for the merchant, means they can, according to defined procedures, recognize and authenticate the thing. They are then in a position to pursue a temporary and trusted relationship. What can be achieved during the time the relationship of trusted is bounded, is constrained by an additional layer. In this layer the consumer, the acceptor and any third parties address which the rights and privileges are to be granted or pursued. This is when the exchange, sale, conversation, tranaction, event or access is granted.
What is a payment card? It is the carrier of a set of credentials, A means of Identification offering financial Attributes capable of being authenticated by a party seeking to sell something to the individual or entity presenting the credential as a mechanism to assure payment.
Back when credit cards were designed, the goal was to offer merchants a guarantee of payment and anonymous consumers a means of paying. Behind this means of payment, a financial institution, the issuer, provides the consumer with a “Line of Credit”.
On the merchant side, another financial institution buys these guaranteed receivables from the merchant and charges the merchant a “merchant discount”. Later that day the Issuing Institution advances payment to the Acquiring Institution based on an agreed set of terms and operating rules. Terms and conditions the involved financial institutions collectively agreed upon.
For this method of payment to be effective, a large number of consumers and merchants had to agree to participate; hence the financial institutions came together and formed what we now know as MasterCard and Visa.
Given the state of technology at the time it was essential this new mechanism work without the burden and expense associated with the merchant, supported by the acquirer, contacting the issuer to receive approval, or, in stronger terms be assured of a guarantee of payment. To achieve this result, the merchant needed something to acquire the necessary information to submit a request for payment. For both the merchants and financial institutions,, there had to be a means of authentication. Designed to assure the responsible parties of the authenticity of the person or entity to present their payment credentials.
 To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
To accomplish this goal, just like with money, physical security features are integrated into the payment card designed to allow the merchant to authenticate the uniqueness of the card carrying the payment credential, thus assuring the merchant of the authenticity of the card.
Overtime criminals successfully counterfeited these security features.
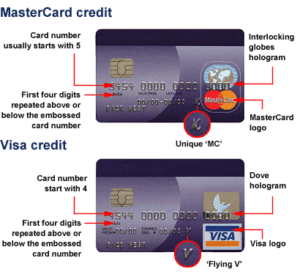
As these features were compromised additional features had to be added.
Today, a computer has been embedded inside the card, in order to assure the authenticity of the payment card credentials being presented to the merchant.
These computers embedded onto the front of a payment card exploit the power of cryptography. Cryptographic certificates and digital signatures are created by and for these computers, allowing:
These two mechanisms prove to the merchant and issuer that the card is unique and the data, credentials, and digital signature it contains or produces are authentic.
As these features become redundant and the merchants embrace Near Field Communications, based on the ISO 14443 standard, the issuer can replace the card form factor with anything equipped with the necessary computational capabilities and ability to communicate with the terminal over the NFC interface.
This is exactly what Apple Pay and Google Pay have done. They replaced the card with a device. Yes, the Payment Card may become redundant. But, the Payment Credentials they contain, remain.
What we know as card payments, is fundamentally an account-based solution. Money, through the defined settlement process, ultimately move from the line of credit or deposit account of the buyer, through a series of accounts with the participating financial institutions, to the account of the merchant.
When we listen to the news, we must think first of the bias of the reporter. This unfortunate truth is troubling in a world where the United States leader speaks of fake news and uses Twitter to stir up the masses. This body of citizens struggles with truth and is easily bent to believe what the leader says.
This particular charismatic leader, like many others in the past, can cause people to believe anything. The challenge, these same people will follow both those with high morals and those without.
Jesus Christ, Siddhartha Gautama, Confucius, Laozi, and a few others spoke wisely and became spiritual leaders many continue to follow.
To name one well remembered, Hitler, like the recent President of this great country, spread lies, and fermented hatred.
How can we rise above when so many are unwilling or unable to see the truth. We must rise above the madness these charismatic immoral individuals ferment.
That is the concern I have felt since first I looked upon the control a church exerts upon the mass.
What is a certificate? A certificate as defined by Merriam Webster
certificate noun
1: a document containing a certified statement especially as to the truth of something
specifically: a document certifying that one has fulfilled the requirements of and may practice in a field2: something serving the same end as a certificate
3: a document evidencing ownership or debt
certificate verb
: to testify to or authorize by a certificate
When we designed the EMV specification we employed a cryptographic mechanism to assure the merchant and ultimately the issuer of the presence of a uniquely issued payment card. The goal, address the weakness of the security features then present on a physical payment card.
For the merchant – a local mechanism capable of allowing the device – the point of sale to attest to the membership of that card to the family of cards issued under one of the Payment Network brands.
For the Issuer – a mechanism where the card signed transaction details the merchant would forward a digital certificate – the cryptogram – to the issuer for authentication. This cryptogram included in the message sent to the issuer assured the issuer, the card they issued; was presented to the merchant as a means of payment, for the transaction.
What is a payment card? – It is a certificate, issued by a financial institution, designed to guarantee the merchant will be paid – if they follow the agreed payment brand rules.
What is a ticket? – It is a certificate, issued by the movie theater, or a designated vendor, granting access to some venue or event.
What is a license? – It is a certificate, issued by some authority identifying your right to be or the ability to do something.
In the digital world, certificates are strings of characters, such as 2FG%4T678&b23, created, using some mechanism, by an Authority. The readers, of these characters, use the certificate to Authenticate the uniqueness and Authority associated with the presentation of this certificate by someone or thing to something or someone.
Today I read an article on LinkedIn
‘Identification’ is to give an answer to the question of ‘Who is he/she?’, while ‘Authentication’ is to answer ‘Is he/she the person who he/she claims to be?’
This distinction for me is clear. Yet, based on this article, and personal observation, people do not appreciate the unique difference between these two words.
For those who remember the film War Games, the two young adults were able to access the game simply by learning tidbits about the author of the program. “Joshua” is the critical fact our young hackers unveiled. This single word was both the identifier and the password. A simplistic form of Identification which some may confuse with Authentication.
Our driver’s license number, credit card numbers, passport number, social security number, employee number, email address or other aliases; are identifiers. These values are and should have remained, simple means of linking someone to the person who initially registered on a web site.
We then link these identifiers to a means of Authentication, an Authenticator. We then use the authenticator combined with the identifier to assure Identification. The recent NIST 800-63 standard defines the strength of an Authenticator. The simple reality the authenticator can be a combination of things you know, things you have, and things you are. Combining these factors create different strengths of Authentication.
Back in the day, a password, if properly constructed, was a very strong means of authentication. Unfortunately remembering numerous and unique passwords is unmanageable.
One of the issues we face is how so many entities, companies, and other enterprises have taken the identifier and allowed it to also become a means of Identification, a secret.
As soon as a simple number or string of letters designed as public information, to be shared with others; became a means of Identification we created an untenable situation.
https://www.nytimes.com/interactive/2019/opinion/internet-privacy-project.html
https://www.nytimes.com/interactive/2019/12/19/opinion/location-tracking-cell-phone.html
As a technologist, the revelation of what is available did not surprise me. I understood how location can easily be captured from all of the electronic devices I use. Be it the GPS chip, the triangulation of Cell Towers or the IP address of the router I am using to access the Internet. Where I am is easily acquired by any application or server I am employing.
What bothered me is that “We the People” have not pushed our governments to regulate the capture and use of this very personal information and data. What bothers me is that most of the citizens of this country or this world do not take the time to read the terms and conditions or the privacy statements provided to us and so often simply consented to them without a thought. And, if they did read them, most of us would not appreciate the language and therefore the meaning of these legal documents.
The surveillance state is real. Marketing companies, employers and so many others are buying the data and using it to improve their delivery of services, advertisements and so much more.
https://www.linkedin.com/pulse/i-hope-we-all-understand-data-collected-each-us-philip-andreae/
Today 2019-12-12 I found my way to the following article and associated podcast.
https://www.constellationr.com/blog-news/identity-dead
Below is a flow of thought as I read and listened. to Jon Reed and linkedin.com/in/lockstep Stephen Wilson discuss this most interesting topic.
We need to evolve through the pony express stage of data management, and get to a point where there are responsible data intermediaries who are being held to account.
Identity management, for me, is about proving things about myself. I want to log onto a bank and prove that I have a particular bank account. Sometimes I want to log on and prove that I am the controller of a multi-party bank account with my wife. And sometimes I want to log onto a health service and prove my health identity. So this is all about proving things about me in different contexts.
In the podcast, they beg the question “Why is the Digital Identity problem still any issue”? This leads one to think about the scale and expectation so many have surrounding this idea of “DIgital Identity”!
They then go on to ask the question What is two-factor authentication and remind us that our phone is a two-factor device, exactly what the standards FIDO Alliance worked to develop. They remind us of the reality that people look after their phones. We know when our phone is not with us.
Why not simply bind my identity to my phone.
Mr. Wilson sees the phone as the second factor. I would suggest our devices, bond to our identity, is the primary factor.
Mr. Wilson reminds us that Identity is all about Verifying Claims. We claim to be someone and the relying party seeks to confirm that I am who I claim to be. Or, when I seek to log back into a website, the relying party needs to make sure it is I – the same person who the relying party originally proofed, registered and agreed on an identifier and an associated means of authentication.
Attributes are more interesting than Identity
Attributes are what matters in the various relationships we have when we interact with another. As we think about our data we need to think seriously about what other parties need to know about us and what we wish to share with them. Efforts in Europe to institute GDPR and the efforts in California to implement CCPA
As I continued to read and follow the thread I ended up at a W3C working group working on “Verifiable Claims” and found the following:
Abstract
We are expecting people to be better than smarter than the crooks. This is an interesting thought that begs the question.
How does each of us keep up with all of the various products, standards, specifications and other efforts to develop stuff capable of securing our “IDENTITY”?
I am a firm believer in the work the FIDO ALLIANCE and W3C’s work on Web Authentication and recommend its adoption and use based on authenticators capable of adhering to a level of security certification commensurate with the associated risk of the acts, transactions, information, and services offered by the relying party to the user.